Oregon Sports Medicine was added to 8Base’s leak site today. No files or filetree was offered as any proof of claims, but the threat actors claim that they acquired:
Invoice
Receipts
Accounting documents
Personal data
Certificates
Employment contracts
A huge amount of confidential information
Confidentiality agreements
Personal files of patients
Another
The listing indicates that the data were downloaded today and will be published on August 13 (presumably if there is no payment by then).
DataBreaches sent an inquiry to Oregon Sports Medicine seeking confirmation or denial of the claims and additional information but no reply was received.
SOCRadar has a recent article on 8Base, a group that has been around since 2022 but has seemingly become more publicly active in recent months. The Hacker News also provides coverage that includes links to a number of articles about the group.
Oregon Sports Medicine is not the first medical entity listed by 8Base. They previously claimed to have attacked Redwood Lab Services, ER of Dallas, and Smyrna Pediatrics. All three of those were allegedly attacked in or about November of 2022 and leaked in December — before 8Base had a leak site. The mega.nz links where 8Base claimed to have uploaded the entities’s data was were removed by Mega.nz for gross violation of terms of service.
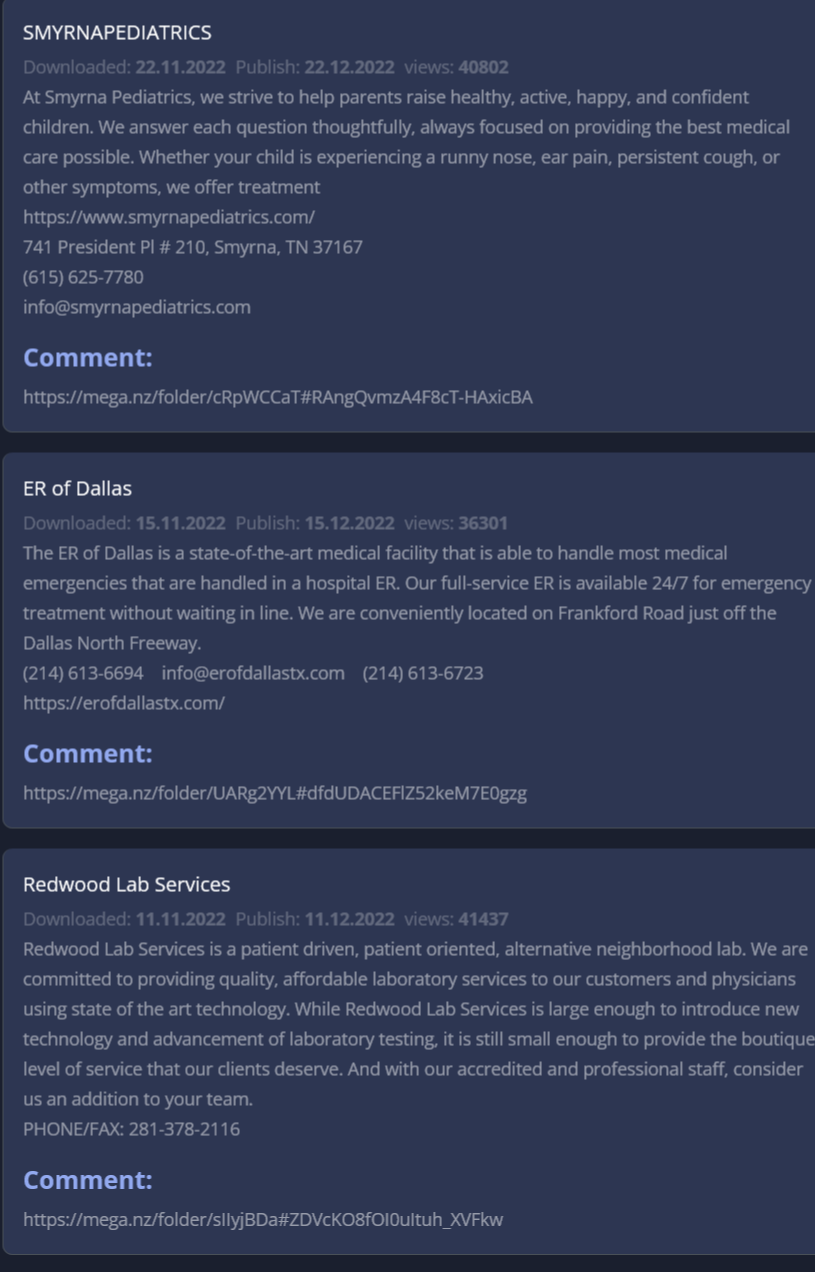
None of those three victims have any reports on HHS’s public breach tool, and DataBreaches has never seen any press release, substitute notice, or notification from any of the three. Emails or contact form inquiries were sent (again in one case) on August 6, but none of the three have responded.
In addition to the three allegedly attacked last year, 8Base also claimed to have attacked Kansas Medical Center in June of this year. KMC did not respond to an email inquiry sent July 11. On some date unknown to DataBreaches, the listing was removed from 8Base’s site.
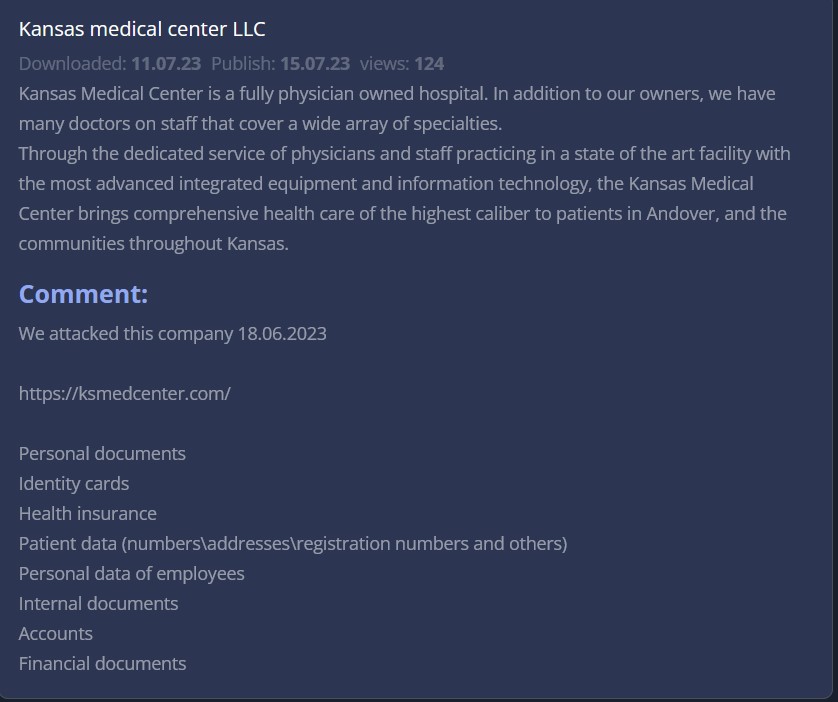
No breach report from Kansas Medical Center appears on HHS’s public breach tool, and DataBreaches has found no press release, substitute notice, or any notification by KMC. DataBreaches sent a second inquiry to KMC on August 6, but again, no reply was received.
DataBreaches reached out to 8Base to ask if they still had any data or proof from the three listings that still appear on the leak site. If they provide any evidence, or if any of the named alleged victims reply to inquiries, DataBreaches will update this post,