Some breach reports really bother me. The MilitarySingles.com situation is a case in point. Despite their denial of any breach, what I saw in the two data dumps leaves me with the nagging suspicion that they were hacked. And so I contacted them again almost two weeks ago, following their last statement, to ask to speak with them about my concerns and what I had found in analyzing some of the data. They never responded to that request or got back to me.
So after mulling this over for a while, I decided to post my concerns here. This will be a long post, so bear with me. The first part is a response to their last statement on the breach allegations. The remaining parts contain some of the data in the dumps that makes me very skeptical that their claims of fabricated data are correct.
Response to ESingle’s March 28 statement
Statements by ESingles are in blockquote; my responses/comments are italicized:
After a thorough investigation by our company programmers, it is our conclusion that our database was not hacked and that the claims of the Lulzsec group are completely false.
Why didn’t ESingles bring in an outside firm to investigate? An internal investigation may be inadequate as employees who may have made an error may be reluctant to admit any problems – or they may be unable to spot their own errors.
1. The total number of users in our database does not even closely match the number they have claimed to have exposed.
From reporting in the L.A. Times, I understand that ESingles claims 140,000 members, which is less than the 171,000 in the data dump. But is there more than one database, perhaps? The smaller data dump included a database called “cl_users.txt.” Can ESingles conclusively deny that there is any such file or database anywhere on any of their servers?
2. All user passwords in our database are encrypted and secure.
As noted by multiple sources, including this blog, the passwords in the data dump were MD-5 hashed and it was relatively easy to crack most of them. Will MilitarySingles.com/ESingles confirm or deny that it was using MD5 to hash passwords?
3. The location of the file the above user posted is in a repository directory on our website for user’s photos. The above user simply uploaded a photo of the Lulzsec group and does not mean in any way whatsoever that they were successful in actually hacking our service.
The “above user” reference was in response to this comment on a previous blog post. What ESingles claims is a fair point in terms of the image file not being adequate proof of hack by itself.
4. MilitarySingles.com was down for a few hours on March 25th due to regularly scheduled maintenance, not due to any outside activity.
Those involved never claimed they took the site down and I have no idea why ESingles keeps repeating that as if it’s relevant. The hackers’ post says, “The website http://www.militarysingles.com/ was recently closed day ago or so, so we dumped email db.” They didn’t say they closed it the site or took it down.
We have taken measure to confirm our website and it’s database is secure and safe for our members, and will continue to do so. We are unable to confirm that the so-called checklist of email addresses have actually come from our user database.
“Unable to confirm” can mean a lot of things. This would be more reassuring if you had brought in outside forensic investigators to assess the allegations. The “checklist of email addresses” refers to a comment from Dazzlepod in a previous blog entry.
Previous Question Still Unanswered
In their updated statement, ESingles did not address previous questions that had been raised by this blog:
The users in entries in the data dump correspond to the users and images posted in their “online members” photo gallery on the home page. How do they explain that?
The photo gallery was disabled shortly after breach reports appeared, so it was not possible for me to attempt further verification, but the few that I had been able to check did match the data entries. (See Update at bottom of this post for more data on this point).
A Larger Data Dump with Chat Logs Raises Additional Questions
After a commenter made me aware that there was another database dump associated with the claimed hack, I downloaded it an examined it. That dump contained 171,002 user entries plus private messages and chat logs. The most recent new user entry was from March 26.
One of the entries from March 26 involved a user with the following details (redacted by DataBreaches.net):
sabotage[xxx]@yahoo.com
IP: 74.254.113.126
Username: [FirstInitalLastName]
Full name: [FirstName LastName]
The I.P. is in North Carolina, and the hashed password decrypted to “ncarolina.”
Does ESingles really expect us to believe that hackers created an entry with an IP and then hashed a corresponding password to be consistent with that IP? Seriously?
Exploring the chat log (which is not as extensive as I would expect to see), I found what appears to be evidence that the dumped chat logs are genuine. Here is a part of a fairly innocuous chat, redacted by me to protect identities:
INSERT INTO cometchat VALUES(‘1′,’USERID1-redacted’,’USERID2-redacted’,’wow only u and are just here.. am back am so bored here at our home’,’1287161380′,’1′,’0′);
INSERT INTO cometchat VALUES(‘2′,’USERID2-redacted’,’USERID1-redacted’,’What is it like in the Philipines?’,’1287161408′,’1′,’0′);
INSERT INTO cometchat VALUES(‘3′,’USERID1-redacted’,’USERID2-redacted’,’wat do u mean?’,’1287161469′,’1′,’0′);
INSERT INTO cometchat VALUES(‘4′,’USERID1-redacted’,’USERID2-redacted’,’ah u mean the places?’,’1287161483′,’1′,’0′);
INSERT INTO cometchat VALUES(‘5′,’USERID2-redacted’,’USERID1-redacted’,’I have never been, how is it?’,’1287161511′,’1′,’0′);
INSERT INTO cometchat VALUES(‘6′,’USERID1-redacted’,’USERID2-redacted’,’the beaches island and the historical place,,,there\’s a lot of beautiful places here..
In another chat with another individual, USERID1 provided her name:
INSERT INTO cometchat VALUES(’29’,’USERID1-redacted’,’USERID3-redacted’,’hi ur looks like a filipino man.. by the way am [Name redacted] from philippines nice to see u here.. how are u?’,’1287162964′,’1′,’0′);
In a second database, cl_users.txt, USERID1 is associated with the very same name given in the chat fragment. The entry in cl_users.txt also reveals that the user is from the Philippines. It appears, then, that the two databases correspond to each other.
Does ESingles seriously expect us to believe that hackers fabricated chat logs and then fabricated user databases with information that corresponds to the chat logs?
And will ESingles confirm or deny that: (1) their logs show “INSERT INTO COMETCHAT” and that (2) during some chats, administrators pop in to say hello and ask users how they’re doing and if they’re happy with the service?
Not-so-innocuous Chats
The snippet I posted above is fairly innocuous. There were some very private chats in the data dump that could be extremely embarrassing if anyone read a chat and then looked up the corresponding userids to get the person’s e-mail address, name, location, etc. In the following chat log, I am redacting information here to protect privacy, although according to ESingles, this is all fabricated, right?
Person1: lol im up for anything except for anal lol
Person2: really? Just don\’\’t like the idea or tried it & didn\’t enjoy it?
Person1: im just not into me sticking my dick in a whole where shit comes out lol
Person2: ok. I can respect that.
Person2: ‘My pussy\’s more than adequate anyway.
Person1: that it is
Person1: my dick is wanting in your adequate pussy lol
Person2: It\’s really tight.
I’ll spare you most of the rest other than to note that one person’s phone number, provided to the other, began with area code 870.
Here’s a bit more of the chat:
Person1: but this weekendi wont be able to this weekend is my drill weekend
Person1: so what do you like to do for fun
Person2: I love taking my camera out to the forest or the park& getting shots of random plants or animals.
Person2: Or taking my nephews on adventures. We go to the Nature Center or one of my friends\’ farms
By matching the UserIDs in the chat log to the cl_users.txt database, I could find corresponding user entries with full names, e-mail addresses, and other details.
Ugh.
So, no, I am not persuaded by ESingle’s denials of breach and am calling for a fuller investigation of the alleged breach that may require bringing in an outside forensic team to investigate the situation.
And members of Congress who care about the military should be concerned as to whether soldiers’ private information has been dumped on the Internet. Our military puts their lives on the line for us. The least we can do is ensure the privacy of their online dating contacts is adequately protected or that they are notified if their data has been publicly dumped.
Update: The images on MilitarySingles.com home page are available today. This screenshot shows two users’ information: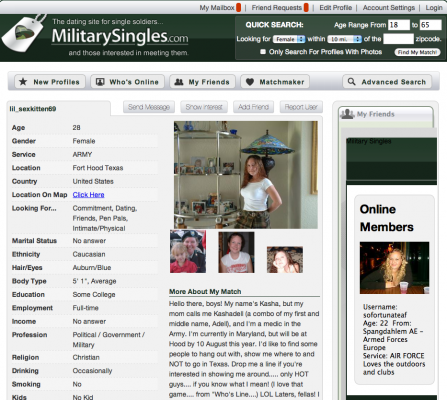
Note that the user in the left panel has a username of “lil_sexkitten69” and under her picture, she gives her name as Kasha.
Searching the cl_users.txt file – the one that ESingles claims is not their data – for “lil_sexkitten69” returns:
49863 lil_sexkitten69@[redacted] 2005-07-02 22:24:31 69.173.26.139 US United States Buffalo 2004-09-12 20:23:04 0000-00-00 00:00:00 2005-07-02 22:31:02 /esvon/pm.php Y 0000-00-00 00:00:00 lil_sexkitten69 Kasha [Last Name Redacted] 19 5 5 0000-00-00 00:00:00 0 guest 0 1a38b74ca39b2af7acea418d0c312358 0
Now look at the Members Online photo on the right. It depicts “sofortunateaf” from Germany, right?
Searching the cl_users.txt file for “sofortunateaf” returns:
146779 sofortunateaf@[redacted] 2010-10-07 09:18:48 80.154.29.93 DE Germany Kabel 2010-09-26 05:05:26 2010-12-26 06:26:38 0000-00-00 00:00:00 0000-00-00 00:00:00 sofortunateaf [First and Last Name Redacted] United States 0 5 5 5 0000-00-00 00:00:00 0 Mr. 0 guest 0 81363bcb7b38d296ad9fe3725e7cf3f7 1286468490
Both women’s hashed passwords were easy to decrypt.
So yes, I’m calling bullsh*t on ESingle’s claims that they weren’t hacked. If you think the data aren’t convincing, please tell me why.
In digging into this breach a bit more, I just discovered that MilitarySingles.com domain name is up for auction. According to one site, it was put up for auction on March 22nd, presumably a few days before the hack. Would the site name being associated with a major privacy breach have any impact on its sale price? I don’t know, and I don’t know if the attempt to sell the domain name is in any way influencing ESingle’s response to this incident. I certainly hope it isn’t.
I am still laughing at militarysingles denial. Keep pushing them till they admit it’s true!
If anyone who was in (or – and I hope this isn’t the case – is still in) their database has any screenshots as proof, I’d love to see them.
They aren’t asking much for an opening bid, ninety-nine cents?. Its ALEXA rating is pretty high for a site thats supposedly has thousands of users.
Humm wonder what the actual staffing, in numbers is, and if they know about the potential sale of the company? I mean, if your working for a company, and the place is sold, doesn’t that mean the rug is pulled out from under your feet when it comes to paychecks?
I wonder if they know their goose is cooked, and by dumping the website onto some one elses’ lap, they seemingly can get rid of a potential nightmare.
This doesnt look like the best website to sell domain names. I know there is a 3rd party connected with NetworkSolutions.com, Register.com, GoDaddy.com all would have probably brought more bids and exposure. I wonder if they site, in its form is an “as is, where is” clause, and if they “winner” of the site becomes a big loser and a knock on the door from the Feds, eventually.
It’s also listed for sale on Sedo, linked from both domaintools.com and domainwhoisinfo.com