Update: Post-publication, the Virtue Center web site was taken offline and has not returned as of December 23. An undated entry on another site lists Shakil Islam and Faizan Sattar as “former employers” of VC. At the time of publication, however, they were listed on VC’s web site as part of their team. Follow-up e-mail to Ryan Mahoney with questions about the incident and their storage of credit card data did not result in any response. None of their clients contacted by DataBreaches.net responded to requests for comments on the incident.
Virtue Center for Art & Technology is a New York-based software company that designs and develops web applications, websites and mobile apps. VirtueCenter is managed by Ryan Mahoney, Shakil Islam, and Faizan Sattar, and they pride themselves on their social responsibility and support for clients, many of whom are involved in promoting Muslim or anti-islamophoic causes:
If there were such a thing as a boutique firm that caters to not-for-profits, Virtue Center would be it.
Sure, we know about technology. We can wrap our heads around complex marketing concepts. We’ve got skills. But what sets up apart from the herd is our unique perspective when it comes to prospecting clients.
What we are is small group of like-minded individuals with a common purpose: to use our unique skill sets to help the organizations and individuals most poised to make a positive impact on the world.
An admirable goal, to be sure. But as researcher Chris Vickery uncovered and shared with DataBreaches.net, their skills don’t seem to extend to industry standards for retaining and securing payment card information.
One of the applications they provide is a donation processing and management system. “Manage your money,” they proclaim:
Accepting online donations is easy, fast and safe with a payment module integrated with your site
Recurring/monthly payments are processed automatically
Keep track of your funding with printable reports, highlighting top donors and other aggregate information
Track pledges, follow up, and convert them to real donations
And then there’s reassuring locked symbol with an assurance:
Safe And Secure Payment.
Virtue Center’s donation platform is 100% secure and fully integrated into the site – no redirection to PayPal or other third party sites. Both your donor and you can rest at ease about the safety of contribution.
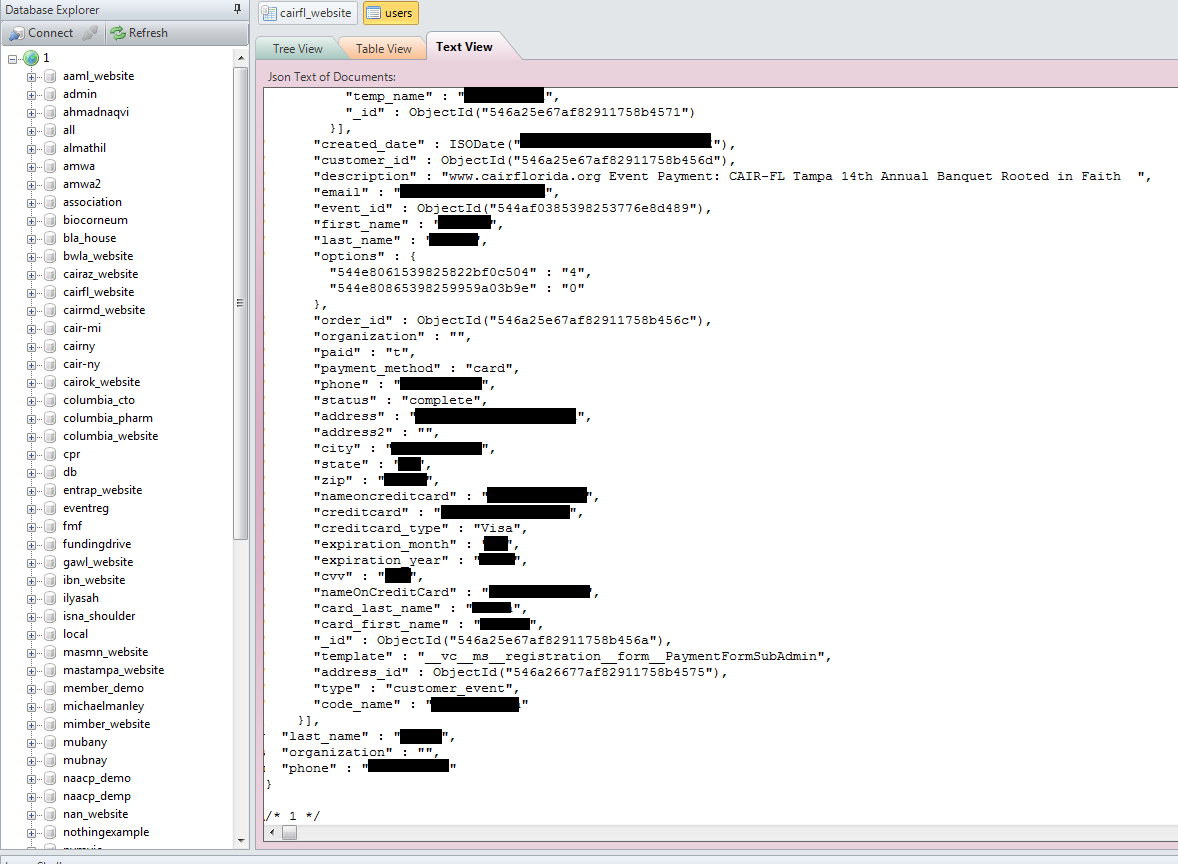
Not quite. Their MongoDB Database installation was leaking on Port 27017 (as so many others have leaked), and of concern, it appears it was storing names, addresses, telephone numbers, and credit card number with expiration date and CVV code – all in plain text.
Failing to comply with PCI-DSS is serious enough. But when your company is a service provider to organizations that are politically sensitive, it’s even more concerning. The directory revealed they provided web site or other services to a number of chapters of the Council on American-Islamic Relations (CAIR) and Muslim American Society (MAS), as well as the Islamic Broadcasting Network and Muslim Bar Association of New York. Virtue Center also provided services for the NAACP and a clinical trial program at Columbia University, as well as the Georgia Association for Women Lawyers (GAWL), American Muslim Women’s Association, and other organizations:

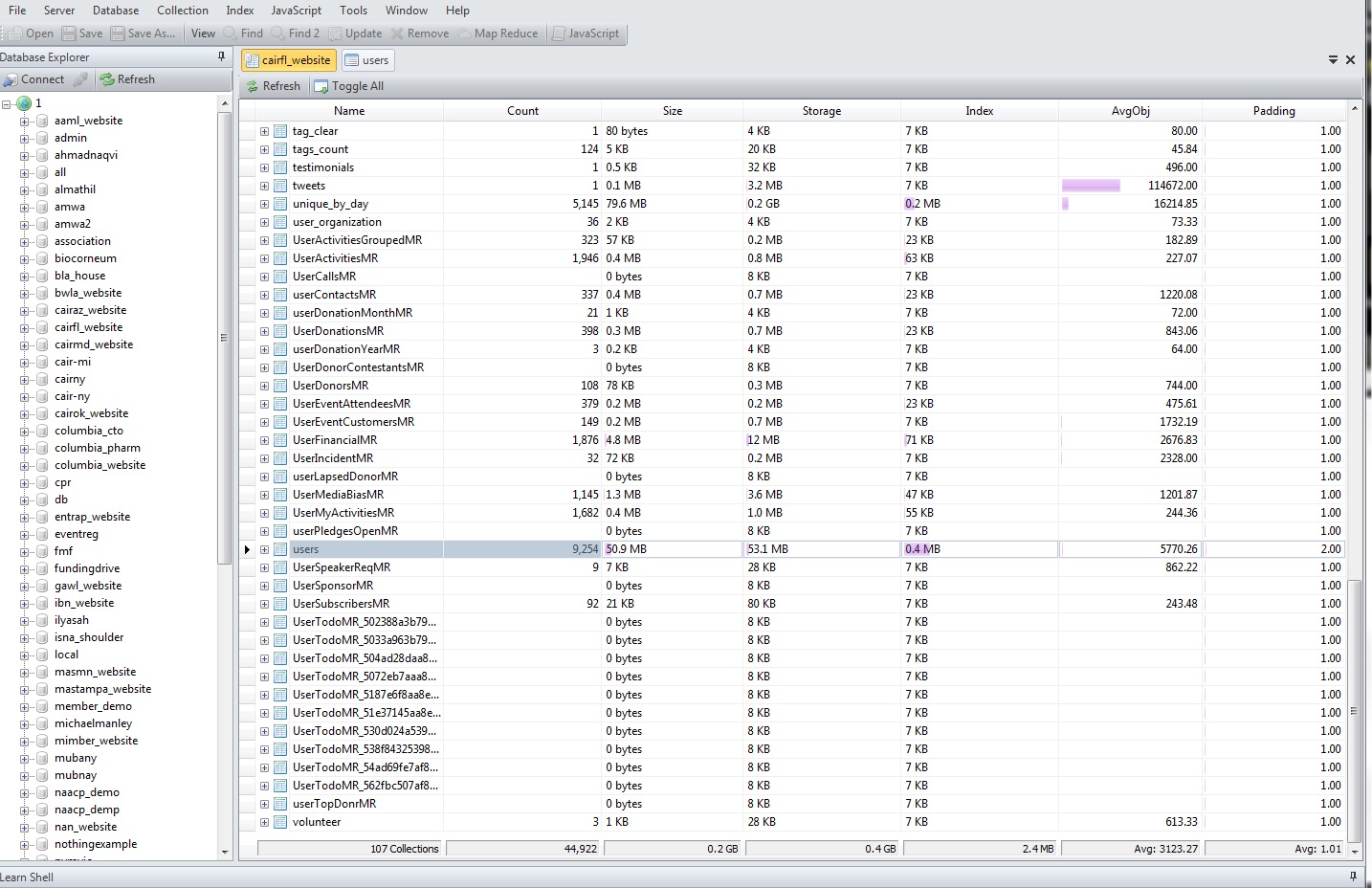
Not all of these clients had credit card information stored in the leaky database, but there was credit card data stored for the Florida chapter of CAIR, who had information on over 9,000 users in its records:
Those attending events at, or donating to, CAIR in Maryland, Michigan, New York, and Oklahoma also had credit card data stored in clear text with their full name, address, card number, expiration date, CVV code, and phone number exposed.
Many of the credit card numbers in the leaky database appear to be unexpired card numbers.
On December 15, Vickery first attempted to notify card issuers to alert them to the breach, but got no prompt response from two of the issuers and couldn’t find contact emails for the other two. He then sent emails to all of the impacted chapters of CAIR, at least one of whom contacted Virtue Center, who contacted their ISP to block access to the database until they could sort out the problem. DataBreaches.net also reached out to the Georgia Association for Women Lawyers today to alert them.
None of the CAIR chapters responded to a request sent December 15 for a statement in response to the leak.
If you’ve donated to one of the organization listed in the screencap of organizations, be aware that many of these organizations may no longer be using Virtue Center. A quick check of some sites indicates that some have switched providers and recent donations or transactions may not be through Virtue Center.
At the present time, Virtue Center’s web site is not available, and they have not responded to inquiries as to when this leak first occurred, how many people are impacted, and whether they will be providing notifications. Nor did they respond to questions as to why credit card data going back to 2013 was all stored in clear text.
This post will be updated if more information becomes available.