Over the past few months, DataBreaches.net has reported on a number of hacking incidents where the attackers demanded ransom if the victims did not want to see their data publicly dumped or put up for sale. Some of the incidents involved TheDarkOverlord, who attacked a number of clinics in the healthcare sector. Other incidents involved a self-described Russian hacker known to this site as “Return,*” who attacked a clinic, a small accounting firm, and a law firm.
As far as DataBreaches.net knows, not one of either attacker’s publicly identified victims ever paid any ransom, even though Return’s ransom demands were much more modest than TheDarkOverlord’s. Obviously, there may be entities that do pay ransom and we never hear about them, but for the cases where the hackers have made the media aware of a hack, there has been no evidence of any ransom paid as a result of any public pressure due to media coverage. Entities that are ransom-refusers may just remain ransom-refusers.
If the hackers made any money at all for their efforts, then, it was likely from the sale of personally identifiable information that could be used for fraud or medical identity theft. But by now, any dreams of easy money from a ransom demand should probably have been abandoned.
As Einstein famously, but probably didn’t, say, insanity is doing the same thing over and over again and expecting a different result. Yet both attackers are back with yet more hacks and attempts to extort their victims. Let’s start with “Return’s” latest publicly announced hack. In Part 2, we’ll cover TheDarkOverlord’s return.
In an encrypted chat on September 20, “Return” claimed that he had hacked a payroll processing firm in Grandville, Michigan, V.I. Pay, Inc. As he has done in other cases, “Return” provided a large (147 mb) sample of the data he claims to have acquired. The sample includes numerous spread sheets from named clients, files with personal and financial information, login credentials, and more. Return claimed to have acquired 13 GB of the firm’s data, and told DataBreaches.net that he had sent an emailed ransom demand for 25 BTC.
As in other attacks he had discussed with DataBreaches.net, Return also claimed that he had used social engineering to gain access to their network.
DataBreaches.net contacted V.I. Pay, who denied having received any ransom demand and who initially denied having been hacked. Their denial of any ransom demand turned out to be accurate: several days later, DataBreaches.net would learn that the emailed ransom demand to one of their listed email addresses had bounced back to Return after failure to deliver.
Unfortunately, VI Pay’s response to this site’s notification call and request for a statement turned out to be yet one more “shoot the messenger” encounter. When it became clear that they had no idea they had been hacked, I offered to send them the sample data so they could review it to see if it was their data. Steve (last name unknown to this site) refused the offer. I then started reading him names of clients whose data was in the sample, and asked him whether those were his clients. He wouldn’t answer. I did expect that once he heard the names, he’d realize that VI Pay might have a serious problem, and he would request more information or the sample of data. Instead, he refused to deny or confirm anything, said that he had no statement, and at one point, accused this journalist of being in cahoots with Return. [Apparently, because I interview hackers and they talk to me, I must be in cahoots. Good to know, and my kids can now brag that their mom’s a hacker instead of journalist following up on a report, I guess.]
DataBreaches.net subsequently emailed a handful of clients from the sample. The emails included some of their or their employees’ information and asked them to confirm or deny whether that was their information. None responded to the notifications, even though the notifications were re-sent a few days later. A search of a number of the clients’s names, however, did find companies by those names at addresses in Michigan.
The files in the sample contain a slew of personal data, such as a spreadsheet with commissions paid to a realty firm’s employees, and another spreadsheet purportedly from another firm’s 401K plan that includes 111 rows with the participants’ name, postal and email addresses, Social Security number, date of birth, amount of employee and employer contributions to the plan, and telephone number. Some of the files in the sample include information pointing to VIPay, such as logins or passwords, and there are other indications that the files were created by VIPay. One of the files in the sample, for example, seemingly for Clinton Realty, shows what appears to be VI Pay’s checking account information in a dialogue box used in preparing a tax filing for the client:
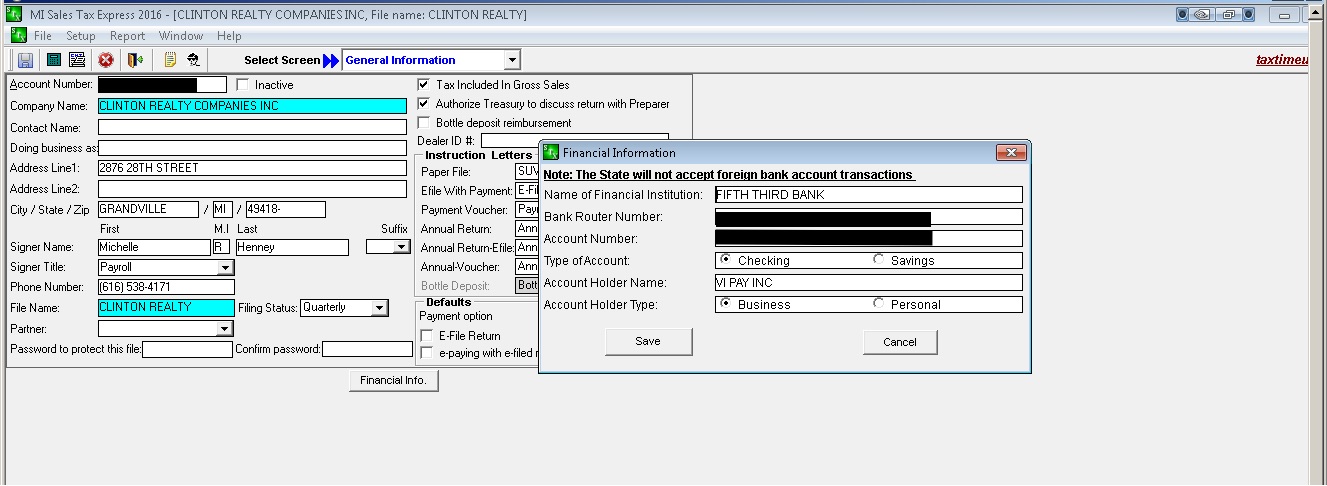
Another file revealed clients’ names, account numbers, and login credentials, as well as login credentials labeled “vipay01:”
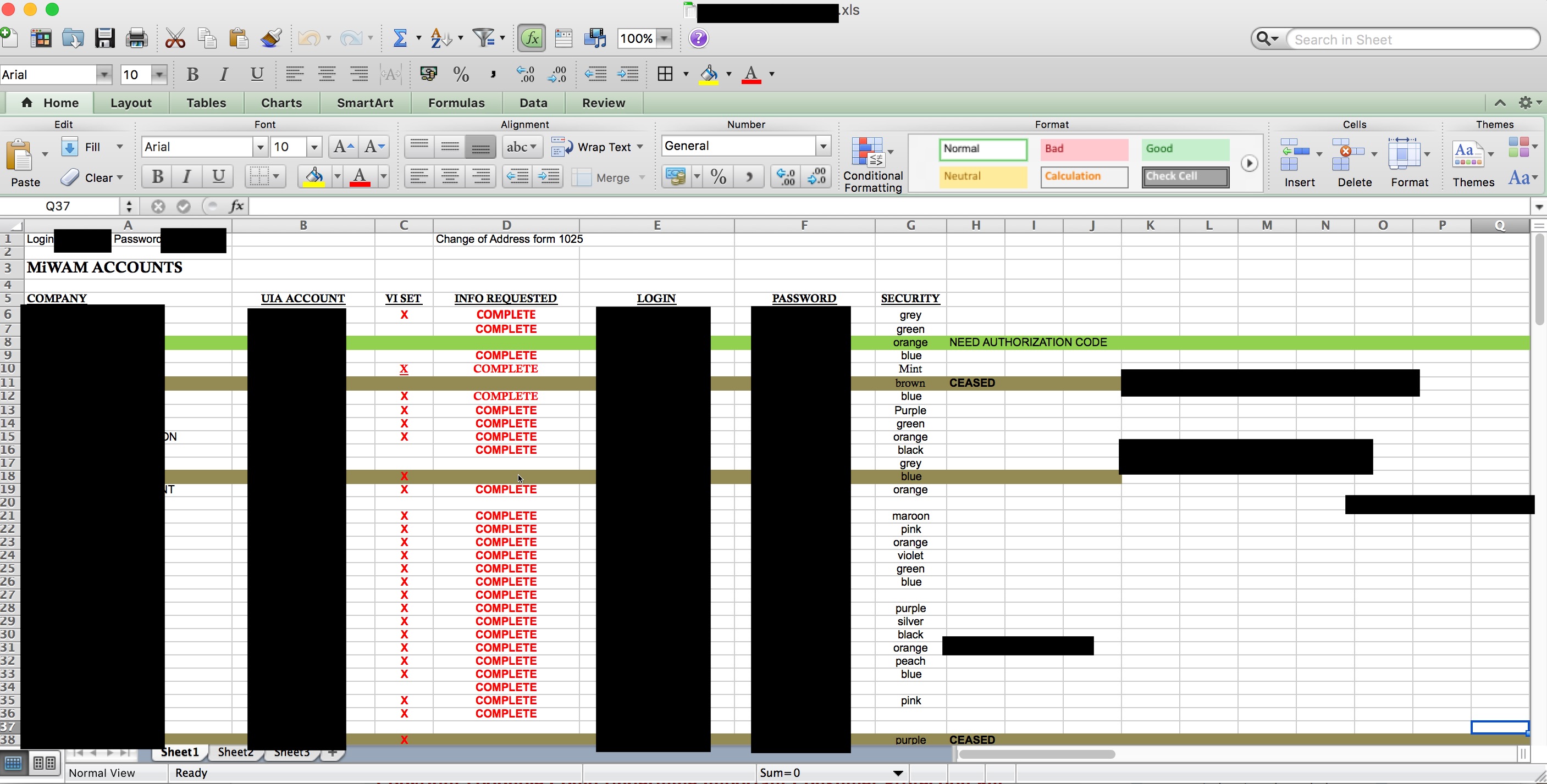
Keep in mind that this was just a few files in a sample of a much larger database.
As of today, Return informs DataBreaches.net that he has heard nothing back from VI Pay.
At the present time, it is important to reiterate that VI Pay has neither confirmed nor denied any breach, and none of the firms contacted have responded to inquiries asking them to confirm whether the information purportedly about their employees is authentic. DataBreaches.net will update this if more information becomes available.
# # #
*Note: DataBreaches.net does not know if “Return” is really a “he” or Russian, but that is the hacker’s self-description.