Over on Hot for Security, Graham Cluley beat me to the punch on reporting an insider breach involving Bupa. You can begin by watching Bupa’s public notice, and then read Graham’s report for some more information. Of note, he reports:
In all, around 108,000 international health insurance policies are said to be affected.
An email sent to affected policy holders describes that although financial and medical information was thankfully not exposed, details such as names, dates of birth, nationalities, phone numbers, email addresses, membership numbers and other administrative data was taken.
DataBreaches.net had held off on reporting this breach, but there seems no reason not to add some details to what Graham reported.
DataBreaches.net first became aware of the Bupa breach on June 23, when a listing appeared on the now-gone Alpha Bay marketplace by a vendor calling himself “MoZeal:”
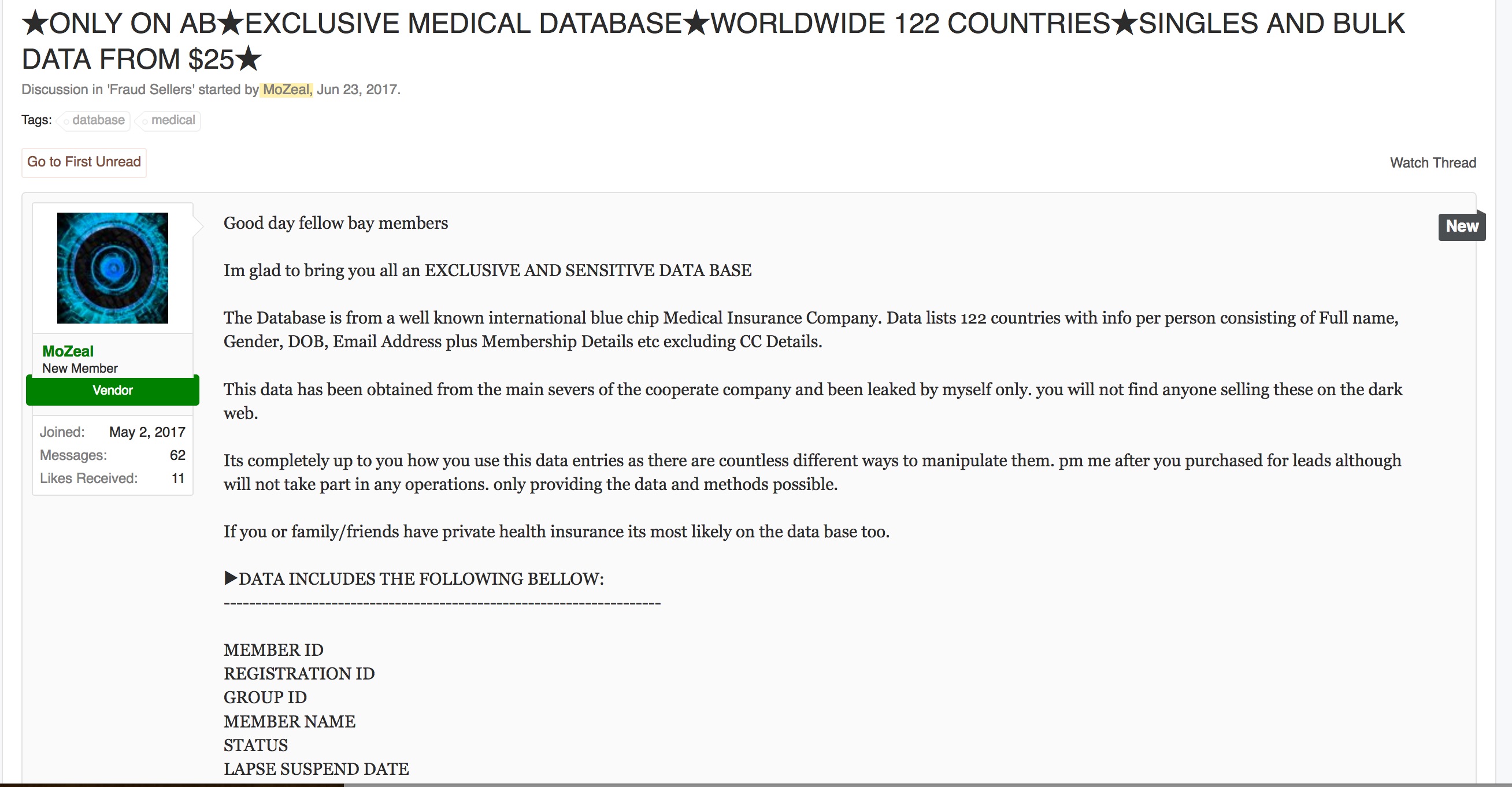

The listing, by “MoZeal,” listed the following data types were included:

It would appear that “MoZeal” is likely the rogue employee that Kenton referred to in his videotaped statement.
Also of note: while Bupa reports that 108,000 were affected, MoZeal’s listing and thread indicated that there were over 130,000 in the U.K. alone, and that overall there were about 500,000 – 1 million records for sale.
In a reply to a potential buyer about pricing, MoZeal responded:
Thanks for your inquiry bro, but before i start talking about pricing i would just like to clarify that this medical database is the only unique db if not only one on the entire dark web market with over 1million entries and over 122 countries as a whole not to mention its come straight from one of the world class health insurance companies. so you can imagine the information is very sensitive but also exclusive.
Bupa has reportedly taken legal action, so this post will be updated as more information becomes available.
Update: Bupa responded to the reported discrepancy between their numbers and the AlphaBay vendor’s claims with a statement to Insurance Business reconciling some of the differences by noting that they referred to “policies” while the vendor referred to number of individuals. Sam Boyer reports:
“All of the information and statements we have made public this week, remain valid,” it said. “We are aware of a report by Databreaches.net that suggest ‘a former employee claimed to have 1m records for sale’. Our thorough investigation established that 108,000 policies, covering 547,000 customers, had been copied and removed. The disparity in numbers claimed and those taken, relates to duplicate copies of some records.”
That would resolve the discrepancy, yes. But then they seem to be acknowledging that more than half a million people may have had their information up for sale on the darknet, which is concerning. Does anyone have the most recent version of AB before it went down to see how many sales might have been recorded and whether they were bulk sales or individual sales?