I’ve had enough. Actually, I’ve had more than enough. I should have written this post months ago.
Last week I received notice from Twitter Legal that they had been served with a grand jury subpoena for my account information. Also listed in the grand jury subpoena were four other Twitter accounts, only one of which I recognized. So why would a grand jury in Texas want my details from Twitter? And why should they be able to get them?
Suppose I told you that the only basis for them seeking my information was that someone added me to a conversation that I wasn’t in, and sent me a smiley emoji. I hadn’t replied, but that seemed to be enough for the grand jury to want to know more about me.
If it sounds outrageous to you, let me tell you that my lawyers inform me —- from a safe distance so that I don’t throw something at them — that it’s perfectly legal for grand juries to do this.
It would not be legal in the World According to Dissent. And it doesn’t really make good sense in any world, as Mike Masnick of TechDirt articulates so well in his post on this insanity.
What the Northern District of Texas and Judge Toliver have done to Justin Shafer is outrageous. This subpoena for my info is infuriating, of course, but let’s talk about Shafer, because it is his case the subpoena relates to.
Regular readers of my site will recognize Shafer’s name from his research uncovering leaking patient data and his collaboration with me in filing an FTC complaint that Henry Schein settled via a consent order and payment of a $250,000 fine to the FTC.
This blogger has been reporting on Shafer since December, 2013. On a good day, he can be impulsive, brash, obsessive-compulsive, and offensive, but that doesn’t make him a criminal nor justify repeated raids on him or treating him like a criminal. And it doesn’t justify keeping him in jail for months because he lost his temper after all of the FBI’s perceived harassment of him and his family.
Unfortunately, it appears that some entities he embarrassed by revealing their security failures tried to deflect blame by accusing him of hacking them. And it appears that the FBI agent involved may have believed them. Beginning in March, 2013, according to Shafer, Special Agent Nathan Hopp treated him like a black hat or grey hat, when all he had done was find exposed data and try to report it so patients would be notified. Entities may not like to be publicly embarrassed but there is nothing illegal in Shafer going to the media to call attention to data leaks that he uncovers.
Over the next four years, Shafer would feel repeatedly harassed by the Dallas FBI and Special Agent Nathan Hopp. And who wouldn’t feel harassed when he was repeatedly raided and there were never any criminal charges because he had never done anything illegal? The only criminal charge they ever levied was harassment after he lost his temper with Agent Hopp after years of perceived FBI harassment.
Instead of a grand jury investigating Shafer, someone should investigate why the Dallas FBI covered up or suppressed evidence that Shafer was a white hat who was trying to help them, because they certainly didn’t tell the federal court about all the help he had offered them and I doubt they ever told the grand jury about Shafer’s attempts to help, either.
So grab your favorite beverage and sit back while I show you some of the evidence that the federal court was not shown when the FBI tried to get Shafer charged with stalking an FBI agent with intent to harass or intimidate.
On March 31, 2017, in his affidavit in support of the criminal complaint alleging stalking and intent to harass or intimidate an FBI special agent and his family, Special Agent Ronnie Buentello left out important context and history for assessing Shafer’s conduct and intent, but he also indicated (Paragraphs 10 and 11 of the affidavit) that Shafer was also being investigated as a co-conspirator of the blackhats known as TheDarkOverlord. Perhaps someone thought that making Shafer out to be some criminal hacker would boost their claims that he was some kind of dangerous stalker, but the Dallas FBI had evidence to show that Shafer was actually trying to help the FBI catch TheDarkOverlord.
As part of his affidavit (obtained from PACER while it was briefly unsealed), SA Buentello stated that the FBI had found a copy of a stolen database from Missouri when they raided Shafer’s home in January, 2017. That database had allegedly been hacked by TheDarkOverlord and had been put up for sale on the dark web. The implication seemed to be that if Shafer was in possession of a database that had been hacked and put up for sale by TheDarkOverlord, then he likely was involved in the hack or was conspiring with the hackers:

What the FBI did not tell the court was that Shafer had emailed that very database to the FBI in July, 2016, telling the FBI that TheDarkOverlord gave it to him, unsolicited, duing a chat on Twitter.
So here’s “Exhibit A” for you: the email Justin Shafer sent on July 1, 2016 to this blogger and the Dallas FBI with the database the FBI would later claim supported a suspicion that he was a “co-conspirator:”
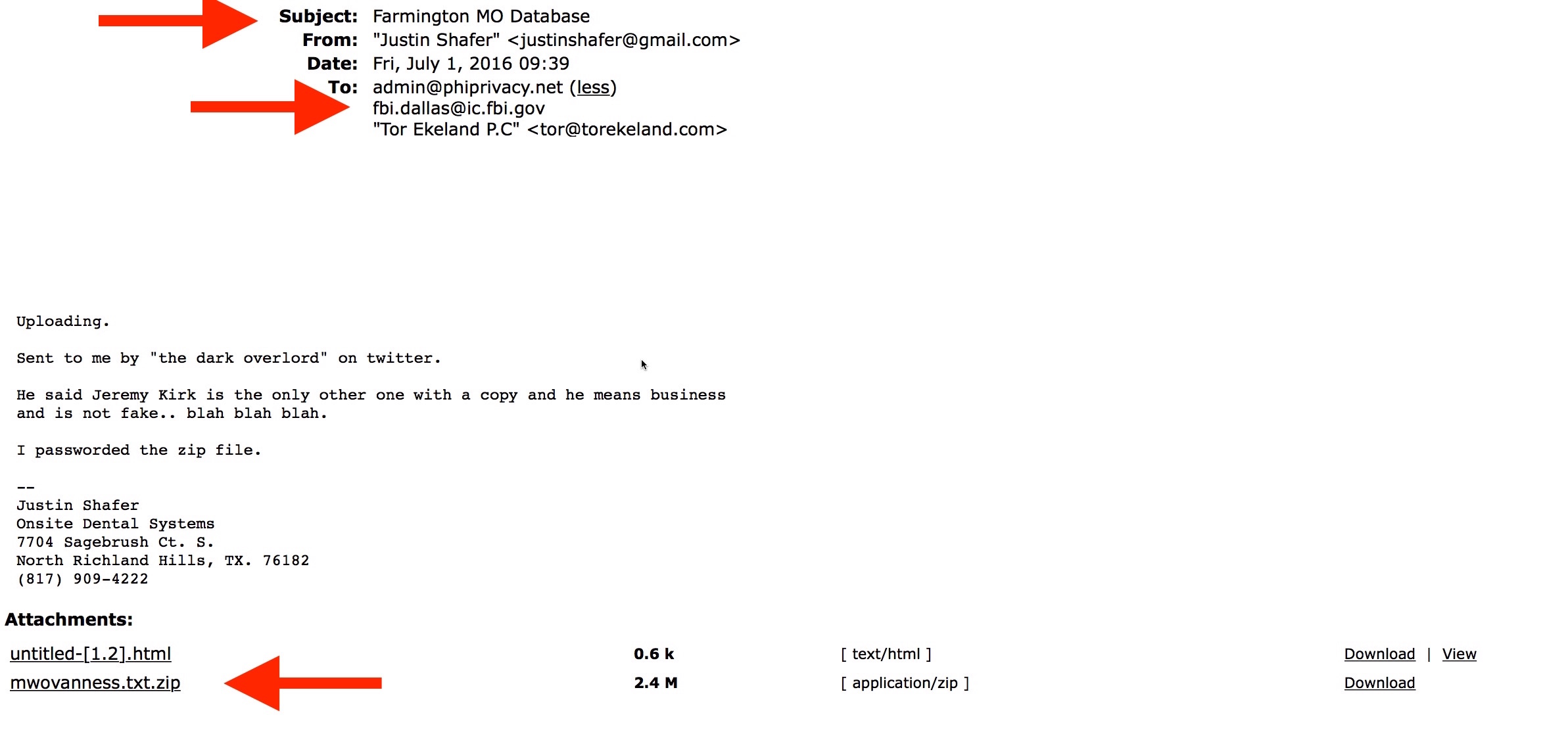
At another point, the FBI’s affidavit also claimed that during the second raid (January, 2017), the FBI found evidence of a chat session between Shafer and TheDarkOverlord:

The affidavit referred to a chat session, but did not indicate whether it was a file copy of an old chat session or a new one in progress at the time of the raid. In fact, Shafer did have a number of private (DM) conversations on Twitter with TheDarkOverlord that Shafer logged. He often reviewed the logs afterwards, looking for additional clues in the material. Shafer generally shared his logs of the chats with this blogger and with others – including the FBI.
So now view “Exhibit B:” an email Shafer sent on July 3, 2016 to an NHS unit in the U.K. to warn them that they had been hacked by TheDarkOverlord. Shafer had been told about the hack in a private conversation with TheDarkOverlord and then tried to contact the NHS so that they could secure their data and warn patients. Shafer also cc:d Dallas FBI on that email, and included part of the chat log between him and TheDarkOverlord:

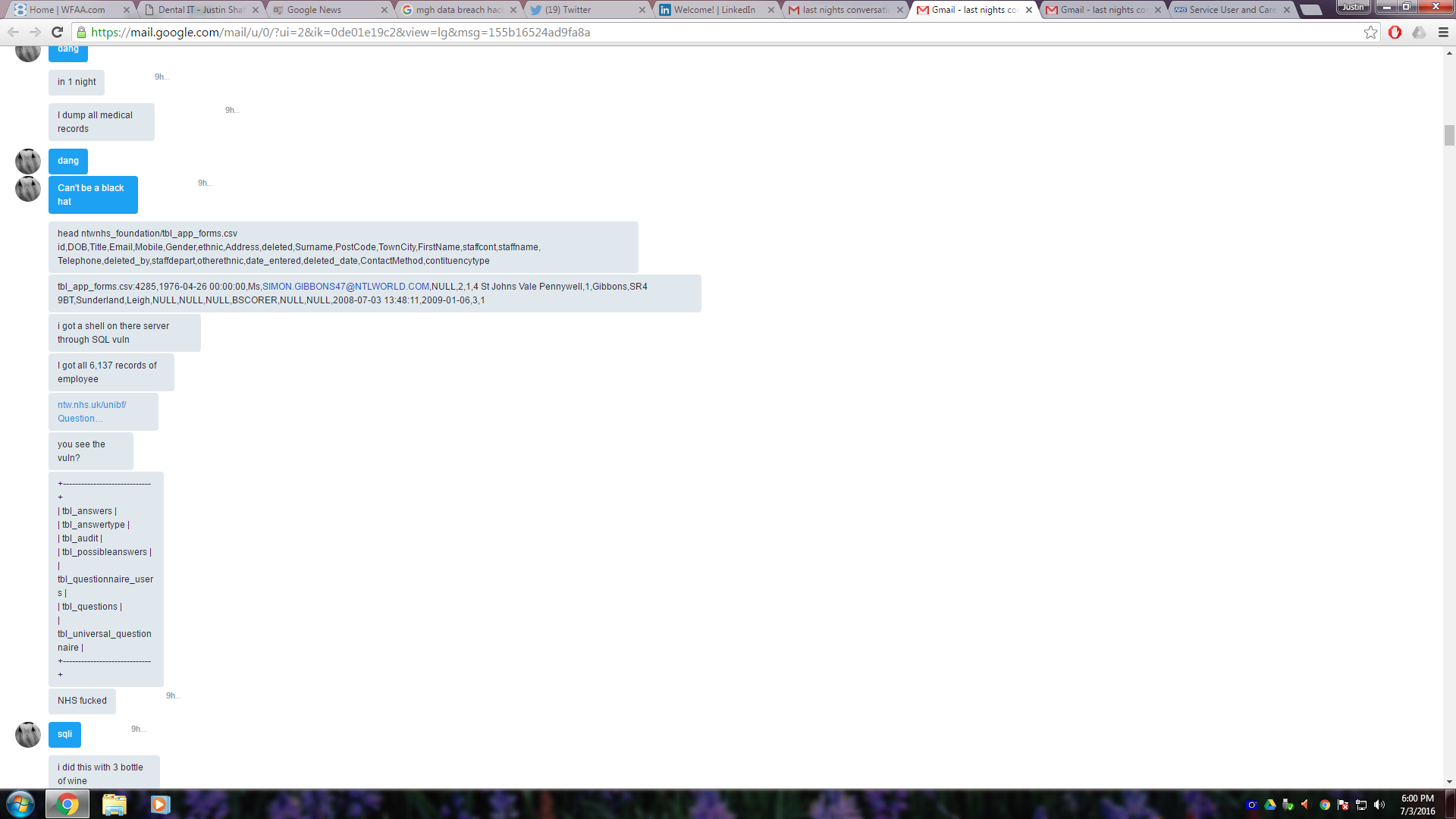
So was the presence of chat logs evidence of conspiracy? I would argue that it was actually evidence that Shafer was collecting information on TheDarkOverlord which he was then promptly sharing with law enforcement to assist them.
It seems the FBI couldn’t tell a white hat from a black hat. Or perhaps the Dallas FBI failed to share the information he was providing to them with the Atlanta and Missouri regions of the FBI and other regions investigating TheDarkOverlord. Despite TheDarkOverlord’s bizarre attempts to implicate Shafer or tease him, Shafer had always helpfully provided information to the FBI. What co-conspirator does that?
And do note that Shafer offered this help to the Dallas FBI in July, 2016 – even after they had raided him in May, 2016 and upset his children and damaged his property (he claims). He was still being a whitehat. What a shame that the Dallas FBI did not respond to him that way.
Now consider “Exhibit C:” If Shafer was a co-conspirator, why was he running around the internet trying to get TheDarkOverlord patient data dumps removed? Here’s an email from Mega.nz in February, 2017 thanking Shafer for notifying them and saying they suspended TDO’s account. It was not the first time Shafer had contacted them. And once again, Dallas FBI was cc:d.
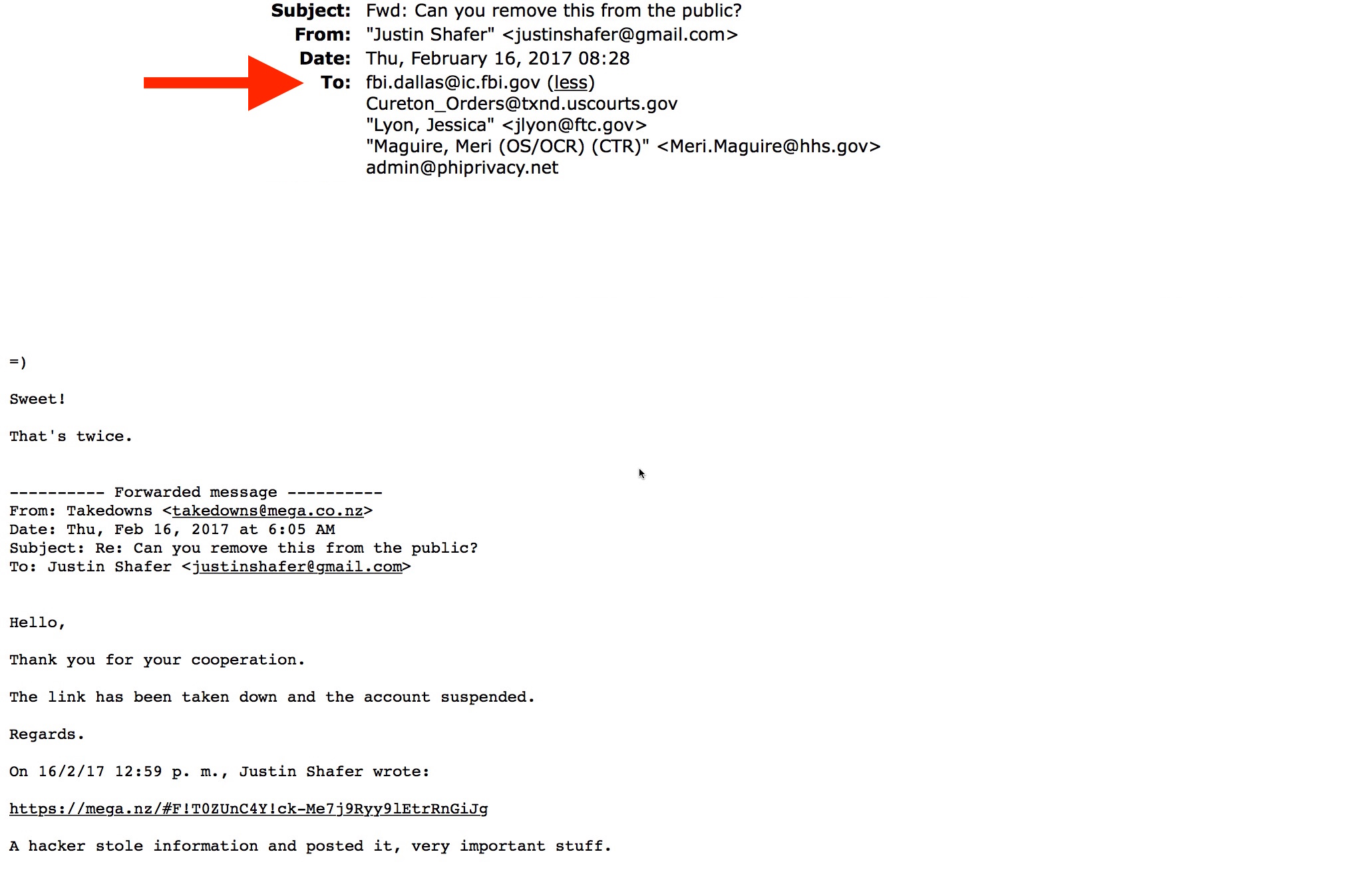
So beginning in July, 2016 and thereafter, Dallas FBI received evidence that Shafer provided to try to help them catch TheDarkOverlord. Does any of the evidence above look like someone conspiring with TheDarkOverlord or does it look like someone trying to help law enforcement catch TheDarkOverlord?
The FBI seized Shafer’s devices. They almost certainly have copies of all of the evidence cited above on his devices, plus other evidence of his attempts to help them and his complaints about Agent Hopp’s attitude towards him.
Why did the FBI withhold all of this evidence from the court? Why did they try to suggest that Shafer might be some kind of dangerous master blackhat criminal or dangerous stalker? Why didn’t they tell the court that there was history between the Special Agent and Shafer going back to 2013 that provided important context for any harassment charges? Simply noting that the agent was involved in two raids on Shafer does not even come close to telling the whole story of why Shafer might have engaged in what he may have considered verbal harass-back activities.
Shafer repeatedly tried to help law enforcement catch TheDarkOverlord. Instead of appreciating his efforts and help, DOJ has maliciously tried to keep him in jail, depriving his children of their father and his family of their income-earner. And for what? Because he got ticked off at an agent who he felt had been giving him a rough time for four years?
#FreeShafer
Update: Ken White (@Popehat), another one of us presumed “Gang of Five” also blogged about this. When it comes to this subpoena, at least I’m in good company….
While I am extremely sympathetic to Justin Shafer and I totally get he is a white hat who is trying to help secure databases and help make our cyber digital world a bit more secure, he did make some very IMPULSIVE choices in his behavior. While I do believe that Justin’s impulsive behavior was enabled by Agent Hopp and FBI intrusive and ridiculous raids, Justin still did leave some pretty threatening tweets publicly on Twitter and on Facebook. If anything, that is not helping the alleged cyber-stalking claims.
I get you are his biggest supporter to #freeshafer. At the same time, I think it is also relevant and unbiased to present ALL of the facts as did Kevin Krauss did in Dallas News, which included the tweets and FB messages. (No, I do not think those tweets and messages were illegal. However, I think he was so obsessed with fury, that he lost his train of judgment and thought as well as being violated from the raid that all rational and composure went out the window.).
https://www.dallasnews.com/news/crime/2017/06/02/computer-geek-hacker-harassed-fbi-agent-hero-trying-secure-internet
I agree with you that he was angry and impulsive and didn’t help himself with those tweets. I also agree with you that a lot of what he said/did was *legal.*
I’ve left your link to the Dallas News, but tbh, I didn’t feel the need to quote his tweets because even if you take it as a given that he tweeted inappropriately or angrily, it doesn’t alter my theses that the FBI provoked Shafer by their repeated raids that never found illegal conduct and the FBI purposefully omitted exculpatory evidence and tried to make Shafer sound like a blackhat to boost their weak stalking charge. Read their affidavit again – in track changes mode – and you’ll see the FBI/DOJ writing to each other in ways that indicate that they knew they had no real case and had to try to boost what they were claiming.
Thanks for sharing your thoughts.
He WAS at home with an ankle bracelet. He was immediately remanded into custody for publishing this post on his blog on April 14th. http://justinshafer.blogspot.com/2017/04/shake-it-off.html
We should do all we can to get this story in the media. Don’t forget to call the ADA and let them know the guy who hacked them, is know claiming to be a victim. I guess he was not a black hat when he posted the video of that hack.
I approved your comment because I really have no idea what you’re talking about, and I’d like to know.
What ADA are you claiming got hacked by Shafer? And what video are you talking about? Links, please?
I was curious about that as well. I have no idea what 3DO was talking about either.
I did a quick search to see if links came up. The only thing that looks similar is that a woman named Ada posted videos of a hacker hacking the President’s website. If that is what the reference was about, 2 different cases then.
https://www.google.com/search?ei=ZkYQWrHSHpGsjwOtpJvgCQ&q=hacker+who++hacke
For anyone who may be unsure of this case and who or who is not involved, I did a quick search to find links on others who reported this with the basic facts. Hope this is helpful for extra links if people seem confused on who he is or what this case is about.
[Note from Dissent: Links deleted. I generally do not allow links to other sites because it encourages spammers and besides, some site might wind up dropping malware on my site visitors if they get compromised down the road.]
Oh ho. NOW I know what you’re talking about. I was thinking ADA= Assistant District Attorney. And we can debate whether he was a blackhat or not when he posted that video because I think his intent was to get them to address a vulnerability that had been unaddressed for quite a while, wasn’t it?
3DO, maybe you should watch that video you reference again. See the date on it? January 17, 2011?
You see the comments Shafer types in the video? He’s directly addressing the ADA and Steve Roberts. Know who he is? He’s the vice president of Product Management at Henry Schein Practice Solutions now.
You know why his name is in the video? Because right around the same time Shafer discovered the ADA XSS flaw, he also discovered that the Dentrix credit card payment processing website, epay.dentrix.com, had a vulnerability too. Shafer was able to create himself an administrative login for the site. He took that information directly to Steve Roberts @ Dentrix and they acted on it immediately. In the same conversation, Shafer asked Steve if they had contacts at the ADA as he found a big problem with their site as well. Steve emailed another Steve @ Henry Schein, Steve Kess, introducing Shafer and asking who to contact at the ADA since Kess had very close ties with the Association. He recommended Shafer contact Kathleen O’Loughlin, the executive director, and said she’d be most appreciative.
He did just that. O’Loughlin, or her assistant, referred Shafer to the ADA IT department and they reached back out to Shafer. Shafer says he was told they were already aware of the vulnerability 6 months prior, but couldn’t do anything about it because management of the website was outsourced to some other company. 2 months later, when Shafer saw that the website was still vulnerable, he emailed O’Loughlin again, wondering why it hadn’t been fixed and showing her screenshots of just how bad the problem was. He ended the email asking how long before they fix it, or did he have to bring it up with the doctors on dentaltown. In her reply back to him, she first thanked him for bringing it to her attention and then went on the offensive, taking his message as a threat and some odd manner of extortion. She politely volleyed a veiled threat of her own, reminding Justin that if he continues to attempt access to their systems, whether successful or not, he would be violating the law as he would be doing so without authorization. Not so appreciative after all it seems!
You don’t have to take my word for it, he mentions all of this on his blog, he just doesn’t spell it out very well. He’s not just pulling it out of his ass either, he’s got all the emails and calls with these folks to back up what he says.
I have to COMPLETELY disagree with your assessment of Kevin Krause’s articles. They say any press is good press, but in both Krause’s articles that’s just not true. His writing is filled with slanted phrasing, the headline of his latest piece alone says it all. I had intended to comment on his article with the following response, but by the looks of it, I’d be wasting my time. So I might as well dump it here…
Mr. Krause,
I have a lot of problems with the way you’ve approached Shafer’s story and how you’ve framed his activities, not just in this article, but in your last article as well.
We’ll start with the headline… “Alleged Hacker”.
I shouldn’t have to remind you as the federal courts reporter that the Feds have been in possession of Shafer’s seized electronics since May 2016 and have yet to indict him on any hacking charges. Nor should I have to remind you that he’s stuck in jail for nothing related to hacking. Soak in that for a second… Despite being raided three times by the FBI. Each time, seizing and scouring through his personal, business, and family records. Stuff they aren’t sure they’ll ever see again. Everything taken, at gunpoint… The machines he needs to run his business, sensitive patient information on his clients and their networks, patient information that he may have stored on behalf of his clients purposefully or incidentally through the natural course of working for HIPAA covered entities. They even seized the kid’s Wii console!! Calling him a hacker in your headline and then prefixing it with “alleged” feels very greasy to me. Unfair and irresponsible.
Later, you write: “Shafer runs a business that does computer work for dental offices”. Your description of Shafer’s profession is pretty damn shallow and I honestly can’t help but think it was intentional to do so. You certainly go out of your way elsewhere to frame his security related activities as entirely self-ascribed instead of simply referring to him based on his accomplishments in the patient data security sector. “Shafer says he’s this…” “Shafer claims to be that…”, etc. Like Shafer, I’m also a dental IT integrator. While nowhere near as talented and passionate about it as he is, I’m just as equally concerned about the state of security in dental practices. Why should we be so concerned? Because we’re not just tech monkeys “computer work for dental offices”. We sign business associate agreements with our covered entity clients and it becomes part of our responsibility to our clients and to their patients to help safeguard our client’s hardware and software from those who might pry.
As business associates, we too are bound by the same HIPAA and HITECH Act legislation as our clients, and face the same stiff penalties in the event of a breach. We are not comparable to your typical Best Buy or Staples geek behind the counter. Saying Shafer runs a business that does computer work for dental offices is like saying Arnold Schwarzeneggar is a fellow who likes to lift weights or Frank Sinatra was an Italian who liked to sing.
Shafer is certainly eccentric, he’s absolutely terrible with communication and he often writes in a manner that is cryptic and puzzling to many on the receiving end. If I had to pull a guess out of my psychiatric ass, I’d say he’s somewhere on the autism spectrum between a high-functioning asperger’s case and a savant. There’s no guesswork when it comes to describing Shafer as likely THE brightest dental IT technology specialist in the country. That’s a hyperbole free statement. He makes things work that simply shouldn’t work. He makes multi-billion dollar dental hardware and software companies look like fools finding solutions their top-tier engineers either can’t figure out or refuse to so that dentists are forced into upgrades they don’t need. He’s also an accomplished dental software developer and an acclaimed dental software security researcher. None of that is “alleged”.
He helped the FTC tackle the largest dental software and supply company in the world for lying to dentists about the data protections built into their software that were meant to protect patient’s information and doctor’s liability. He is credited mutliple times in the Department of Homeland Security’s US-CERT vulnerability database for the security holes he’s found, responsibly reported with embargo I might add, fully briefing the US-CERT team along the way. He’s also certainly not some lone wolf either. For years he’s partnered with databreaches.net to reponsibly report on the breaches he’s located. He’s not Mr. Robot and he’s far removed from that nonsensical stock photo “hacker with a hoodie” you’ve chosen to embed into the middle of this article. He’s a family man, with a wife and three young kids, all of whom have been left traumatized by what the FBI has done to their family.
You write that Shafer “claims” and “says” he’s helped do this and protect that, which can easily come off to appear as if he’s self-aggrandizing. He’s not some emo 19 year-old proclaiming to be genderqueer. His contributions to the Department of Homeland Security’s US-CERT database alone should really NOT be understated. Feel free to look him up. https://www.us-cert.gov/ His discovery and exposure of that dental publisher’s encryption lies leading to FTC fines are a separate matter entirely from the vulnerabilities he also has found a handful of practice management software titles, including Patterson’s Eaglesoft. The same company which would later claim they were hacked by him, kicking off the FBI raid trifecta. These holes are STILL not fully patched and they’re holes that are now an even greater risk in light of the recent break of the WPA2 wireless security protocol.
When US-CERT confronted the largest of these companies with the vulnerability Shafer had uncovered, their solution was to not let people on the network! Just enable WPA2 wireless security so bad actors can’t get on the network to take advantage of the problem! We’re talking about a situation where someone could gain unhindered access to the database containing patient’s medical history, insurance policy data, social security numbers, name, date of birth, allergies, full address, phone number, email, prescriptions, credit card details and more. The vulnerability affects possibly hundreds of millions of people in America and abroad where these companies also do business. It’s just ONE example.
As a software developer, he introduced intraoral camera software that allowed dentists to slash their costs and vastly improve the quality of their care by allowing them to use signicantly cheaper intra oral camera models with full control and drivers which allowed communication with dozens of different dental imaging systems. This broke the stranglehold on industry incumbents who charged dentists thousands of dollars for similar solutions (and still do). Thanks to Shafer’s software, dentists around the US and Canada have collectively saved millions of dollars in equipment and software costs and patient care has increased immeasurably.
Referring to him as a hacker, even an alleged one, is insulting. And in the eyes of John Q. Public, carries with it a highly negative association and we’re not even to the second half of the headline yet!
The second part of your headline purports it’s Shafer and/or his legal camp who make the claim for his reason for being in jail. No, that’s what the federal justice system is claiming. He violated bail orders to stay off of social media. To him, social media meant facebook and twitter. The very first message I received from Shafer upon his release on bond was a screen capture of his computer’s hosts file. The image showed his computer’s hosts file, where he set it to deliberately loopback the facebook and twitter domains so they could not even be accidentally visited.
You’ve already talked to a lawyer or two who has told you about the SCOTUS ruling on limiting access to social media back it June, so I won’t go there. I will question your social media “expert” however, who seems to think that blogs are social media. No, they are not. It depends entirely on how it’s used. They are publishing platforms for distributing articles. If Shafer’s blog is social media by this expert’s definition, then ALL media is social media. The New York Times, the Washington Post, Newsweek, Time, FOX news, MSNBC, even the Dallas Morning News. All have websites which carry content inviting comment and discussion from and amongst readers, with links provided for sharing within one’s own social circle. I think it’s rather a notable exception that Shafer took the step to DISABLE those “social” features on the article he posted which put him back in the klink. It’s not his personal diary. It’s not some peek into the crazy, nutty, goings-on of a dental IT guy, with selfies, pictures of food, and quiz results. It is his professional blog, there’s next to no personal information to be found on it. It’s where he sells his camera software. It’s where he writes about particularly frustrating software and hardware problems and their solutions with advanced tutorials which lesser Dental IT techs like me often follow. Of course it’s also where he discusses the security research he’s involved himself in; past, present and future. Obviously, the raids on his home for his investigation and disclosure of the Patterson FTP breach and the reasons for and why his incarceration and persecution are absolutely relatable to what he does for a living. This is especially true when it comes to the discussion of the particular special agent involved as Shafer has dealt with him in the past, prior to any raids on his home.
Shafer broke the story of a large breach of patient data from a Dentrix 11 dental database found on The Pirate Bay. For some independent background, see: http://wnep.com/2013/12/09/stolen-data-on-thousands-of-williamsport-area-dental-patients Shafer used a media partner to help responsibly report on this breach.(https://www.databreaches.net/thousands-of-pennsylvania-dental-patients-may-be-at-lifetime-risk-of-id-theft-after-patient-database-is-uploaded-to-torrent-sites/) The doctor’s lawyers in that case would claim the practice was not to blame, that it was a hacking incident and they pointed their finger at Shafer!
The database was uploaded to TPB years before and in its entirety as a flat file database and it was not hacked in any sense. In fact, as far as I’m aware, authorities found zero evidence to suspect direct hacking of the doctor’s network even occurred! The database was an old version of Dentrix containing patient record, SSNs, and other info for 11,000 people current to May, 2009. It was uploaded by someone in early 2010 to the Pirate Bay and found by Shafer in Sep, 2012.
The breach was in Pennsylvania, but it was the special agent at the local Dallas FBI field office which interviewed Shafer as part of the investigation. Shafer wrote about that call back he received long before the first raid occurred. He recalls that the agent asked if he was a pen-tester, a white/gray hat. Shafer replied in the affirmative, and Shafer says the agent responded with a threat that he should halt any whitehat activities, lest he would be visited by the agent and he wouldn’t want that.
Low and behold, Shafer would indeed wind up with a visit, from the very same Special agent, no less three times a couple of years later. There’s more to that Pennsylvania databreach of course… The HHS/OCR dropped their HIPAA investigation in late 2015, accepting the doctors claims that his Dentrix database was hacked. Rather odd considering the person responsible for posting the database to TPB, a user by the name of “zeusgodz”, claimed in his upload information box to have found the data on a USB drive. “I found a USB flash drive in the middle of the road and it had this Dentrix software on it. I don’t know if it needs activated or who would even be looking for this type of software, but someone put on a flash drive for a reason, so here ya go.” Upset over the OCR’s decision and their acceptance of the false hacker narrative, Shafer started digging into the user on the pirate bay which uploaded the data. The results of his search are some the cleverest armchair detective work I’ve ever seen on the internet. http://justinshafer.blogspot.com/2016/01/williamsport-pa-databreach-update.html
Shafer is charged with cyberstalking and doxxing a federal employee. I honestly have to wonder if you really read deep enough into both the unsealed complaint the feds drafted since since you totally neglect to address some incredulous points there, you also appear to have have glossed over repeated mention of those points in the defense motion to appeal detention.
First, the feds (and you) make it sound as if he spent a year pestering those poor people from May 2016 on… Not true at all. With few exceptions, the entirety of the posts related to his charges all occurred within the span of a few hours in the early morning of March 21, 2017. There was zero contact between Shafer and the agent, the agent’s relatives, or anyone else before AND after the incident. It’s written in the complaint used to obtain the arrest and seizure warrant that the agent, nor his wife, nor any of his relatives ever received any communication from Justin prior to this. It was only after the agent looked back through Justin’s twitter history and read a few of his easily justifiable rants of vitriol, (which were aimed at the FBI in genera and not the agent), that they chose to spring to action and arrest him. The complaint, now sealed again, contains the accidental inclusions of the agency’s microsoft word comments in the margins of the affidavit. They discuss the poor strength of their evidence and at one point one agent asks “Were the communications to the judge more clearly threatening?” Kind of makes you wonder doesn’t it? Did the judge actually read the entirety of this complaint or did he simply rubber stamp it based on the oral urgency of whomever “communicated to the judge”? How that alone isn’t something worth digging into is beyond me.
Ok, so he followed the agent’s wife on twitter? So what. It’s twitter. Unless your account is set to private and invite only, anyone can follow anyone else, that’s the WHOLE POINT of twitter. You’re a willing addition to the open database of users, the same applies for Facebook. The agents seem to wish to frame this as if Shafer had to go to some heavy hacker extremes to get the drop on his target. Who the hell on this planet DOESN’T look others up on Google, facebook, linkedin, etc.
So, he’s finally found them… What did he say or do that was so twisted and threatening? Did he send her pictures of dead rabbits? No, politely asks, with a smiley face on the end, to relay a message to her husband asking when he’d get his kids pictures and videos back since the FBI took them all from his home in May 2016. You neglect to actually show the content of those messages, which I think is rather telling. You were familiar with the details, you read the complaint, yet you chose to show an image of a tweet he wrote to the FBI regarding a Van he believed they had parked outside his home doing surveillance on him from months prior. It’s not even addressed to the agent, it’s to the FBI in general.
The question you really should have asked next here is why? Why would he do any of that? It’s because three hours before posting a smiley-face message to the agent’s wife, he discovered, for the first time, the actual name of the agent which had handcuffed him and raided his home, twice prior. Up until then he thought the agent’s name was something similar, but quite wrong.
All the contact he had tried to make with Feds since his initial raid, and he’s sent a LOT of data their way, seems to have fallen on deaf ears and blind eye because the name of the agent he thought was handling his case didn’t actually exist. The agent apparently never left his contact information with the Shafer family. What would ANYONE do in this day and age if they discovered the name of someone who they perceived to have brought unfair persecution down on them? They’d head STRAIGHT To facebook, linkedin and twitter, perhaps intellius, or spokeo too, all in an effort to learn more about someone.
Shafer’s crime there? Tweeting the status of that search along the way. Stupid? I guess so considering what the law has to say about it, however, it’s a pretty damn transparent act for someone the DA’s office claims as the “mastermind” of the dark overlord group. If anyone wishes to read what REAL and substantial emotional distress is, they should talk to his traumatized wife and kids or at least read her statement here: https://www.databreaches.net/wp-content/uploads/177111111998.pdf I would love to be able to sit across from that agent reading her words and then have him explain to me how he thinks his family has been put through the same or worse by Shafer.
Your last few paragraphs really take the grand prize though. Here, like in that unsealed FBI affidavit, you make a conscious editorial choice to follow the FBI’s lead, implying connections exist between the dark overlord and Shafer which simply are not there.
You spend a paragraph detailing all the things that Shafer claims about himself and you neglect to mention anything at all of his documented accomplishments, the vulnerabilities he’s uncovered, nor any of the public praise for discovering and properly reporting on data breaches and other security holes he’s found that are well publicized. The FBI did the same in their complaint.
You end by claiming the May 2016 raid resulted in the seizure of a database known to have been put up for ransom on the dark web. No, that was the SECOND raid of his home, January, 2017. The one where they also “discovered” his chats with the dark overlord. That database, the smallest of three databases being hawked on the dark web, was given as proof to both Justin and an Australian security researcher.
Just like the Feds who wrote that warrant complaint, you mention nothing about the fact that even after the initial raid in May 2016, Shafer kept contact with the FBI and sent them the copy of the database he had received and spent over an hour on the phone with the Missouri field office discussing it the same day he received it. That’s all in his appeal motion, why would you leave that out of your story? How in the hell is that balanced reporting?
The chats they discovered, were captures of twitter conversations, yes the dark overlord has a twitter account, which Justin wanted to keep a record of for analysis and for sharing with others which he routinely did. I saw some, the admin @ databreaches.net saw some, anyone interested in helping bring those assholes to justice got to see them INCLUDING the FBI.
The FBI’s complaint and your article also fail to mention that Justin immediately informed MI5 and the NHS in the UK as well as the FBI on cc when he learned the dark overlord had hacked into the UK’s national health service.
Your article and the FBI complaint also fail to regard the efforts made by Shafer to contact file dump and distribution websites like Mega, where the dark overlord was dumping data to inform them that the group had dumped patient data and to delete it asap.
Let all that sink in… Despite raiding him, taking all his stuff, scaring the shit out of his kids, damaging his property and his business and his status in the community, he persevered and kept sending the FBI data.
There’s even MORE To this story, but I’m tired.
I HIGHLY recommend to you, Mr. Krause, and for anyone else reading this article to go read Mike Masnick’s techdirt.com articles on this subject as they are quite thorough and do a much better job of covering the many facets of this very complicated story. You’ll want to see what dissent @ databreaches.net has to say as well if you’re truly a journalist concerned with balanced reporting.
Leadership at the DOJ and FBI changed in January due to the election. Is there anyone that can be contacted in the new administration that can serve as an advocate?
Or does the entrenched bureaucracy carry on regardless of who’s in power? That’s pretty scary to contemplate.
Read Ken White (@Popehat’s) blog post about this subpoena (he’s targeted, too), and why people should resist the urge to just call the DOJ and try to discuss it:
https://www.popehat.com/2017/10/24/in-which-my-identity-is-sought-by-federal-grand-jury-subpoena/
The biggest problem we have in this nation is 2 fold..
Blame and Shame..
We WANT a solution and will point fingers at Anyone/anything..
Even if we created the instance and Fault..
FOR SOME AWFUL REASON we can not Admit, something is wrong and we did it..it dont matter which side you are on..
Much of the faults happening NOW, tend to be Automated systems NOT doing a good job of protection.
An old adage.. How NOT to treat a dog.. If you keep beating a dog to make him MEAN, you only have 2 choices of out come.. A BEAT DOWN DOG that wont do you any good, or a DOG that will HATE YOU until it can BITE YOU as much as you have BEAT HIM..
People keep saying YOU HAVE A CHOICE, to do/not do something.. NOT IF you DONT have the choice..and cant find a path OUT of the problem..
Is there a link to the affidavit you posted screenshots of?
I didn’t upload the affidavit because I was confused as to the legality of uploading a file that was sealed, unsealed briefly, and then resealed. But someone else uploaded it on another site: https://assets.documentcloud.org/documents/3535241/Shafer-Complaint.pdf
Rule nr 1 is never talk to the police or the FBI. Because they are going to f- you over flat and do so with no regrets. This case looks like a corrupt FBI agent (this type of thing has happened before). I guess someone should look into that angle sooner rather than later.
At least you tried. Some day, someone will look at this whole case and say, “Why didn’t anyone DO anything at the time?” 🙁
Wow. I don’t know if Krause will read what you wrote, but I hope he does.
Very well said, Trent. Hope you Email it off to them. Good on you.
I really should have proofread that. Lots of grammatical errors, total stream of consciousness, and by the end I was literally falling asleep at the keyboard, too tired to even get the links to mike’s stuff and the evidence of his contact to the feds you’ve got on your site here. The thrust of my arguments are there. Is it editable?
Just leave it… I’m sure you’ll have more to say at some point. 🙂
Right now, I’m trying to get my hands on the PC affidavit for the second raid. Do you happen to have a copy?