Update: On December 2, Sunshine Behavioral Health reported this incident to HHS as impacting 3500 patients. They also ticked the box for Business Associate.
Update 2: On January 23, 2020, ID Experts submitted a copy of their notification to patients to the Vermont Attorney General’s Office.
Another day, another leak. In this case, an error exposed some personal and financial information of patients treated for alcohol or drug addiction.
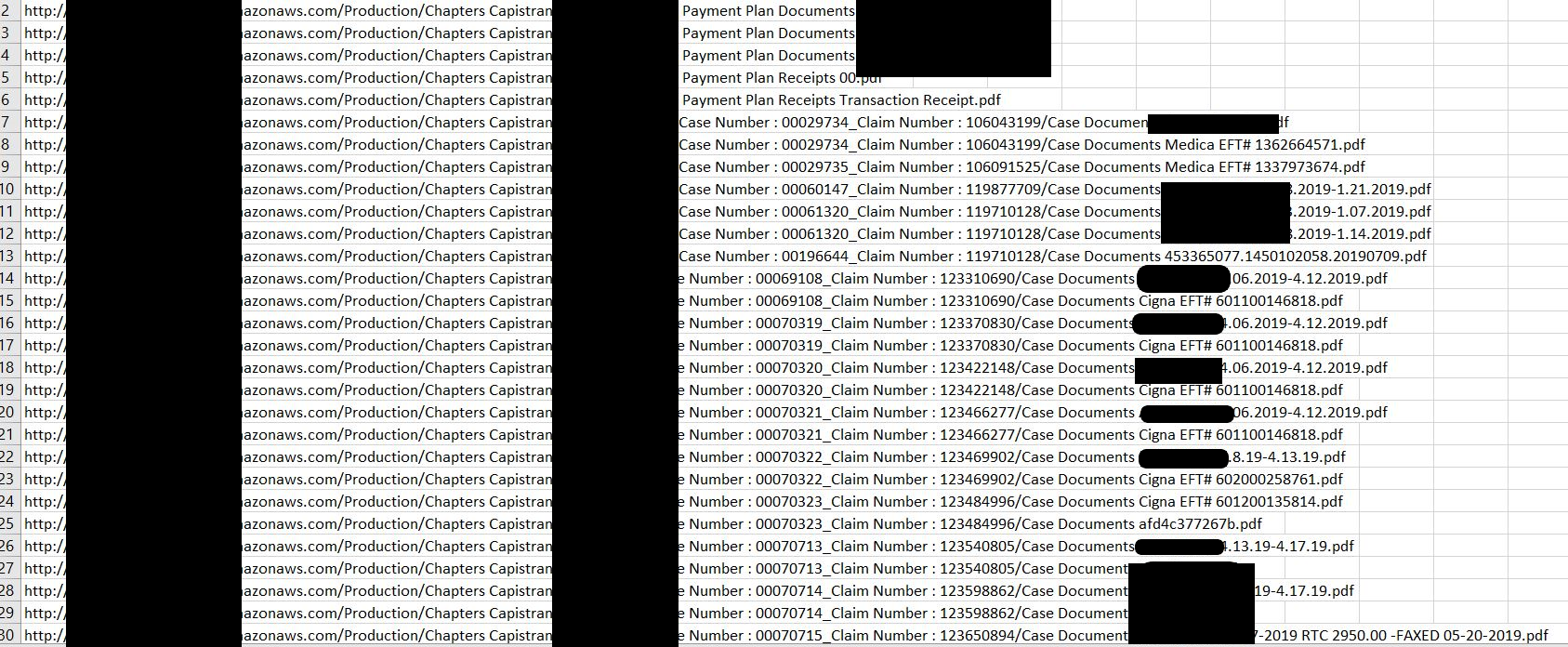
Sunshine Behavioral Health, LLC is a private network of drug and alcohol addiction treatment facilities with locations in California, Texas, and Colorado. At some time as yet unknown to DataBreaches.net, approximately 93,000 patient files related to billings for patients at their Monarch Shore, Chapters Capistrano, and Willow Springs Recovery facilities were exposed online due to a misconfiguration of an Amazon AWS s3 bucket. DataBreaches.net notes that the approximately 93,000 files did not represent 90,000 unique patients, as for many patients, there was more than one file, and not all files were actual files (some appeared to be templates or test data).
The leak was discovered in August by someone who shared the exposed data with DataBreaches.net. After verifying that the data were exposed, this blogger called Sunshine Behavioral Health on September 4 to alert them to the exposed data.
The employee who took the call said he understood that he needed to pass along the message immediately to their infosecurity people, but the files were still unsecured the next day. So DataBreaches.net called them again. This time, I was told that the employee I had spoken with the previous day was not there at the time, and I was asked to call back. I may or may not have hollered at that point, but I did tell the employee who had answered the phone that I wouldn’t call back again, and they needed to have someone in charge of patient privacy or data security call me back promptly.
Stephen VanHooser, their Director of Compliance, returned my call. He claimed he knew nothing about my phone call to them the previous day, so I have no idea what the first employee did, if anything. But after I spoke with VanHooser, access to the bucket was disabled.
Sunshine Behavioral never got back to me to tell me the results of any investigation or what they were doing in response to the incident. And there has been nothing on their website, the California Attorney General’s website, or HHS’s public breach tool, even thought it is more than 70 days since they were first notified or discovered the exposure.
Did Sunshine Behavioral Health ever notify HHS OCR or any patients or state regulators? Did they investigate and determine that notification was not required? Do they know how many people might be in possession of a copy of all those files? DataBreaches.net does not know the answer to those questions.
But in trying to follow up to see what they had done, I realized that the files were still accessible without any password required if you knew where to look. And anyone who had downloaded the urls of the files in the bucket while the bucket was exposed would know where to look (I realize this is true for these situations in general and it is not unique to Sunshine Behavioral Health).

On November 10, I sent VanHooser an email notification that the files were still not secure. I also asked what Sunshine had found after they investigated my September 4 notification and I asked whether they had notified any regulators or patients.
Getting no response at all, I sent a second email to him on November 12. He has not responded, but it appears access to the files has been disabled.
So what was in the unencrypted files? They generally did not contain treatment or medical history records, although a few do contain diagnostic codes, treatment codes, or reference to “detox.” For the most part, though, they were billing statements or correspondence concerning unpaid bills for some patients treated between 2016 and this year. The screenshots above show two of a number of types of files in the exposed bucket. Files revealed the following kinds of patient information:
- full name
- date of birth
- postal and email addresses
- telephone numbers
- full credit card numbers with expiration dates (month/year) and full CVV code
- health insurance membership number, account number, statements concerning insurance benefits, and amounts due and paid.
Not all patients had all of those data types exposed.
Because Sunshine Behavioral Health did not respond to queries, DataBreaches.net sent inquiries to some patients whose data was exposed to ask if they were ever notified of the exposure incident. So far, out of the small sample of patients, none of the emails have bounced back, but none of the patients have responded.
This post may be updated if more information is obtained. DataBreaches.net has not yet decided whether to report this incident to HHS OCR, but is reporting it here because Sunshine Behavioral Health has neither posted anything on their site nor informed this site whether they have made notifications to patients and/or regulators.
Correction: a previous version incorrectly stated that there were partial expiration dates for credit card numbers. Those were actually full expiration dates (month/year).