In what seems like a mind-boggling OPSEC #FAIL, a U.K. man associated with thedarkoverlord allegedly used his real details to create bank accounts as well as to open email accounts, phone numbers, vpn, Twitter, and PayPal accounts that thedarkoverlord used as part of its operations to hack and extort victims. For a group that signed their pastes and extortion demands as a “Professional Adversary,” the revelations should be embarrassing, to say the least. But embarrassment may be the least of their problems. Now that Nathan Wyatt is in custody in the U.S. awaiting trial for his alleged role, will he roll on others to get himself a deal?
In June, 2016, an individual or group calling themself “thedarkoverlord” (TDO) announced that they/he had hacked three patient databases and put them up for sale on a dark web marketplace. Since that time, this site has reported on TDO’s criminal activities dozens of times, but even the many hacks this site has covered represent only a small fraction of TDO’s actual criminal operations. The scope of their attacks often tends to get lost in mainstream media coverage that tends to only point out hacks involving Orange is the New Black, celebrity patients, or well-known corporations like Gorilla Glue. But TDO has hit numerous big and small businesses, school districts, universities, and big and small medical entities. And over the past few years, those of us who have watched them have seen them grow increasingly aggressive and violent in their imagery and threats. But then things seemed to suddenly stop.
In early 2019, KickAss Forum shuttered. Without that forum to post their offerings and banned from most social media platforms they had been using to try to sell hacked files, TDO disappeared from public view. They haven’t responded to emails I have sent to their email account for journalists, and they didn’t re-emerge on New Year’s Eve with a major hack announcement as they have done in past years. So where’s TDO? Are they in custody or have they gone to ground because one of their alleged members, Nathan Wyatt, is now in U.S. custody awaiting trial? Have they continued hacking entities? Or are they just relaxing somewhere enjoying retirement? Significantly, perhaps, their disappearance from public view roughly corresponds with Wyatt losing his appeal of a ruling ordering his extradition to the U.S.
Either way, for a criminal operation that often tried to portray itself as a polished and professional adversary, Nathan Wyatt is not a good look for them.

Who is Wyatt?
Nathan Francis Wyatt, 39, is an unemployed U.K. national who lives in Wellingborough with his fiancee, Kelly Howell, and some of their children. He and his fiancee live off the welfare benefits they receive from the government. Wyatt has acknowledged that he has supplemented those benefits with illegal online activities.
Unless there’s some plea deal worked out, Wyatt will be tried in federal court in St. Louis for his alleged role in some of the early TDO hacks and extortion attempts in Missouri, Illinois, and Georgia.
The indictment can be found here. Wyatt faces trial here on 6 counts: a single conspiracy charge, two counts of aggravated identity theft, and three counts of threatening damage to a computer. Although DOJ did not name the victim entities in their court filings, I have identified the victim entities (with one possible exception) based on DOJ’s descriptions, my previous detailed reporting on the breaches, and the fact that some of the evidence DOJ provides in the affidavit exactly matches files that had been given to me by TDO for those victims.
Wyatt, whose online nicks include “Crafty Cockney,” “Hardcore,” and “Mas,” pleaded not guilty in his first appearance in federal court in December after losing his attempt to prevent extradition.
OPSEC? What OPSEC?
Anyone reading the affidavit supporting the government’s extradition request may understandably conclude that Wyatt should try try make a plea deal. There appears to be a tremendous amount of compelling evidence supporting the charges, although of course, those are just allegations that need to be proved in court. But then also remember that DOJ did not show all its evidence in the affidavit. They likely withheld what they consider to be other damning evidence that they will present at a later date or use to persuade Wyatt to plead guilty.
Actually, if you read the affidavit, you may well wonder what on earth Wyatt could possibly have been thinking when he allegedly used his own personal details to open email, phone, PayPal, and bank accounts that were used for criminal purposes.* Did Wyatt’s alleged co-conspirators have any idea how casual and negligent he was about OPSEC or did they know what he was doing? From statements made to me by TDO in September 2016, they had no idea that “Crafty Cockney’s” real name was Nathan Wyatt and so when they saw the bank accounts he had set up, they did not know it was his real name and his fiancee’s real name and their real addresses. Whether TDO was telling me the truth in disclaiming any previous knowledge of Wyatt’s identity remains to be determined.
Wyatt was no stranger to crime
The current charges represent only a small part of Wyatt’s alleged criminal activity over the past 3 years.** Charges against him in 2016 for his role in selling hacked photos of Pippa Middleton were dropped and he never served any time for his role in that case. Those close to that situation believe that the charges were dropped to spare Middleton the stress of a court case and not for lack of evidence. Both The Sun and this blogger had quite a bit of evidence showing Wyatt’s involvement in the attempted sale of the photos.
But while Wyatt seemed to have caught a break in the Pippa Middleton case, he wound up arrested again months later because in the process of investigating the Middleton matter, prosecutors found evidence of other crimes on his devices. As a result of their discovery and charges, Wyatt pleaded guilty to almost two dozen charges, including 20 fraud charges and two blackmail attempts. Those charges included a 2016 hack of a law firm and attempt to extort it as “The Dark Overlords.”
Wyatt was sentenced to three years in prison and was jailed from June, 2017 to August, 2018. As soon as he was released, he was picked up on the U.S. charges for which he will now stand trial. This time, however, Wyatt may not get off as easy as he has in the U.K., as our sentences tend to be longer than U.K. sentences for the same crimes.
Wyatt has children and a fiancee in the U.K., and no connections here. By his own statement, he has significant medical concerns that include a history of heart attacks, and he also needs psychotropic medication and medication management. Will he decide that a possible years-long prison term in the U.S. is more than he wants to risk by going to trial? Will he try to make a deal, and if he does, does he have anything to offer that would motivate the prosecution to make a deal?
Can Wyatt name thedarkoverlord, and if he can, will he?
In chats with this blogger in the fall of 2016, Wyatt claimed to know the real identity of the person who was posting as thedarkoverlord on Twitter and Jabber, and who had chatted extensively with this blogger. Wyatt claimed that he had learned the other’s real identity because he had agreed to make a phone call to TDO’s landlord so that TDO wouldn’t be evicted when he was late with his rent. But according to TDO, Wyatt did not know his real identity. Because Wyatt wouldn’t say more, his claim could not be confirmed. If Wyatt really does know the real identity of the other, that is probably his best bargaining chip to make a deal.***
Regardless of whether Wyatt knew TDO’s real identity, it was clear to this blogger that he was involved in and knowledgeable about TDO-related operations, including how TDO had selected his victims. According to Wyatt, TDO purchased access to cracked servers on xDedic when cracked servers were selling for less than $10 each. DataBreaches.net was subsequently able to confirm that victim entities known to this site had indeed had cracked servers listed for sale on xDedic. And worryingly, there appeared to be many more who were at imminent risk.
Although Kaspersky had issued a report in June, 2016 identifying the problem with xDedic selling cracked servers, thedarkoverlord’s use of that marketplace was not publicly known at that time. Because of this blogger’s extensive chats with TDO, DataBreaches.net had knowledge of many of their attacks that had not yet been revealed publicly. Teaming up with a trusted partner, DataBreaches.net and that partner determined how many entities hacked by TDO had had cracked servers for sale and how many entities were still at imminent risk from TDO attacks. With the help of an industry organization, an alert was sent to hundreds of at-risk entities to inform them that access to servers had been sold and to urge them to take immediate steps to protect their patients’ data. DataBreaches.net’s role in that effort to warn covered entities was not publicly disclosed at the time due to some concerns as to how TDO might respond if they knew this site was using information on their methods acquired from “Crafty Cockney” to thwart their operations.
TDO takes a reputation hit
According to Wyatt, when logs from xDedic were made publicly available after xDedic closed for a while, those logs exposed TDO as someone who wasn’t a brilliant hacker but who was just buying access to servers. Given his previous bragging, the exposure understandably resulted in TDO’s reputation plummeting.
Wyatt’s statements were consistent with the fact that without any background or context,TDO had suddenly informed me that he was going to disappear and leave the scene. He didn’t really leave the scene, although it seemed clear that there were some personnel changes that took place after that. Discussion of those changes in the latter part of 2016, during 2017, and thereafter will have to wait for other posts on other days, because this post is focusing on Wyatt’s role in TDO’s 2016 activities and his knowledge of TDO activities during the time period when the victim entities were hacked and extortion was attempted.
How good a hacker was Wyatt?
How many people were hacking for TDO and was Wyatt one of them? In our earliest contacts, Wyatt had told me that he wasn’t a hacker but had other skills. As one example, he told me he hadn’t hacked Pippa Middleton’s account but was just handling the sales negotiations with media outlets and that he was more of a translator or interface for the community. He described himself as someone who had a seat the table and a lot of freedom. Occasionally, however, he would contradict his earlier claims that he didn’t hack by bragging about hacks he claimed he had conducted — including some hacks TDO had claimed as his hacks. Not once, however, did Wyatt ever claim that he had hacked any of the victim entities in the St. Louis case.
Wyatt also frequently claimed that he had mentored and trained TDO and that TDO would seek his counsel, assistance, or feedback on pretty much everything in the early days. While TDO downplayed Crafty Cockney’s role whenever I would ask TDO about him, Wyatt made himself sound like he had a bigger role and influence, with a few exceptions. One notable exception was an alleged hack of ReleasePoint. Although Wyatt told me that he and one other person (who he didn’t name) knew about the ReleasePoint hack, that had been “Dark’s” doing, and Dark had allegedly cleaned the company out of two million records. Given that he did not deny involvement in other cybercrimes involving TDO, I found Wyatt’s denial of involvement in an alleged ReleasePoint hack interesting and somewhat convincing. No ReleasePoint hack was ever made public and ReleasePoint never responded to my inquiry as to whether they had been hacked, but Wyatt claims that he was questioned by the FBI about ReleasePoint on a few occasions.
When Wyatt was prosecuted in 2017 for hacking the unnamed law firm in December 2016 and then trying to extort it, the prosecution never really proved that Wyatt did the hacking. They didn’t need to, because Wyatt pleaded guilty as part of a deal. For all we know, then, it may have been the case that someone else did the hacking and that Wyatt was just involved in the extortion attempt.
So how good was Wyatt as a hacker? This blogger has no clue, and it doesn’t particularly matter for this case because Wyatt is not charged with hacking. Under the extradition agreement, no additional charges can be added to the indictment, either. Should Wyatt ever be indicted in other states for other TDO hacks, his role in actual hacking might become a significant issue, but for now, it does not appear to be.
Trouble in paradise?
By October of 2016, Wyatt was seemingly getting frustrated with “Dark” (as he referred to the other person). According to Wyatt, TDO hadn’t made any money at all since its inception, and Dark was trying to get Wyatt to give him 20% of money he thought Wyatt had received for the sale of Pippa Middleton’s pictures — even though according to both Wyatt and “Dark,” “Dark” had presumably not been involved in that hack.
Wyatt’s claim that TDO hadn’t made any money was interesting, because TDO had repeatedly told me that TDO was making money (i.e., some victims were paying up), and they would later show me proof of that (as I reported here). But Wyatt repeated that claim a number of times to me in 2016 — that TDO hadn’t made any money. So was Dark lying to Wyatt about early operations so that he didn’t have to give Wyatt any of the money, or was Wyatt lying to me in October of 2016? Or was there some other explanation?
In one exchange between Wyatt and Dark in the fall of 2016, Wyatt repeated his assertion that TDO hadn’t been successful, and Dark responded that Wyatt did not know about all of TDO’s operations. Wyatt was logged in as [email protected]. DataBreaches.net does not know what Jabber account “Dark” was using for this chat.
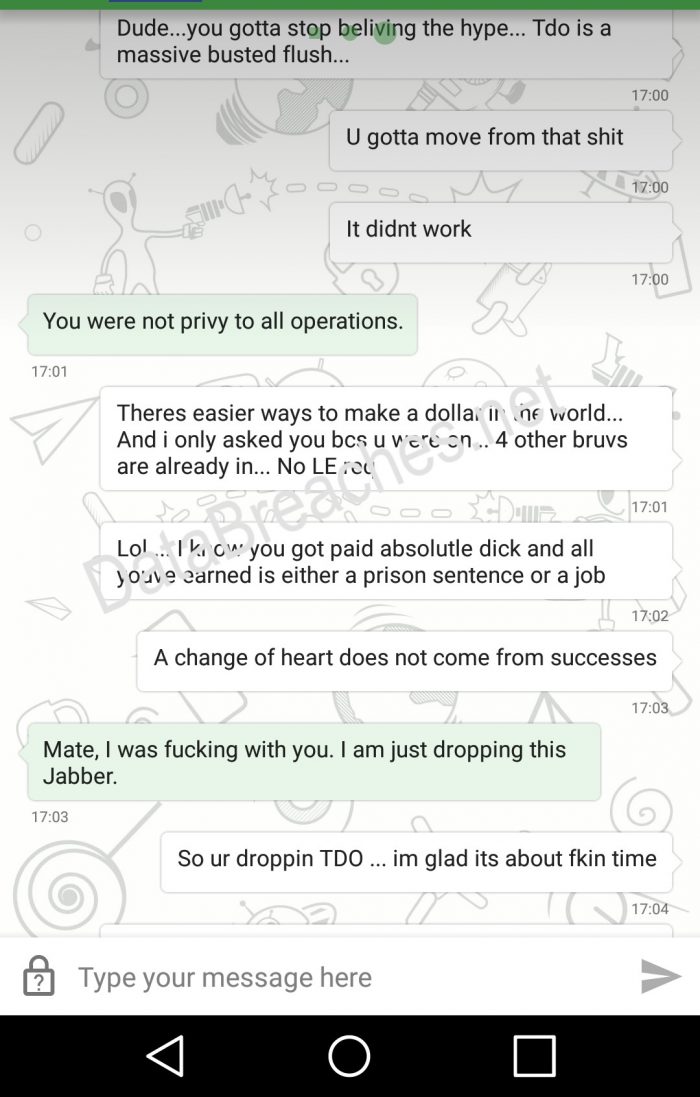
Over the next few months, Wyatt appeared to become increasingly distrustful of Dark, saying he suspected that Dark was looking to protect himself by rolling on him or others, as this snippet from one chat between Wyatt and “Dark” illustrated:
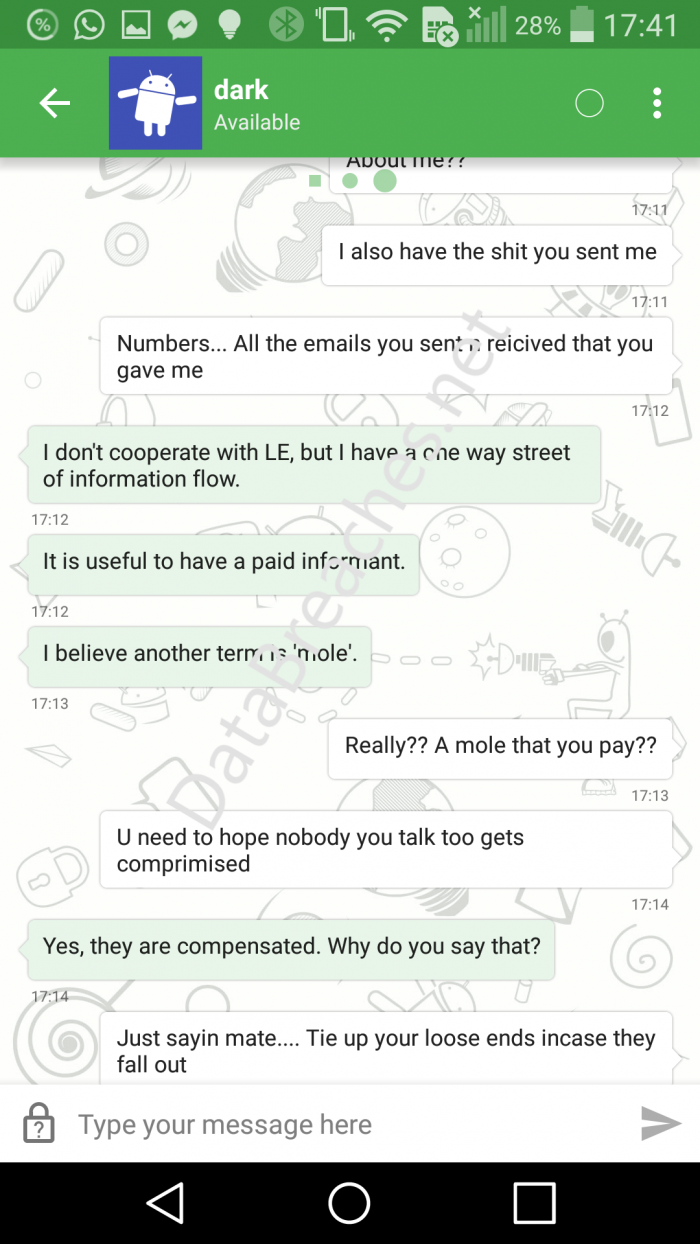
Weeks later, Wyatt would tell this blogger, “Dark fucked me.” When asked to explain how, Wyatt replied, “Well LE [law enforcement] have a file containing stuff only between me n dark.” When I asked Wyatt how he thought LE had obtained it, he indicated his belief that Dark had rolled on him. According to him, the chat logs were likely from their chats using the Proter3 and darkmoney jabber accounts.
But what took on later significance was his answer to my question as to what was in those chat logs. Wyatt responded, “Him running details past me etc …. Its built in a way that it looks like i was tdo boss.” The chat logs had been redacted, he claimed, but he didn’t offer any guess as to who had redacted them.
“But its tellin a story that is far far from the facts,” Wyatt wrote. “Its suggestive ill say that,” he continued, telling me that Athens Orthopedic was one of three hacks where the logs made him look like the TDO boss. The other two were the Missouri clinics for which he also currently faces charges in federal court.
Was Wyatt anticipating the charges and testing out a possible defense on me? Or was his role really being edited by the individual he called “Dark?” The answer to that may depend on whether law enforcement really has the chat logs Wyatt claimed they have. Wyatt’s defense counsel has made a comprehensive request for evidence and records in discovery. Those logs, if they exist, should be produced.
Before “TDO” there was “Arnie.” Is Wyatt “Arnie?”
At various times, a number of people have claimed that Wyatt is “Arnie,” a persona that appeared to be the predecessor of the first TDO spokesperson. If it is true that Arnie became/was the first spokesperson for TDO in the summer of 2016, then Wyatt is not Arnie. There are at least three of lines of evidence to support that conclusion:
- Arnie is more literate and educated than Wyatt in written communications. Wyatt’s written communications in real-time are replete with spelling errors, grammatical errors, and are often crude in language. You can find some samples of his writing in this post and some samples of TDO’s writing in screenshots in this post, but I have many more exemplars in my files.
- Some chat logs involved both “Dark” and Wyatt, as illustrated in screenshots in this post. Unless you believe (which you might) that Wyatt was using two phones to have a conversation with himself as two different identities with radically different writing, then Wyatt isn’t Arnie or the person who was the spokesperson for TDO.
- I chatted with the first TDO on a number of occasions while Wyatt was actually in jail, including while Wyatt was being held over the Pippa Middleton hack.
So if “Arnie” was the first TDO spokesperson in 2016, then Wyatt is not “Arnie” or “TDO.” But Wyatt did provide valuable services that we’ll get to later. But first: if Wyatt isn’t Arnie or the first TDO spokesperson, then…
Was TDO 2 people … or 3 people… or 4…. … or more?
In a 2016 forum comment about a ransomware attack on Hollywood Hospital, Wyatt, posting as “Crafty Cockney,” claimed that thedarkoverlord consisted of one person in their 20’s, one in their 30’s, and one in their 40’s.
“actually a Trio of 20-40 somethings with a mixture of Intelligence, Strategy, Humour, & Bottle”
#Thedarkoverlord
Wyatt would have been about 35 at the time.
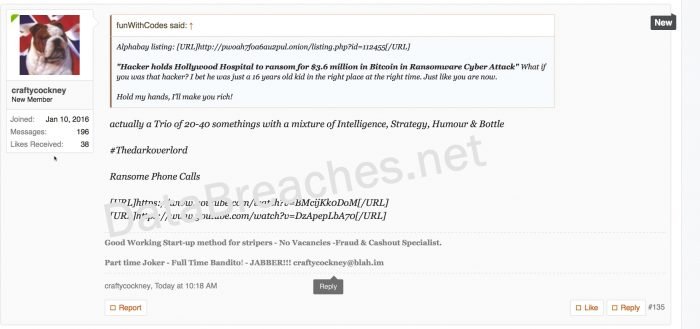
But later, in October of 2016, Wyatt claimed that TDO was a one-person operation. That one person was an individual he referred to as “Dark” and whom he described as being in his 20s. Wyatt also claimed Dark was living with an older woman with her children. That description was somewhat consistent with what TDO had told me of his living arrangements, but it was not totally consistent.
But if his forum post was true, Wyatt, if he was including himself as a member of TDO, was the 30-something and “Dark” was the 20-something. But who was the 40-something and why did Wyatt later claim that TDO was a one-person operation instead of saying a two-person operation based on him and “Dark?” Remember that Wyatt did allude to a third person who was in on the ReleasePoint incident. Wyatt never named the third person, and I have no evidence as to whom any 40-something might be in the early days of TDO, although there is some evidence to suggest the involvement of other people who were likely much younger.
Although in July, 2016, I thought TDO might be just one person who was being assisted at times by Wyatt, I subsequently began to think there were at least 3 or 4 people regularly involved in TDO. That impression was strengthened the following year when I had an opportunity to look at some of their BTC wallets from 2016 and I could see how many wallets the extortion payments had been equally distributed to. But was Wyatt one of those who appear to have shared in the distribution of gains? DOJ has not provided any evidence yet concerning any BTC wallets and withdrawals or payments Wyatt may have received.
Claim in DOJ Affidavit: Wyatt made threatening phone calls to support the extortion demands.
The AlphaBay forum post depicted earlier in this post linked to voice recordings of the extortion attempts that Wyatt has been charged with. In chats with this blogger in 2016, Wyatt admitted that he was the voice in the extortion recordings, although he subsequently tried to claim that although he made the recording, he never made the actual phone call to the victim and that he only made the recording because TDO was pressuring him to. You can hear the recording here, including the voice of a person who answered the phone. Since the victims presumably reported the phone calls to the FBI, and law enforcement has his phone records, Wyatt may have trouble defending again this allegation.
Claim in DOJ Affidavit: Wyatt sent threatening text messages to extortion victims and their relatives.
The affidavit contains transcribed examples of some threatening messages. Not only is the writing in the text messages below totally consistent with Wyatt’s writing in our numerous chats (note the spelling and grammatical errors, as well as the crude tone), but Wyatt actually used the phrase, “stay hot, Babe,” in communicating with this blogger — a phrase that appears in one of the text messages below:

The affidavit also contains evidence as to the ownership of the phone number that the calls were made from, and yes, it allegedly links to Wyatt.
Claim from law enforcement: One member of TDO was arrested — a 38 year-old Serbian.
That one appears to be partially true. A 38-year old Serbian who was only identified by initials “S.S.” was arrested, but then we heard nothing more about it. Months later, a source with knowledge of the investigation who was not authorized to speak about the case told me that it appeared that law enforcement had erred or at least severely exaggerated in claiming that the individual was a member of TDO.
What’s Next?
There is an attorneys-only conference scheduled for January 15 that has to do with discovery and pretrial issues. Looking at the defense counsel’s discovery request to the prosecution, discovery is likely to take a lot of time.
But if I had to bet at this point, I would bet that Wyatt will be convicted on the charges against him if it goes to trial and that it won’t take the jury more than one hour to convict him on all counts. I would also bet that Wyatt will not roll on TDO even if he does know his real identity.
I continue to believe that Wyatt was never the top person in TDO at any time. While he may be a recidivist fraudster and engaged in the hacks and extortion attempts, I doubt he wrote the highly detailed email threats or “contracts” that we saw in numerous cases. And we know he was in prison in 2017 at the time when TDO was attacking school districts and when parents were receiving death threats and students were also being sent threatening messages. We have yet to see any announcement concerning the arrest of that individual or those individuals.
Stay tuned. You can reach me via Signal at +1-516-776-7756, or via email me at breaches[at]protonmail.ch if you have any corrections or additional information you would like to provide.
End Notes:
* One of the bank accounts created to receive extortion payments to be sent by Athens Orthopedic actually used Wyatt’s fiancee’s real details. No evidence has ever been produced to a court concerning Kelly Howell, however. As part of their investigation into earlier charges against Wyatt in another case, the Crown Prosecution reportedly had charged Ms Howell with handling stolen goods and encouraging or assisting other offenses, but she was acquitted after the prosecution offered no evidence to substantiate any charges. DataBreaches.net attempted to contact Ms Howell several times to seek comment for this story, but she did not respond to the email sent to the only email address this site had for her or to attempts to let her know through Twitter that I was seeking to contact her. (SEE UPDATE AND CORRECTION, PLEASE)
** In the course of numerous chats, Wyatt admitted to participation in a number of sophisticated crimes and operations in the financial sector that did not involve TDO. He also claimed to be a partner in a dark web marketplace, but DataBreaches.net never found any evidence that the marketplace was ever launched.
*** Wyatt also claimed that he had logs that contained the information on TDO’s real identity as well as tons of other chat logs and files, but that he needed money to get them out of storage. It sounded like a scam to get money from me, but in any event, DataBreaches.net does not buy data. When I mentioned Wyatt’s claim to a security professional who had been investigating TDO, they said they would be interested in buying his logs and that if they obtained them, they would let me see them. Not surprisingly, Wyatt failed to deliver the promised files after receiving their payment. Those reporting on Wyatt need to remember that he is a fraudster. Much of what he said to this blogger about TDO, himself, and others is best read with a healthy dose of skepticism if there is no actual independent proof or confirmation.
UPDATE AND CORRECTION: On January 11, Kelly Howell submitted a comment claiming she had emailed me a number of times and that I had ignored her emails and was lying. I was not lying. I never got any emails from her at all. And on investigation, that was totally my fault. A wildcard in my blacklist had managed to delete all of her emails from my server without me ever seeing them. I apologize unreservedly to Ms Howell and hope she re-sends her emails so I can see what she wrote and try to incorporate it, even now.
Well that’s a total lie….
U emailed me and I replied to you. I can screen shot and show u all the emails we have sent if u would like.
If u choose to write it lies that’s fine if others choose to belive ur lies that too is fine. But to write that u contacted me and I didnt respond I wont sit here and have u like about me When we both know I responded to your emails.
Now we both now u wont post this. As it will make u look bad. I havent followed ur posts. I only found out about this one when a mutual friend contacted me and told me about it. Up untill now I havent had a issue with ur writing as nathan isnt TDO and that one thing we can agree on. But now I see ur bringing my name into this and what ur writing is lies I will monitor what I say. Thanks
Whoa. I have not gotten any emails from you. Please check the address you sent them to, or re-send them. Or better yet, forward them to a second address of mine. My email addresses include: admin[at]databreaches.net and breaches[at]protonmail.ch. Replace the [at] with the @ symbol. Amd if you re-send, post a comment here so I know you’ve re-sent them.
I’ve never knowingly ignored an email from someone I’ve emailed for a story. NEVER. So I don’t know why the email(s) you claim you sent didn’t get to me, but they were not ignored.
Oh, for Pete’s sake….. I just went searching to see if I could figure out what happened to the emails you said you sent, Kelly. I found something in my blacklist filters with a wildcard that would have blacklisted your email address and deleted it/them from my mail server without me ever seeing them.
I am so sorry. Please do re-send and I will update the post to reflect my error.
Good morning
I have resent my emails to you.
I hope u get them this time.
Nathan’s attorney had a status hearing yesterday. So I’m waiting to find out what’s going on.
I know u have a job to do. But nathan isnt this person u think he is.
I sent you email acknowledgement of the two emails I got overnight. Hopefully there won’t be more problems with my mail filters deleting your emails from the server.
And yes, I have a job to do. But I don’t think you have an accurate understanding of who I think Nathan is. I am not the one running around claiming he was other personas that I don’t think were ever him.
Sorry it’s taken me a few days to reply.
I am going through a few health issues.
Had to have a biopsy and some tests done but I will sit down tomorrow and find and send the old emails if u want them.
Kind regards
Yes, please. I’d like to see them in case there’s anything I might have reported incorrectly that I’d want to amend or correct.
In the future, if you email and don’t get an ACK, don’t assume the worst of me. I tend to be very careful in my reporting, which is why I reached out to you for comment or clarification in the first place. And I always acknowledge receipt of emails, although sometimes not the same day if I’m swamped.
I can also be reached via Twitter, my protonmail addy, Signal, and xmpp.
I hope your test results come back clean. And if you can’t get back to me right away, don’t worry, unless there’s something critically urgent you think I need to know or correct.
I seriously hope this man does not come back to the UK. Let him rot out there. Amount of crime he’s done and then to boast about it is a disgrace. How can his kids look up to him and call him dad is beyond me. Hope he’s locked away for a long time so we don’t have to pay that vile man his benefits