In May, 2019, Lawrence Abrams of Bleeping Computer reported on threat actors using Maze ransomware, a then-new variant of ChaCha ransomware. As reported by Abrams, Jérôme Segura had found that the ransomware was being dropped by the Fallout exploit kit. In October, researchers also noted that it was being dropped using the Spelevo exploit kit.
Since that time, the number of reports involving Maze ransomware has mushroomed. And whereas the majority of ransomware victims in the past few years typically reported that their files were locked but they had no evidence that files had actually been accessed or exfiltrated, MazeTeam is very clear that they have exfiltrated data and will dump it all. To that end, they have created web sites where they list the names of recalcitrant victims and posts samples of the data they have exfiltrated. If the victims still don’t pay up, they proceed to dump more data.
One of their victims, Southwire, did not pay the reported $6 million ransom, and took the bold step of suing the attackers in federal court after also obtaining an emergency injunction from Ireland’s High Court to compel World Hosting Farm Limited to take down their data from Maze Team’s site. As Southwire explained to its customers:
On December 31, utilizing outside counsel in the U.S. and in Ireland, Southwire was able to secure an emergency injunction from the Irish High Court. The injunction requires the defendants to remove all data relating to Southwire and its customers from its public website. Furthermore, the court’s order compels the defendants to hand over all data taken from the company and prohibits them from publishing any further material. Independently, Southwire was able to verify that the website was taken down within 24 hours of the judge issuing the order.
You can read the federal complaint here (it appears redacted that way in the docket). Not surprisingly, Maze Team simply registered two domains, hosted them on betans.ru, and proceeded with their plan, dumping 14 GB more of Southwire’s data. A notice of the new data availability was posted on a Russian forum, with the data itself being uploaded to two well-known file-sharing sites. As of today’s date, the data still appears to be available for download from those sites. As the attackers explained to BleepingComputer, the 14 GB dump was not in retaliation for Southwire’s litigation. They were simply adhering to their plan to keep dumping a percentage of the data every two weeks if Southwire didn’t negotiate with them.
In any event, as of the time of this post’s publication, both of Maze Team’s sites have been unreachable for more than 24 hours, and they inform this site that because their sites are under constant attack, they are considering their next location move. But using screenshots of files that were on their site, you can see how they attempted to name and shame one victim, crossroadsnet.biz.

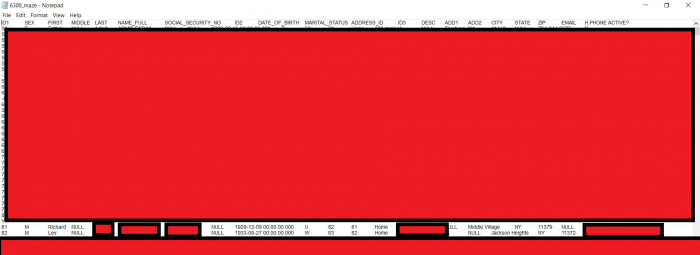
DataBreaches.net made numerous attempts to reach Crossroadsnet and Crossroads Technology to discuss the matter, but they failed to respond to all inquiries, despite the fact that it was clear that they had received the inquiries because their staff started looking me up on LinkedIn.
Because they haven’t responded, DataBreaches.net does not know what services the business provided to these individuals, most of whom appear to be senior citizens. Nor does DataBreaches.net know whether Crossroadsnet.biz has notified any of them of the breach. DataBreaches.net will update this post when more details are obtained.
Commenting on their failure to respond to inquiries or to them, Maze Team wrote:
If people cannot give us even 2 minutes to talk, it speaks either of their snobbery or their stupidity, what lesson can be learned?
All these people, I’m sure care very much about their security, but do not care about the security of their companies in the world, and we tell them, even in such a tough way, that if someone trusts your company with their data, then your company should have a conscience and responsibility to do the job well, putting their customer’s data above their laziness and greed.
And on that last point, we agree.
Health-related data and entities are not immune
While the crossroadsnet.biz sample data dump is concerning, DataBreaches.net had been even more concerned to see a listing for MDLab, a diagnostic lab that is covered by HIPAA, on Maze Team’s website. By the fact that it was listed, I assumed that they had refused to pay the extortion demand, and I reached out to them to discuss the incident. According to the news site, MDLab’s data had been locked up on December 2. Their entry on Maze Team’s site included a few files, but none containing personal or protected health information.
MDLab ignored repeated inquiries from this site. But as it turned out, they may not have refused to pay the ransom. In a statement to this site, Maze Team claimed that MDLab had tried to acquire BTC to pay them, but Coveware didn’t help them for some reason, and MDLab may have given up trying.
DataBreaches.net reached out to Coveware to ask them to explain what happened. Their CEO, Bill Siegel, responded:
Per your inquiry, we have not had any recent interaction with Maze group, and don’t have interactions with these groups outside of when we are negotiating on a clients behalf (which we would keep confidential). As a policy, if a threat actor tries to contact us to help a company, or if a company tells us that an actor referred us, we decline to assist even if the company is genuine and needs our help. Any benefit from a criminal’s referral is wrong in our book, and our policy is designed to ensure there is no ambiguity.
We realize the impact our policy may have, and we certainly feel for these victims. Whenever possible we try an point these victims to free resources or alternative service providers that may be able to assist.
Coveware’s policy makes sense from an ethical perspective, and serves as a useful and timely reminder that entities should have lawyers and incident response teams in place or contracted with prior to needing them. There are experienced law firms that can arrange to obtain BTC for clients. If there is a possibility that one day, you may decide you need to pay ransom but your internal counsel can’t handle that for you, then what arrangement has your firm made that it can quickly activate when needed? When your data are locked up and you’re given a short time period to pay up, that’s no time to start looking around for an incident response firm and external counsel. Get them in place before they’re needed, and periodically make contact with them and review your current contingency plans.
But getting back to MDLab: in response to one of the questions DataBreaches.net submitted to Maze Team, they responded that their ransom demands for MDLab were split into two parts: 100 BTC to decrypt the locked files, and 100 BTC to delete the files that they had stolen and stored. That’s more than $1.7m at today’s exchange rate. So they demanded 850 BTC (approximately $6 million) from Southwire and $1.7 million from MDLab.
Those numbers should also serve as a timely reminder to consider whether you are carrying enough cyberinsurance in the event you are successfully attacked. As previous reports on these attackers have explained, Maze Team seems to adjust the ransom amount commensurate with their assessment of the status and importance of the server to the victim. Their communications are adjusted to include reference to the following
- standalone server
- server in corporate network
- workstation in corporate network
- home computer
- primary domain controller
- backup server
- very valuable for you
Compared to Southwire, the city of Pensacola and Canadian insurance firm Andrew Agencies may have caught a break when the attackers set their ransom at $1 million and $1.1 million respectively. Andrew Agencies would later dispute Maze Team’s claim that it had acquired personal information of its customers.
Everything old is new again (extortion involving patient data)
Given this site’s special interest in breaches involving health/medical data, we asked Team Maze about their attacks in the healthcare space. In response, they provided a list of 11 entities whose names and urls are not on their news site (yet) but whom they have attacked and sent ransom demands to. From a quick assessment of the entities’s sites and data samples that Maze Team provided for two of them, it appears that not all of the entities are covered by HIPAA, but some of them are, including a radiology center in California and a cardiology center in Florida. Sample files provided for those two facilities were what you might expect: pdf files with patient name, date of birth, Social Security Number, diganosis, purpose of visit or test, insurance information, referring doctor, etc.
So far, Maze Team has not publicly dumped any data like that, but it may only be a matter of time if they continue with their present model.
A Bit About the Maze Team
So who is the Maze Team? They’ve been very courteous and professional in responding to my inquiries, and when I asked them to tell me a bit about themselves, they replied:
we are RaaS from North Korea for a limited set of people. The number of our team members is not constant.
Are they really North Koreans, though? And does it make any difference? Here’s something to think about:
If they are North Korean, are they state-sponsored at all? If it’s possible that they are, could people paying ransom to them be providing direct support to a country that the U.S. has declared a “state sponsor of terrorism?”
Although (and as we have reported previously) the federal government has never prosecuted any ransomware victim for paying ransom (nor will they, we have been told), theoretically, the government could prosecute a victim who paid ransom to an attacker if by paying the ransom, the victim was funding terrorism or otherwise providing support to terrorists.
Unlikely in this case, right? Okay, now consider this: you’re attacked and given a ransom demand. You contact your insurer who asks you what is known about the attackers. You tell them that as far as you know, they claim to be North Korean hackers. Your insurance company, who specializes in finding loopholes so they don’t have to pay out, turns around and says, “No way will we cover you for making a payment to what may be a state-sponsored actor, because that payment could be illegal.”
Could that happen? Do you know what your insurer would say or do? You might want to find out now instead of when your business is on fire. Maybe neither of those scenarios come to pass, but I included them here to get people thinking before the fact instead of after it.
Maze Team’s Model is Being More Widely Adapted
Apart from the threat that Maze Team poses, other ransomware attackers are now also adopting the “name, shame, and dump in stages” approach to reluctant or refusing victims. In the past two weeks, we’ve seen reports that the Sodinokibi and Nemty attackers are now following Maze Team’s lead or plan to. The Sodinokibi attacker(s), otherwise known as REvil, appear to have leaked data allegedly belonging to Artech Information Systems. There is no notice of any breach on that firm’s website at this time. Nemty ransomware attackers have also announced their intention to create a website.
But has the name and shame approach ever worked? Did any of Rex Mundi’s or thedarkoverlord’s victims ever change their mind and start paying them after the hackers publicly named them as victims and dumped some of their data? For the most part, I don’t think that approach really works to get recalcitrant victims to pay. If it works at all, it might serve as a cautionary tale to future victims who may decide to pay to avoid being publicly exposed as having had a breach.
So What Next?
This is only going to get worse, as I predicted last year when others were saying that things were getting better with ransomware. Even if you patch software as soon as patches are available and even if you train employees to try to avoid phishing attacks, there are so many ways for attackers to succeed. With Data Privacy Day rapidly approaching, this would be a good time for you to do something to reduce the impact of any successful attack. Can you at least remove old data from connection to your system if you can’t purge it totally? Can you encrypt old data at rest? Can you make sure you have a working backup that is not left connected to your system 24/7?
And if you need any more motivation to do something now, we will end this post by noting that within the past hour, it appears that Maze Team has dumped more than 9 GB of data from MDLab. Maze Team writes:
Yet another company refused to work with us and thought that they can get away with this.
Because MDL ( http://www.mdlab.com/ ) doesn’t want to continue the dialog we will now present to the forum members their private research data.
Check out immunology research, very interesting stuff.

We will have more on this in our next post.