Note: updates to the breaches included in this report appear below the original post.
Some threat actors have gained a lot of notoriety while others are lesser known. In this article, DataBreaches.net reports on a relatively unknown group that has been hitting the healthcare sector, “Xing Team.”
Like other groups, Xing maintains a dedicated leak site. Currently on that leak site are three large data dumps from three different medical/healthcare entities — two in the U.S., and one in Saudi Arabia.
DataBreaches.net reached out to all three entities, but received no responses. The following report should therefore be viewed as unconfirmed by the named entities, although quite a bit of data has been dumped to support such hypotheses.
GlobeMed Saudi
Xing Team claims to have acquired patient data, employee data, and financial reports from GlobeMed Saudi, a healthcare benefits management firm.

GlobeMed Saudi was first added to Xing Team’s site on May 6, and then data was dumped on May 11. Xing claims to have exfiltrated 201 GB of data, and has already dumped 100 GB.
The dumped files contain a lot of personal and sensitive information as well as routine medical records of visits, etc. As examples: one spread sheet contained information on Suspected and Confirmed Cases of Corona Virus for the period from 01-02-2021 until 11-2-2021 ( February). That file contained information on 79 named patients that included the guarantor, the hospital, the patient’s name, the individual’s number, Visa, date, the diagnosis on admission, whether a test for Corona was done, and if it was, the results. There was also a field for comments or update notes.
As one would expect, some files had multiple pages of records and follow-up.
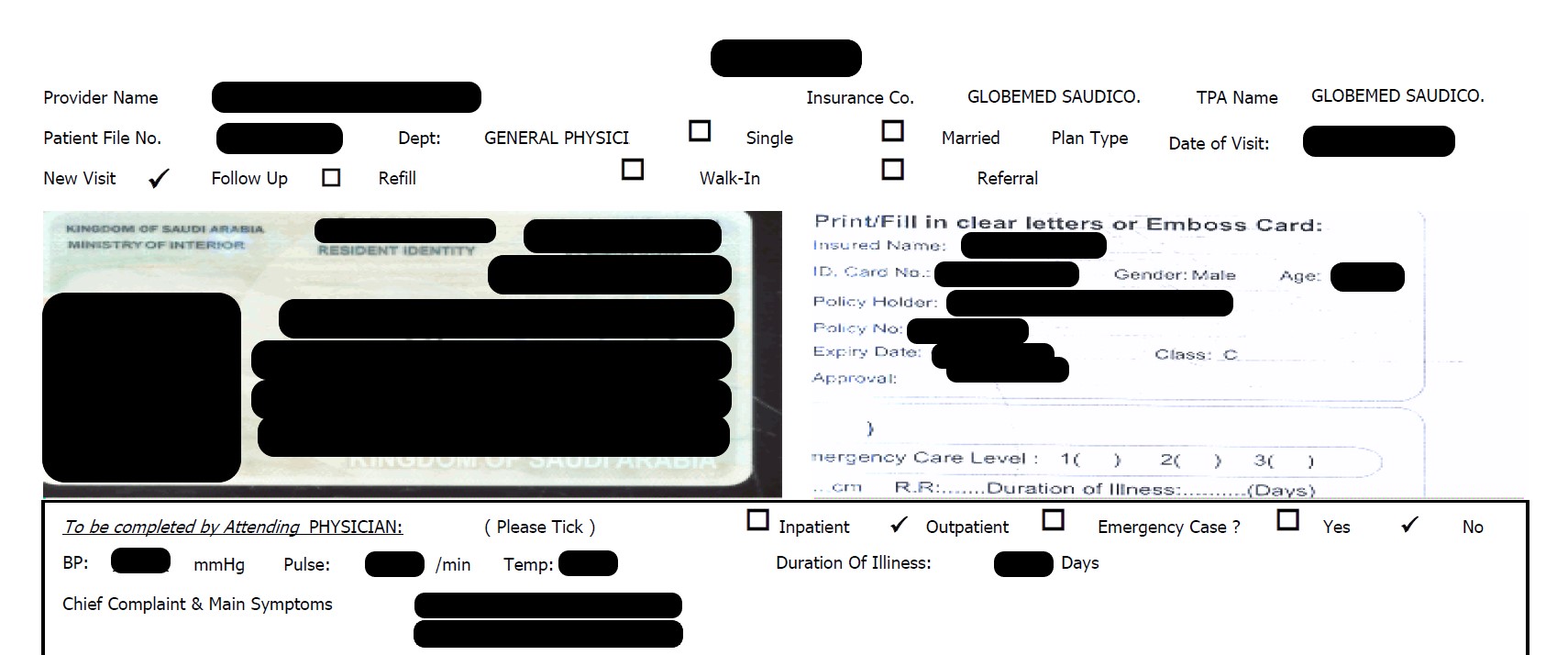
Not all files related to adult patients. DataBreaches.net noted a detailed report on a named child in a pediatric ICU unit due to a serious condition he had been born with.
Saudi Arabia does not seem to have a clear data protection regime of regulations, but there does seem to be a duty to protect patient information. GlobeMed did not answer this site’s question about whether it would be notifying patients or how it is responding to this incident.
As noted above, Xing Team dumped what they claimed was half of what they had exfiltrated. It remains to be seen if they dump more, and if so, what it contains. There have been more than 101,000 views of the listing, but there is no statistic on how many people may have downloaded data.
OSF Healthcare
According to its web site, OSF HealthCare is an integrated health system owned and operated by The Sisters of the Third Order of St. Francis, headquartered in Peoria, Illinois. They employ more than 23,000 Mission Partners in more than 350 locations, including 14 hospitals, 30 urgent care locations, and two colleges of nursing throughout Illinois and Michigan.
On June 3, Xing published all the data they claimed to have exfiltrated — 112 GB — allegedly because the
Company refused to cooperate and participants post all data here. You can get all! Emails, phones, staff data, patients information, contracts, finance information, pictures – all is available!
Inspection of the data dump revealed a mix of what appeared to be thousands of actual patient files and some test files or dummy data. One folder, called “PDF” contained almost 4,700 pdf files on patients seen at the Family Health Center. These files included ultrasounds and other maternity-related records. While there are almost 4,700 files in just that one folder, that does not represent unique patients as each named patient had numerous files. Unfortunately, even the filenames apparently revealed ePHI by incorporating patient names and type of test or record.

Another folder, called PFT, contained records from St. Paul Medical Center that appeared to relate to pulmonary testing on patients.
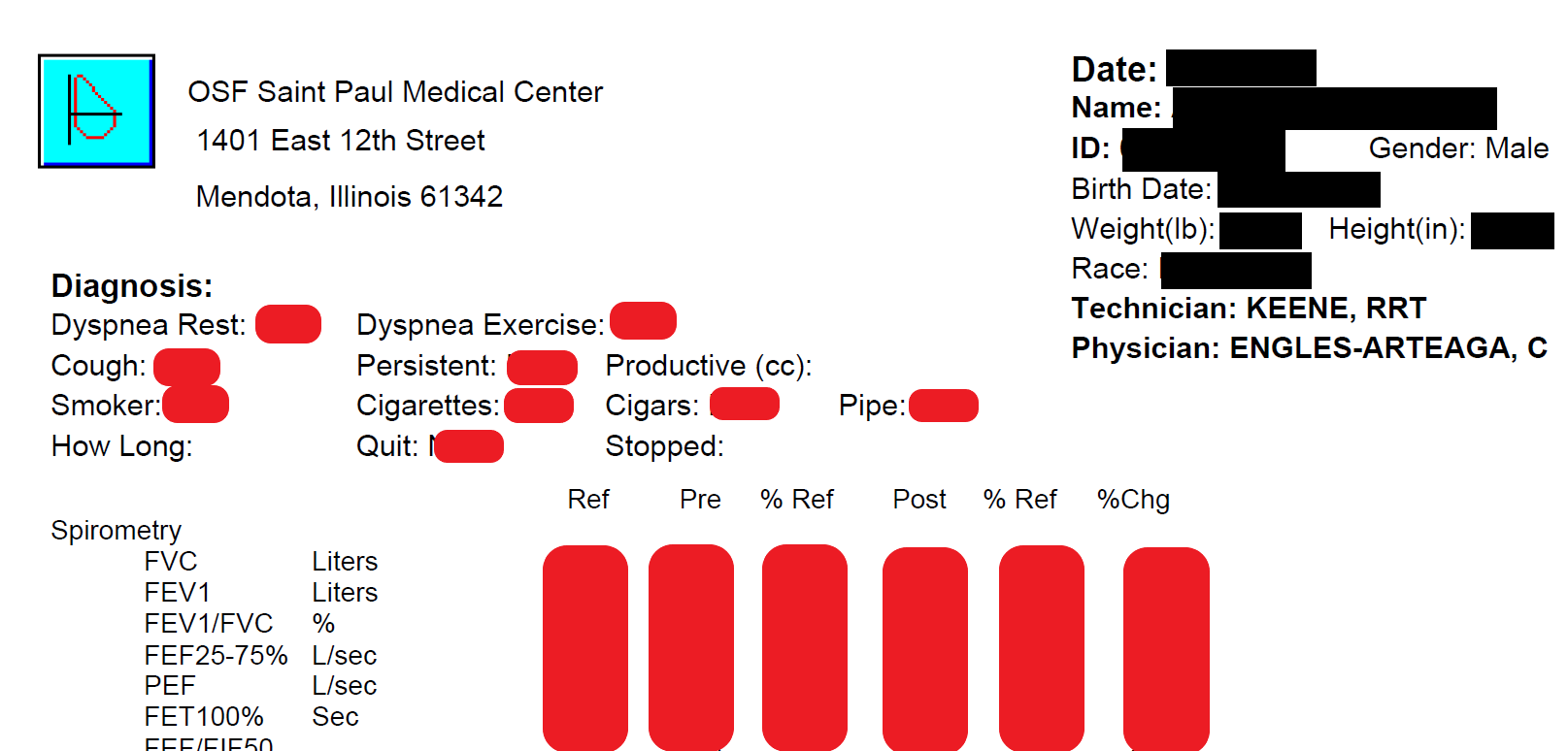
A third folder, “png’s” had more than 516,000 image files going back to 2017, sorted by month. The images were of records such as explanation of benefits statements or other patient-related files. DataBreaches.net does not know how many unique patients may be represented in that folder, but it appears OSF Healthcare may have a significant number of patients to notify about this breach.
OSF Healthcare did not respond to an email inquiry sent to it on May 20, nor to a second request sent last night.
Coastal Family Health Center
Coastal Family Health Center is in Mississippi. Xing added them to their leak site on May 24, claiming
“Company refuses to cooperate and fix a reasons of leak. That’s why we were forced to publish all information we have.”
“All information” appears to amount to 506 GB of data.
There are numerous types of files in the dump. Some are more routine business-related files, but many do have personally identifiable information including housing and financial information or protected health information such as appointment records, medical histories, insurance-related information, and lab results. A number of the files concern patients with AIDS or who are HIV+.
Another folder includes more than 900 photocopies of driver’s licenses, and yet other files relate to an arrangement between Coastal Health and a public school district to provide sports team screenings, etc.
Yet another folder, “Docs,” contains an assortment of files, most of them with personal information on patients such as their eligibility for Coastal Family Health Center’s healthcare services for homeless people. Those forms may include financial/income verification or other forms of verification.
A number of files seen by DataBreaches.net concern patients seen in April of 2021 and the first part of May, 2021.
Comments:
As of the time of this publication, none of the three entities has replied to inquiries from DataBreaches.net, and this site has not found any press releases or web site notifications concerning these breaches (although it is actually early days for data first hacked in May and dumped a week or so ago).
Xing Team is a relatively new presence in the ransomware scene. DataBreaches.net does not know much about these threat actors at this point, and has sent them an inquiry asking whether they have any exclusions in terms of who they will not attack.
For now, however, it seems clear that Xing Team feels no ethical or moral prohibition against attacking medical or healthcare entities. Whether their attacks on any of these entities impaired functioning or delivery of care to patients is not yet known, but based on this site’s review of data dumps, both OSF Healthcare and Coastal Family Health will have a lot of patients to notify after they figure out who needs to be notified.
Updates of July 5
Since the original report, DataBreaches.net was contacted by Mohammed Al Hazemi, GlobeMed Saudi’s Compliance Manager. When they investigated, they discovered that this site had, indeed, attempted to contact them, but that the inquiries had gone to spam. Hopefully they will create a press/media contact email address so that they don’t have this problem in the future.
In any event, GlobeMed Saudi reports that the firm’s IT security team had promptly initiated an incident response followed by a “threat hunting exercise” over their network. As a result of their response, the data center environment and core systems were not affected and the spread was contained, they report.
In response to my question about notifications, they replied that they
…immediately notified the concerned KSA authorities, regulators and the affected entities of about the incident. GlobeMed Saudi contained the breach within 24 hours, and has taken all measures to reinforce its security and cyber policies and tools to maximum protection.
GlobeMed Saudi also requested that this site remove the screencaps and other analytic details from the reporting. DataBreaches.net respectfully declines to do so. This site sees no reason to treat their breach any differently than any other breach or ransomware attack this site has covered.
There is also an update to the Coastal Family Health Center breach. This week, they issued a press release. It did not reveal that 506 GB of files had been dumped on the dark web. DataBreaches.net recognizes that there is no statutory or regulatory requirement that entities reveal data is dumped, but if the purpose of disclosure is to inform people so that they can protect themselves, then I continue to believe they should be told such things so that they can better understand the situation and risks now and in the future.
The Coastal Family Health Center incident has not yet shown up on HHS’s public breach tool. Neither has the OSF Healthcare incident.