Clover Park School District in Washington state is only one of several k-12 districts recently attacked by threat actors calling themselves “Grief.” The same threat actors also attacked Booneville School District in Mississippi and Lancaster Independent School District in Texas. Note that DataBreaches.net has no information or confirmation to indicate whether either of the victims had their files encrypted by the threat actors.
Booneville School District, MS
The threat actors first added Booneville to their leak site on June 30, and recently added files to the data dump. Their listing confusingly says:
Booneville School District is located in Booneville, MS, United States and is part of the Public Schools K-12 Industry. Booneville School District has 125 total employees across all of its locations and generates $8.31 million in sales (USD). (Sales figure is modelled). There are 6 companies in the Booneville School District corporate family.
Sales? A k-12 district? 6 companies? Do they mean schools?
In any event, the data that Grief has dumped so far is mostly, well, to be blunt, garbage. There are four folders with student-related information. The folders have files for named students that contain some of their work or exercises. In a subset of the writings, students may reveal personal information about themselves or their families, but there are no spread sheets with demographic or educational records in the dump. So other than a few files with personal narratives, most of the data (student names) might be directory information under FERPA anyway.
Could the threat actors have more data that would be concerning? Perhaps, but it may be unlikely as they listed Booneville under their “Complete Grief” list.
DataBreaches.net emailed the district to request a statement and additional information, but no reply has been received. This post may be updated if a reply is received.
Lancaster ISD, TX

Grief’s attack on Lancaster ISD was more extensive. The threat actors wrote:
The network of Lancaster Independent School District was screwed and now we have about 9 GB data from file servers, including internal company documents, personal and customers data. According to our rules we are publishing this data step by step in case if this company will keep silence.
Lancaster Independent School District is a public school district based in Lancaster, Texas. The district serves most of the city of Lancaster, a small portion of Dallas, and a small portion of the city of Hutchins.
Well, no, it’s not a company and there are no customers, but they seem to have exfiltrated some data that would be of concern to the district. While many of the files relate to routine district operations and budgeting that would be publicly available on request, other files contain employee demographic information for current and former employees, payroll information, banking information, Social Security numbers, and other Human Resources-related files such as termination letters and requests for leave, etc.

Some files were quite extensive, such as one employee’s file that was more than 140 pages of personal and professional information.
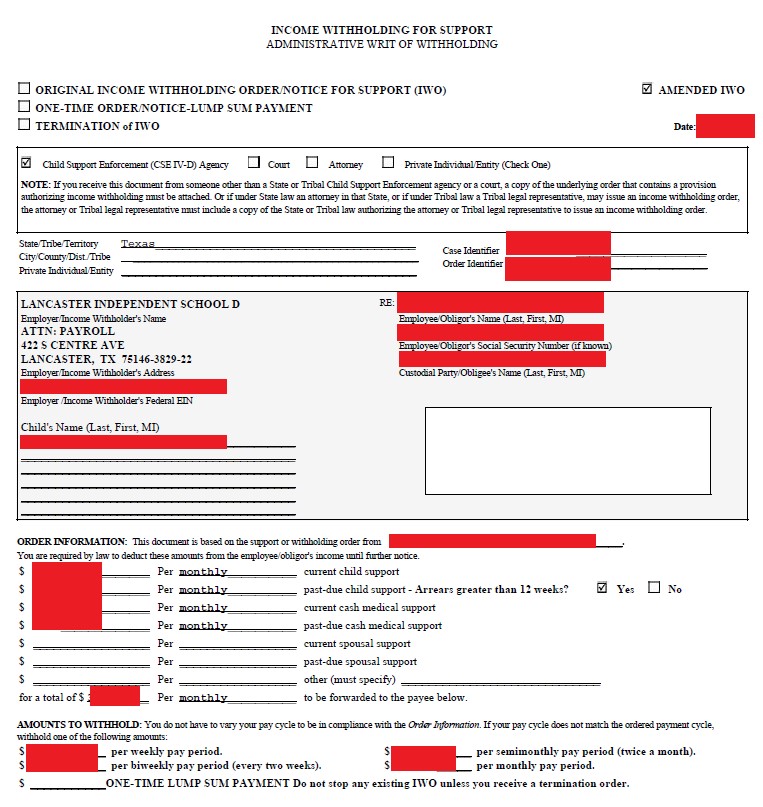
As we found with Clover Park, there were also files with personal and sensitive information relating to employees that are old files where many were probably not needed for current functions. A folder of files concerning child support included orders for the district to garnish certain employees’ wages for past-due child support. Those files — more than a decade old in most cases — contained an employee’s name, SSN, the name of the child for whom support was owed, and the amounts to be garnished, as the following image depicts:
We did not observe any databases or spreadsheets with student information, but personal information on some students was exposed in the files relating to child support payments as well as files relating to the district’s free or reduced-cost lunch program. The district required information on the parents’ income and other details so they could determine or verify eligibility for the program.
DataBreaches.net sent an email to Lancaster asking them for a statement about the incident and their response to it, but no response has been received, and there is no statement on their web site that we could find.
Clover Park in Washington, Booneville in Mississippi, and Lancaster in Texas are just three recent k-12 attacks. In an upcomng post, we will report on yet another Texas district that was attacked by a different group of threat actors. Like the Lancaster, breach, the other Texas breach also involved a lot of information on employees. But in the upcoming report, you will see a lot of student files were involved as well.
Reporting by Dissent and Chum1ng0