Update of September 4: Sandhills subsequently issued a press release that indicates that they could not confirm that the data came from them. See the follow-up report here.
Original post:
Sandhills Center in North Carolina manages public mental health, intellectual/developmental disabilities and substance use disorder services for the citizens of Anson, Guilford, Harnett, Hoke, Lee, Montgomery, Moore, Randolph and Richmond counties. As a publicly-funded Local Management Entity-Managed Care Organization (LME-MCO), Sandhills Center does not provide services directly, but describes itself as an agent of the North Carolina Department of Health & Human Services (NCDHHS).
On some date unknown to DataBreaches.net, Sandhills Center was allegedly hacked by threat actors who claim to have exfiltrated 634 GB of data. The incident is posted on a web site run by “Marketo,” who auction or sell data from incidents. For each listing, Marketo generally provides a small sample of data as proof of claims. As of today, Marketo claims to have received 137 bids for the Sandhills Center data. Their claims about bids are not possible for this site to verify or refute.

In this case, the “proof pack” offered by Marketo was a confusing compilation of files that did not provide any compelling evidence that the files came from Sandhills Center or that the attackers had acquired any personal information on clients or employees. DataBreaches.net requested more proof, and was sent a second archive of files that did contain records that had Sandhills Center letterhead and other materials that are consistent with the Center’s mission and description.
DataBreaches.net first reached out to Sandhills Center via their web site contact form on July 21, but received no reply. An email inquiry was subsequently sent to multiple executives of the center including their compliance officer, but that, too, has received no reply.
Of note, a lot of the files in the second proof pack were quite old. This is not to say that the threat actor(s) didn’t obtain recent data, as DataBreaches.net can neither confirm nor deny that, but what this site did see were records that may not have been needed at all in recent years and yet they were either still on Sandhills’ server or somehow connected to the internet.
The image below is captured from the top of a four-page report on a high school student. The evaluation was conducted in May, 1993, and included intelligence tests, visuomotor integration test, and a behavior rating scale.
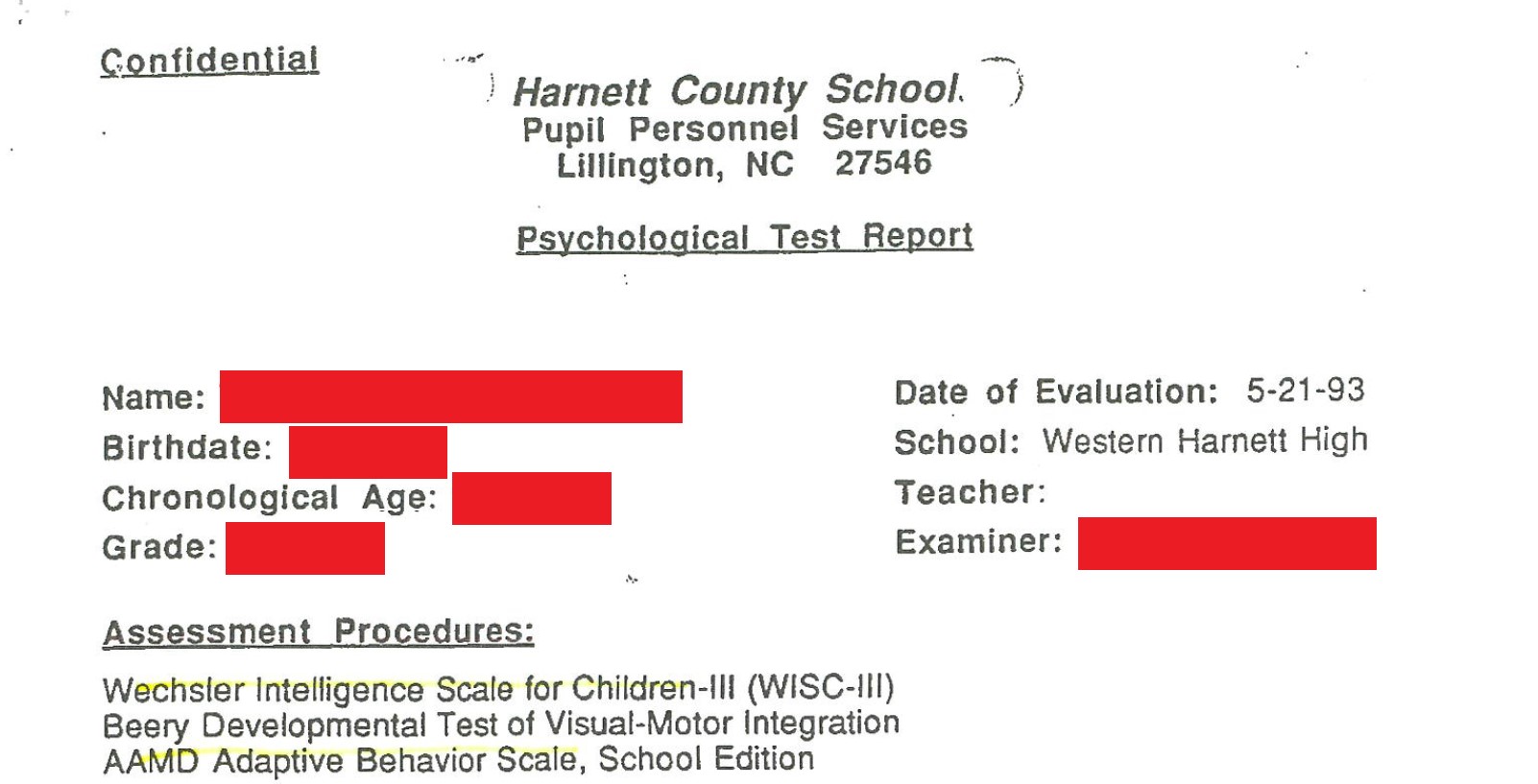
The student was 16 years-old at the time. It is now 28 years later, and these test results and evaluation on were still on Sandhills’ server with insufficient security to protect them from being stolen.
I do not know North Carolina’s records retention and destruction laws but it seems a bit improbable that a psychoeducational evaluation of a high school student conducted more than 20 years ago would still need to be retained. But if it does need to be retained, then why was it unencrypted and why was it on a server connected to the internet?
DataBreaches.net reached out to the state agency that Sandhills Center claims to be an agent for. NCDHHS was asked who would be responsible for notifications if Sandhills Center had a breach involving personal information. DataBreaches.net also asked the state to point this site to the state’s data retention laws that might apply. As of the time of this publication, the state has not replied to those inquiries.
One of the questions DataBreaches.net did not raise in the emails to the center and the state is to ask how more than 600 GB of files could have been exfiltrated without any alarm system or alert going off to warn Sandhills of a security issue. If HHS/CMS or the state of North Carolina investigates and confirms massive data exfiltration, hopefully they will look into that and what additional security measures Sandhills Center might need to deploy going forward.
DataBreaches.net notes that not all of the files in the second proof pack involved youth or students. Sandhills also arranges for services for adults who are developmentally or intellectually disabled and may need housing or vocational rehabilitation or training programs. They also are required to give preference to pregnant women who need mental health or treatment services, including referrals for prenatal care.
The screencap below is just the top of a multi-page report assessing an adult for potential vocational rehabilitation services. The evaluation took place in 2007. Was it necessary to keep it on a server connected to the internet in 2021?

Another file in the material made available exclusively to DataBreaches.net appeared to contain demographic information on more than 42,600 people in the counties Sandhills serves.
This breach will likely be an utter nightmare in terms of incident response because even if the state or Sandhills Center agrees that notifications need to be made, some of these files are so old that tracking down people may be impossible, and all that the state or Sandhills may wind up doing is issuing a press release or substitute notice that will be so vague that even if people do see it and read it, they may have no idea what information of theirs is involved, if any.
Will those who had SSN or Medicaid numbers in the files with other identity information be notified and offered any protective services?
If the state or Sandhills Center responds to any of the inquiries sent to them, this post will be updated.