—– A DataBreaches.net report by Dissent and Chum1ng0 —–
In Part 1 of this series, DataBreaches.net described a number of attacks by Pysa (mespinoza) threat actors on medical entities in the U.S. In Part 2, we look at eight k-12 public school districts in the U.S. who either appear on the threat actors’ dedicated leak site or were known to have been attacked by them. Some of the districts discussed in this post became victims before the FBI published an alert in March about Pysa hitting the education sector, but some became victims after the alert was published.
As a preface, we note that Pysa are not the only ransomware threat actors attacking the k-12 sector, which has a reputation of being “low-hanging fruit” for hacks. We have also seen many other groups attacking k-12 districts. A partial listing of ransomware attacks on k-12 is embedded below this discussion of Pysa victims.
Affton School District (Missouri)
Affton School District was added to Pysa’s leak site with a date stamp of February 25, 2021. Pysa mocked the district, who had publicly acknowledged the breach that day, because in a notice on the district’s site, they wrote:
We do not believe any sensitive information has been accessed and no personal data, financial information, or grades have been found to be compromised. As a routine layer of protection, this information is stored on offsite servers. — Dr. Travis Bracht
The Affton data dump was in two parts. One part contained 1099 tax statements but the 1099’s seemed to be for a softball association as the payor. There were .doc files, however, for district personnel that contained SSN, including new hires dated from 2010–2020 with employees’ name, address, date of birth, position, starting salary, and SSN. Another file from 2018 includes some of the same information but also included phone number and work email addresses.
DataBreaches.net was unable to find any updates to the district’s February statement online, but on April 1, the district filed a notification with Maine Attorney General’s Office (because a Maine resident had been impacted by the breach). As reported previously on this site , the district reported that a total of 1,183 people were impacted by the breach.
Since its earliest statement, we had not seen any statement from the district either denying or confirming whether any student or parent information was impacted, so DataBreaches.net sent an email inquiry. In response, Erica Chandler, the district’s Director of Communications, responded that the district had notified employees, but had not notified students or parents “because student information was not compromised.”
Gering Public Schools (Nebraska)
Gering Public Schools was added to Pysa’s web site with a date stamp of February 24, 2021.
The district subsequently reported a breach to the Montana Attorney General’s Office on March 24, 2021. The metadata with the report (see image below) indicated that the attack occurred a year earlier (March 25, 2020).
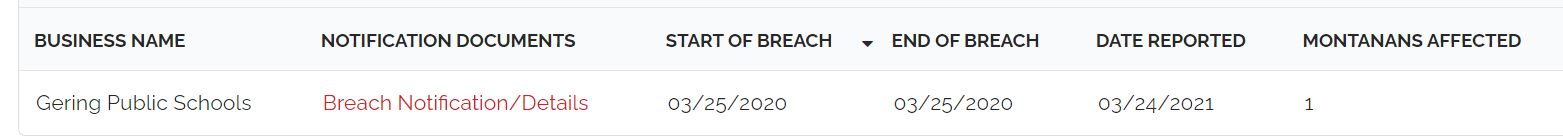
There was no explanation for a one-year delay in notification, and in its notification, the district claimed that it “recently learned” of a data security incident. Is it possible the district only learned after February 24, 2021 if they were added to Pysa’s leak site then? Had their data been encrypted but they had not known they were the victims of a ransomware incident? Perhaps. The notification letter does not tell the recipients when the incident actually occurred.
GPS’s notification says that the threat actor “accessed computer systems that contain some personnel information, which may have included your Social Security number, financial account information, health insurance information, or medical information.”
DataBreaches.net could find no notice on the district’s web site.
The notification makes no mention of student data, but inspection of the data dump revealed lists of students with 504 accommodation plans as well as four years of master lists of IEP students with name, address, date of birth, parent information, type of educational disability, whether a behavior plan was also being developed for the student, and post-school outcomes. The 504 data and IEP data contain education records that are protected under FERPA. While FERPA does not have a blanket requirement that students or their parents must be notified of data breaches, we would hope that the district did make notifications.
GPS did not respond to email inquiries sent this past week about that.
Zionsville Community Schools (Indiana)
Zionsville Community Schools was added to Pysa’s leak site with a date of May 2, 2021. Despite being added to Pysa’s site, however, Pysa’s data dump is not from Zionsville and appears to be from another one of Pysa’s victims.
Pysa did not respond to an inquiry sent to them about the claimed attack. Nor did the district respond to a contact form inquiry of August 2 or an email of August 7. We can find no notice on their web site, no media coverage, and no report to their state attorney general’s office.
At this point then, we consider this claimed attack unconfirmed.
Palos Community Consolidated School District 118 (Illinois)
Palos Community Consolidated School District 118 was added to Pysa’s leak site on December 9, 2020.
Most of the data in the data dump appeared to relate to personnel. There were dozens of scanned tax forms for federal and state returns that contained employee information such as SSN. We also noted a spreadsheet with names, addresses, birthdays, cell phone numbers, and home phone numbers of employees. Other files contained more sensitive personnel information such as complaints about harassment.
There were also files with student information for the past few years. Some of the information in these files would be education records that should be protected under FERPA. There was no indication of any student databases being dumped, however.
In response to inquiries from this site, Yvonne Leschkies, the district’s FOIA Officer, provided the following statement:
On December 3, the school district was the victim of a cyber-attack, the second such attack this year. As with the previous attack, with the help of our cyber-insurance team, we immediately reached out to and engaged professionals with significant experience in responding to cyber-attacks for assistance in containing, remediating, and investigating the incident. We focused, first and foremost, on containing the incident and attempting to make sure our systems were no longer at risk from this attacker. Based on our experts’ information, we believe the incident is now contained, and our systems are not at further risk of compromise related to this attack.
Based on our investigation, we have no reason to believe that our student database or financial software system was breached or otherwise compromised. Likewise, based on our investigation, we have no reason to believe that personally identifiable student or staff information was breached or otherwise compromised.
Fortunately, our Technology Department put in additional security measures after the first attack that has allowed them to restore systems quickly in response to this incident, so we expect any adverse impact on our operations to be minimal. Palos 118 is not alone in the fight against cyberattacks. School districts are increasingly targets of cyberattacks as technology has become more essential to operating schools amid the ongoing pandemic. We continue to work with our outside experts in an effort to harden our information security and reduce the threat against these types of attacks in the future.
Except…. we saw personnel and student information in the dump, so why are they saying that, ” we have no reason to believe that personally identifiable student or staff information was breached or otherwise compromised?”
Brookfield Public Schools (Connecticut)
Brookfield Public Schools was added to Pysa’s site on December 1, 2020. We could not find any media coverage or notice on their web site about any incident.
Pysa’s data dump was a relatively small one with employee information for a few years, including SSN. There was also login information for the district. Hopefully, they changed their passwords for their Confidential system; the file was last updated January 30, 2020.
The district has not replied to email inquiries sent to them on August 3 and August 6.
Winters Independent School District (Texas)
Winters ISD was added to Pysa’s site with a date of October 25, 2020.
The data dump from Pysa was, to put it frankly, a mess. We were able to download the dump from Pysa, but trying to describe or analyze the data is a bit of a head-scratcher. The folders generally did not have meaningful names or organization, and many files of all different types just seemed dumped together, including scans of some students’ birth certificates.
Most of the files in this dump did not even really seem to deal with education or academics, although there were spreadsheets from 2018 that listed every student by name, date of birth and with their district ID, username, and password. And apart from the birth certificates, there were occasional files with social security numbers.
Many files dealt with calculating what the district earned or spent on sports events, a number of files dealt with tardy attendance, and a lot of files dealt with law enforcement forms for probable cause, felony warrants, arrests, and voluntary statements by those arrested. One arrest-related form was actually filled in, but seemed to deal with a domestic disturbance and did not seem to have anything to do with any student. Why the district had so many files and templates for criminally related behavior and law enforcement left us wondering what goes on in that district.
Overall, there were only a few files with the kinds of personal information on students and employees that would generally require notification, but this particular dump would not necessarily impact a lot of individuals. DataBreaches.net does not know what other data Pysa may have exfiltrated.
We could not find any statement on Winters’ web site or Facebook page. Nor could we find any media coverage, and the district did not respond to emails sent to them on August 2 and August 5.
Sheldon ISD (Texas)
Sheldon ISD is not listed on Pysa’s dedicated leak site — because the district paid them ransom. As this site reported in August of 2020, the attack occurred in March of 2020 and:
The impacted information differs for current and former students and across individuals, but generally included information such as: a student’s name; year in school; school name; teacher name; sex; race; test scores; and English language proficiency. The documents did not contain Social Security Numbers or any other similarly sensitive personal information for current or former students.
The district reportedly paid nearly $207,000.00 in in ransom.
Logansport Community School Corporation (Indiana)
Logansport Community School Corporation was added to Pysa’s leak site on May 8 with a date of April 11, 2021.
A notice on the district’s site dated April 23, 2021 acknowledged a data security incident that was impacting their systems, but did not provide any specifics. There has been no update on their web site since then, but media coverage on WLFI on April 27 reported that it was a ransomware incident and that the internet and phone systems in every building had been shut down by the threat actors on April 11.
When Pysa dumped data, DataBreaches.net reported it , but there has been no media coverage or disclosures by the district since then that we could find.
Review of some parts of the 40-GB data dump revealed personal and sensitive education records on students such as a psychological evaluation of a student, a preschool referral form on another child, an Individualized Family Service Plan for another child, and multidisciplinary reports on other students. There were also 504 accommodation plans for students, and a behavior letter for a named student about his potty needs and behavior and why the school program could not handle him.
Many of these files were older files, and one wonders how a former student would feel if an old report about his potty training were to be circulating on the internet now.
These files would all be covered by the Family Educational Rights and Privacy Act (FERPA). FERPA does not actually require districts to notify parents of breaches, although the district should be required to make a note in the student’s file about the disclosure. We do not know if Logansport has made any notations or feels that they are required to do so.
In addition to student-related files, most of which are not described above, there were also personnel files, and again, many of them were not current files.
DataBreaches.net emailed the district on August 2 and again on August 5 to ask for an update. No response has been received, so we do not know how many former or current employees may have been notified of this incident already (if at all), or how many students or parents may have been notified.
Comment:
By now, readers will have noticed that we do not have detailed reports or any numbers for most of these incidents. Notifications and disclosures under FERPA are not required, and many states do not require school districts, as state entities, to disclose breaches.
With one exception, neither the districts nor Pysa disclosed the amounts of the ransom demands, but we know that the cost of not having adequate security can be staggering. This week, as just one example, we learned that Judson ISD in Texas paid hackers more than $547,000 just to get unidentified threat actors not to dump stolen data publicly. More than half a million dollars just for that, and that’s apart from restoring files and replacing any hardware, consulting fees, mitigation services fees, and mores. Similarly, we know that incident response costs for Baltimore Public Schools is already more than $8 million following their ransomware incident. We have not been told who the attackers were for each of those incidents.
So we have a serious problem with weak data security in k-12 districts, and costly attacks, and the public does not truly have a good estimate of how many incidents, how many people impacted, and at what cost.
The K-12 Cyber Map tries to track k-12 breaches, but as dedicated as Doug Levin is, he cannot track what is not disclosed. It is time school districts, which rely on public funding, become more accountable by publicly disclosing breaches and costs.
Ransomware attacks are just one part of the bigger picture of attacks on the education sector. See also: Schools Brace for More Cyberattacks After Record in 2020 (Bloomberg CityLab, August 9, 2021):
Reported hacking incidents have increased nearly fivefold since 2016. Virtual learning during the pandemic created even more access points for attackers.
k-12_Ransomware_Attacks
Research by Chum1ng0 and Dissent; writing by Dissent.