“Full ICU at Missouri Delta Medical Center, workers scramble to keep up with COVID-19 surge,” a headline informed us earlier this week.
And if they weren’t struggling enough already, it appears that Missouri Delta Medical Center (MDMC) might also be dealing with a ransomware attack by Hive threat actors. So far, however, MDMC has been tight-lipped about the claimed attack and has not responded to inquiries asking them to confirm or deny the claim.
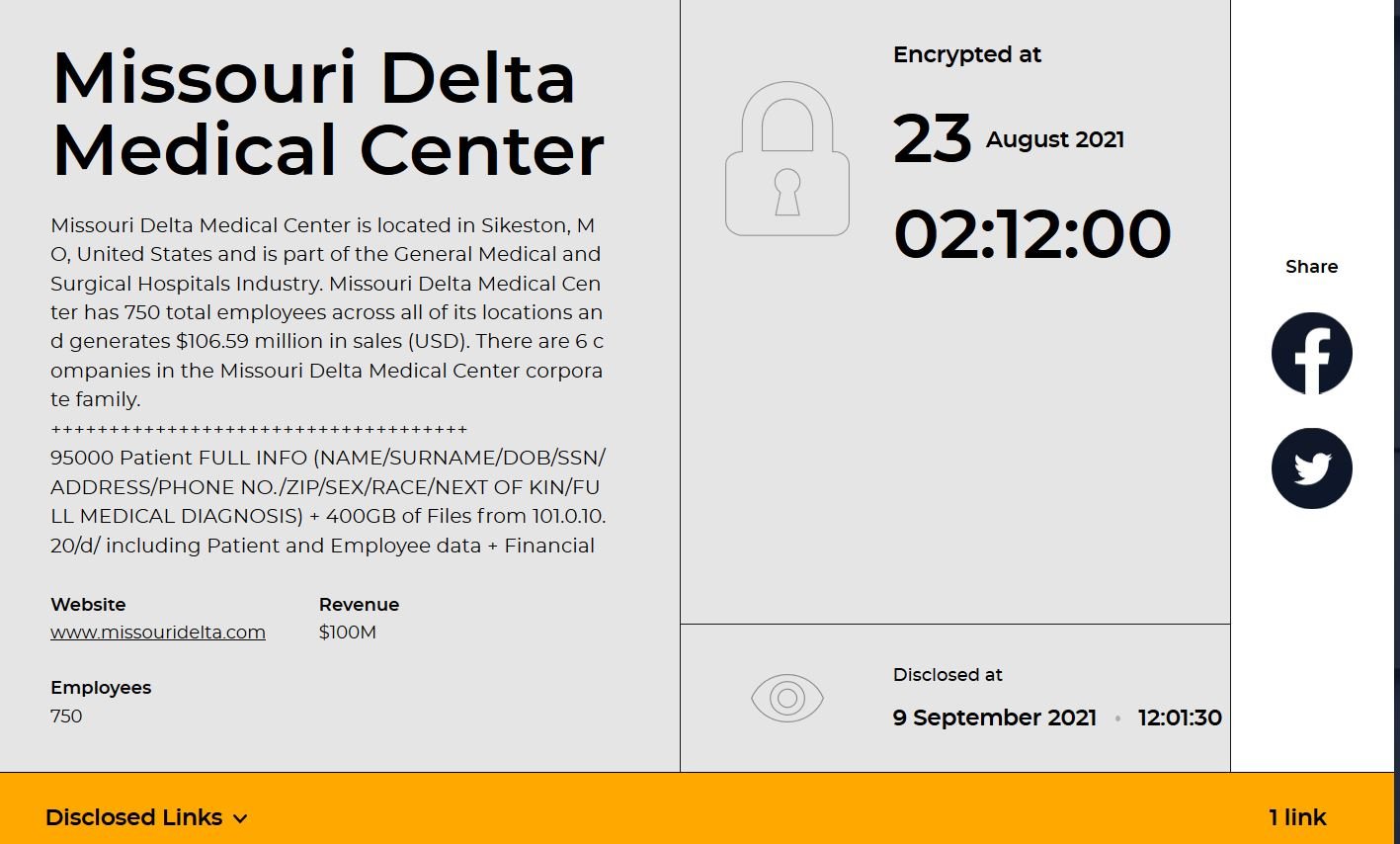
Hive claimed that they encrypted MDMC’s files on August 23. They also claim that they had exfiltrated
95000 Patient FULL INFO (NAME/SURNAME/DOB/SSN/ADDRESS/PHONE NO./ZIP/SEX/RACE/NEXT OF KIN/FULL MEDICAL DIAGNOSIS) + 400GB of Files from [Redacted by DataBreaches.net] including Patient and Employee data + Financial
DataBreaches.net sent an inquiry to MDMC on August 31 and received an acknowledgement of submission, but no answer to the request asking them to confirm or deny the claimed attack.
This site sent a second inquiry to MDMC this week and again got a confirmation of submission, but again, there was no substantive response.
Hive Starts Dumping Data
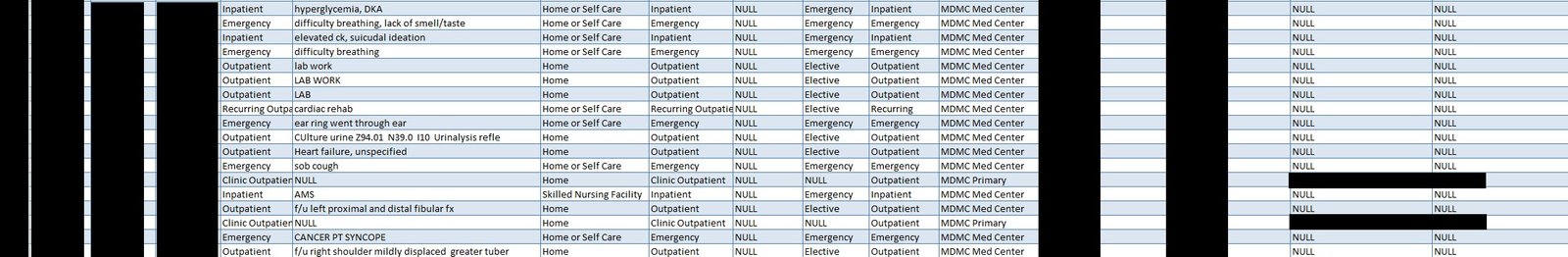
On Friday night, Hive dumped data allegedly from MDMC. Inspection of the data appeared to confirm their claim that the data are from MDMC. They included two screencaps of what was to come. One of them, below, has protected health information redacted by DataBreaches.net:
There was also a 10 GB dump of what they call “random” files.
The dump included folders with PII and PHI that go back years. As just two examples of the types of files in the first data dump:
One folder from 2017 contained scanned multi-page documents used for billing for anesthesiology services. Each log included the date of operation, what service the patient was on (e.g., orthopedics, obstetrics, etc.), the patient’s name and gender, the patient’s pre-operative diagnosis and post-operative diagnosis, their medical record number, the type of procedure, length of time of anesthesia and what type of anesthesia, the name of the surgeon, and other details.
The log files all said:
OR Log
MDMC OR
at the top of log pages, and had the MDMC logo on the bottom of the pages. Companion CRNA Anesthesia Billing pages in each file had “Missouri Delta Medical Center” and logo at the top of the pages.
One directory in the dump had 62 folders with admission data by day. Each folder covered multiple dates. The register sheets for each day had the date of admission, the patient’s name, their account number, their diagnosis, what room they were in and what bed number, and their admitting physician. The folders ranged in dates from 2006 to 2013.
Other folders dealt with insurance billings and other matters. DataBreaches.net did not examine all the files — only enough to determine that the data did appear to come from MDMC or related to their patients. Not all of the folders in the dump had actual contents.
Hive’s dump had been posted on a popular file-sharing site and appeared to be removed fairly quickly, but if what was dumped on Friday is only 10 GB of what Hive claims is a 400 GB dump, then there may be much more to come, although it may not necessarily be personally identifiable information or protected health information. It is also possible that the data are not from MDMC’s system but from that of a business associate or vendor, but until MDMC responds, it will not be clear. What is clear, however, is that there are files that appear to be patient files with MDMC’s name and logo all over them.
Since their initial announcement about MDMC, Hive appeared to have edited their leak site listing to now read:
MDMC Decided not to protect privacy of their patients or employees. By their greed for money, patients will suffer. There is still time – 4 days until all patient info is dumped.
++++++++++++++++++++++++++++++++++++
In upcoming dumps will be:184355 Patient FULL INFO (NAME/SURNAME/DOB/SSN/ADDRESS/PHONE NO./ZIP/SEX/RACE/NEXT OF KIN/FULL MEDICAL DIAGNOSIS) + 400GB of Files including Patient and Employee data + Financial
That 4-day warning was posted two days ago and the listing is still up, so it seems there has been no payment or negotiations.
DataBreaches.net notified MDMC yesterday that despite the absence of any response from them to multiple inquiries, this site would be publishing about the breach because patient data is being dumped and patients need to be warned so that they can take steps to protect themselves.
As of the time of this publication, there is still no response from MDMC and no statement on their web site to alert patients to any possible data security incident. This post will be updated if a response is received.