There’s a fascinating blog post out today by Gemini Advisory. Here are just the key findings to give you a sense of it all:
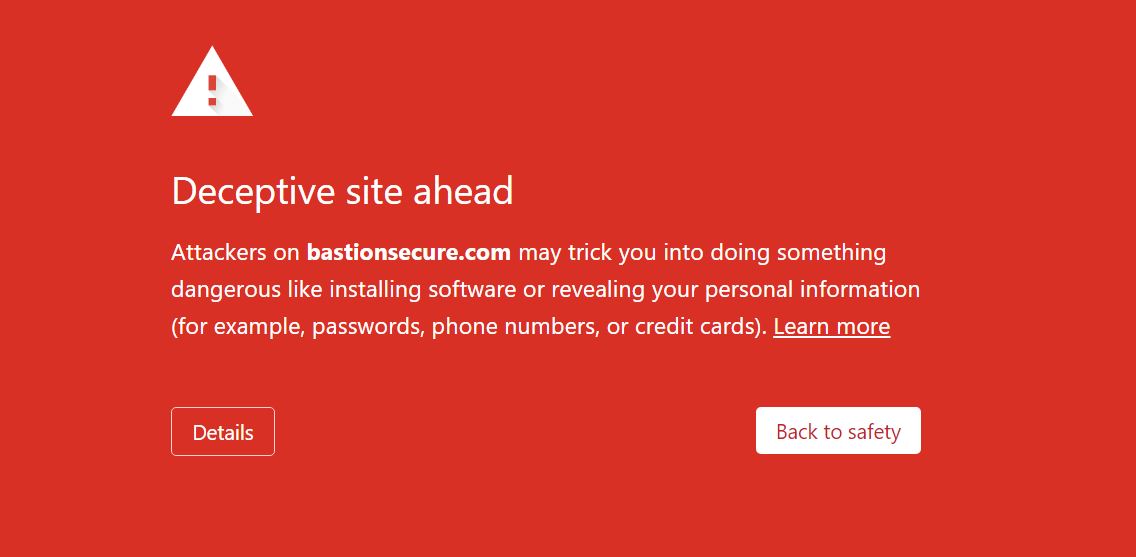
- The cybercriminal group FIN7 has been responsible for large-scale card theft campaigns, resulting in the exposure of over 20 million payment card records, as well as ransomware attacks. Gemini has discovered that FIN7 is now running a new fake company called “Bastion Secure”, replacing the previously reported “Combi Security”.
- Bastion Secure offered a job offer to a Gemini source and, in the process, provided the source with files that analysts later determined were for the post-exploitation tools Carbanak and Lizar/Tirion. These two tools have been previously attributed to FIN7 and establish the link between Bastion Secure and FIN7.
- The tasks that were assigned to the Gemini source by FIN7—operating under the guise of Bastion Secure—matched the steps taken to prepare a ransomware attack, providing further evidence that FIN7 has continued to expand into the ransomware sphere.
- FIN7 can pay unwitting “employees” far less than it would have to pay informed criminal accomplices for its ransomware schemes. However, FIN7’s greed also afforded Gemini a view into the proprietary data of this prolific threat team, leading to the exposure of another fake FIN7 company.