It’s one thing to ignore ransom demands from threat actors, but how smart — or foolish — is it to be sarcastic or insulting to those who have exfiltrated files with your patients’ protected health information?
DataBreaches.net was recently contacted by threat actors who were previously associated with other groups. They claimed to have attacked Compton and Broomhead Dental Center in Indiana (C&B Dental Center) on October 8 and to have exfiltrated patient files.
When DataBreaches.net checked, we could find no incident on HHS’s public breach tool. Nor could we find any report on the Indiana Attorney General’s Office breach site (although that site has not been updated since last August). There has been no public notice that has been indexed by Google, and there is no notice on the dental practice’s website. So three months after the attack, there does not appear to have been any public notice or disclosure.
A spokesperson for the threat actors provided this site with proof of claims — in fact, they provided more than 4,200 files with PHI. The files had C&B’s name at the top of each page.
DataBreaches.net did not contact patients directly (this site tries to avoid that), but using a sample of files, confirmed via Google searches and SSN validation that there are real people with those names at those addresses. This site also confirmed that Social Security Numbers found in the patient files are valid SSNs from states and time periods that would be consistent with the patients’ reported dates of birth.
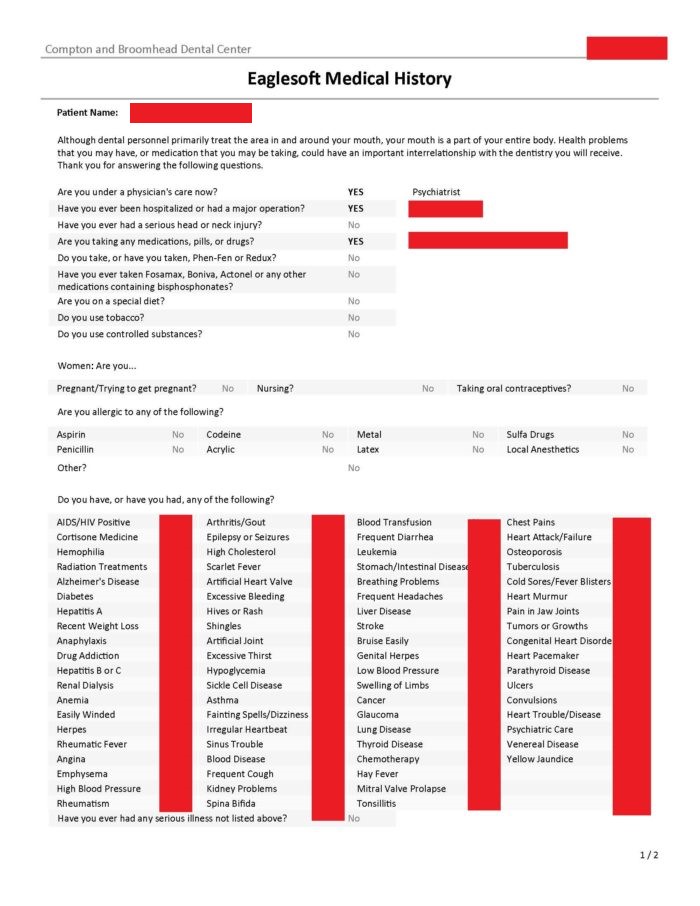
Some files provided to this site contained patients’ names and medical history screening. The screening was not confined to dental issues but inquired about all systems. The incompletely redacted image below demonstrates that the screening included mental health issues. This patient’s psychotropic medications were listed on the form and have been redacted.
Other files contained demographic information and health insurance information including name, address, date of birth, social security number, health insurance plan name, subscriber ID, group number, driver’s license number, name and location of employer, and secondary health insurance information.
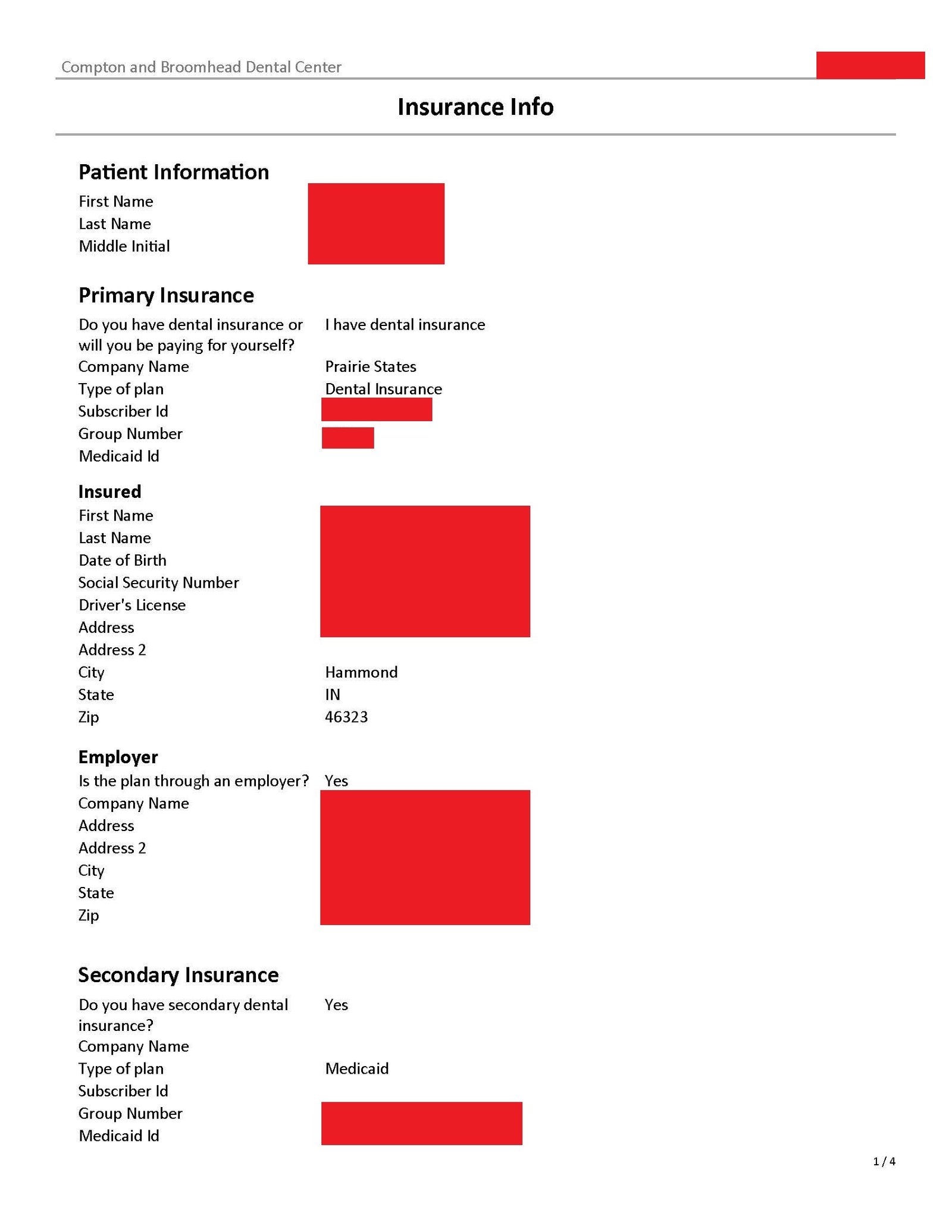
A third file provided to this site contained some patients’ names, phone numbers, and email addresses.
According to the threat actors, they did not encrypt the practice’s files.
On January 5, DataBreaches.net sent inquiries to C&B via their website’s contact form and then via direct email to both Dr. Compton and their marketing person. In the contact form message, this site included two filenames and the corresponding patients’ initials so that C&B could confirm the validity of the claimed breach if they had not already confirmed it. In the email, C&B was asked whether they had notified HHS and the Indiana Attorney General’s Office. They were also asked whether they notified patients or what they had done in the way of incident response.
No replies at all have been received.
A spokesperson for the threat actors claims that they had only limited interaction with what might have been an IT provider for the practice but there were no negotiations over any payment and that at times, the person or persons were somewhat sarcastic. After contacting some employees’ families, as one example, someone responded to them, “Oooh what are you gonna do. Remind them when their dental cleanings are?”

That seems unlikely, but the spokesperson informs this site that their plan includes dumping all of the patient data if there is no payment. It’s a threat — and an outcome — that we have seen a lot in the past few years.
Updated Jan. 10: It looks like the threat actors either dumped the data publicly (and if they did, I do not yet know where they dumped it) or they gave it to someone who has now leaked it on a popular forum while claiming it had been publicly dumped.
Updated Jan. 11: An image that appeared previously in this post was incompletely redacted and has been corrected. DataBreaches.net regrets the error.