Q: What’s worse than a really bad data breach involving patient and employee data?
A: A really bad data breach where the data gets leaked on the internet for everyone to grab for free.

In June 2021, DataBreaches.net reached out to Sea Mar Community Health Centers in Washington to alert them to what appeared to be a leak of some patient data on Marketo — a marketplace for stolen and leaked data.
Sea Mar never responded to that notification or multiple subsequent notifications and queries by DataBreaches.net. Sea Mar’s failure to respond to multiple communications from this site was noted in this site’s report in October, 2021, a report this site delayed until after Sea Mar finally issued notification of the incident to regulators and patients. Sea Mar’s notification to HHS indicated that 688,000 patients were impacted by the breach. DataBreaches.net has not seen any disclosure as to how many employees who were not patients were impacted.
Of note, Sea Mar’s October 2021 press release on the incident reported that on June 24, Sea Mar was informed of unauthorized access — which is exactly when DataBreaches.net first contacted them to alert them to the data leak and to ask them about it.
Data Now Leaked on the Internet with More to Follow?
Months after Sea Mar notified people of the breach and offered them some mitigation services with Kroll, data from Sea Mar that was never leaked by Marketo appears to first be leaking on the internet on both the clearnet and dark web sites for threat actors known as “Snatch Team.”
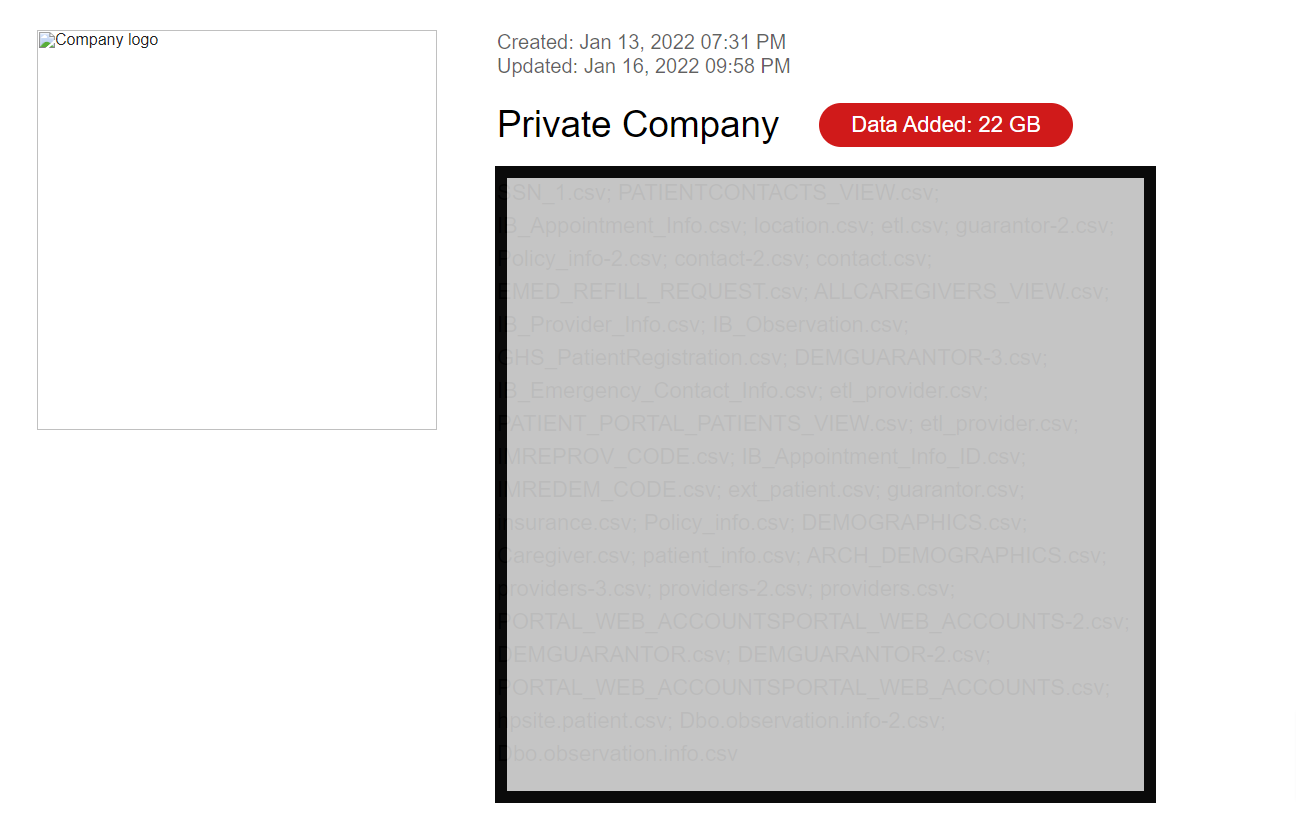
After investigating the files, DataBreaches.net sent an urgent contact form — followed by emails to Sea Mar’s CISO and Executive Director — that what appears to be data from their breach is now being leaked on both clear net and the dark web by threat actors.
Sea Mar has not responded to the alert/notification or to subsequent emails about the apparent leak.
The last time Sea Mar ignored this site’s alert and inquiries, DataBreaches.net waited months to report on their data leak and breach. This time, we are reporting more promptly to ensure that current and former patients and current and former employees find out so that if they haven’t already taken steps to protect themselves, they will learn about their heightened risk as victims and take steps immediately.
As noted above in the figure caption, the threat actors did not name Sea Mar as the entity/source of the data in the 2 GB they have already leaked (they claim to have 22 GB total to leak). DataBreaches.net validated the data using various means. First, an inspection of the files revealed that most of the individuals named in the data leak appeared to be Washington State residents. The names of many of them could be found in Google searches as Washington residents. Second: an attempt to validate that these were real data revealed that the social security numbers and date of birth for the named individuals in one csv file corresponded to the year and state of issuance of the SSN. And third: additional research by Chum1ng0 found that the executive director’s information and the CISO’s information are also in the leaked files. Other names he found in the same file matched the names of employees listed in Sea Mar’s annual report where some employees were named.
On Monday, Databreaches.net also sent an email/alert to the Washington State Attorney General’s Office, because although the individuals may have already been notified last year by Sea Mar, they are now at significantly greater risk. One file alone contained more than 160,000 individuals’ name, date of birth, and SSN. Other files contained their addresses and telephone numbers.
[It is important to stress that at this time, DataBreaches.net does not have any response or confirmation from Sea Mar that this leak is their data and that these individuals have all been previously notified.]
Other files in the current leak include prescription information and health insurance information. And while none of the files has “Sea Mar” as part of the filename or in any properties/info/metadata, Sea Mar’s name appears throughout the leaked .csv files.
As part of its investigation into this leak, DataBreaches.net also communicated with a security professional for one of the health insurers whose members’ protected health information appeared throughout the files. That professional informed DataBreaches.net that as a result of the information we provided, they called Sea Mar yesterday to inquire whether their members had already been notified by Sea Mar last year or if there were members who now first need to be notified.
Sea Mar promised to call them back. They haven’t gotten any call as yet.
HHS lists the Sea Mar incident report of October 2021 as an “under investigation” incident. DataBreaches.net looks forward to reading any findings — including how the breach occurred and why it took four months from the date they became aware that data had shown up on the internet for Sea Mar to send notifications to patients.
Update 1 Jan. 20: A spokesperson for the state attorney general’s office sent the following response to this site’s notification and queries:
Thank you for reaching out to our office. The harm from data breaches can be unpredictable and often delayed. The data dump you share demonstrates this. That’s why our office is so invested in accountability when corporations or agencies handling private data do not have reasonable security measures in place. You can learn more about our work here: https://www.atg.wa.gov/data-breach-notifications The type of enforcement you describe sounds more like something that would be undertaken by the FBI or other law enforcement agency, rather than something that is within our agency’s scope.
Research by Dissent and Chum1ng0; reporting by Dissent