Although one of this year’s trends in cybercrime seems to be a return to the theft/extort model, some groups continue to encrypt victims’ files.
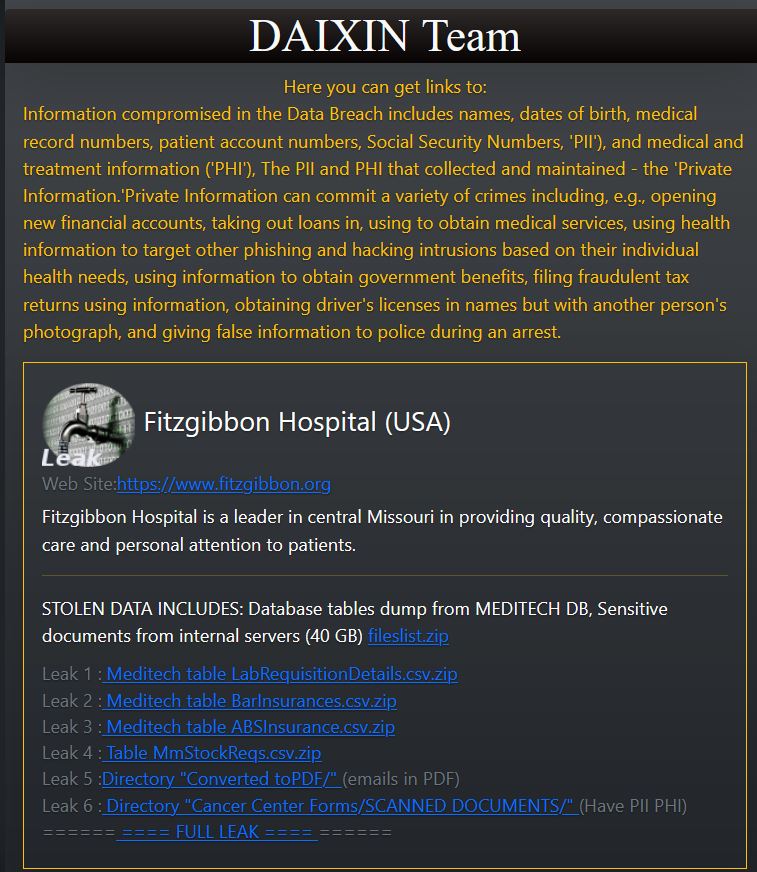
On Saturday, DataBreaches received information pointing to an attack on Fitzgibbon Hospital in Missouri.

The group claiming responsibility call themselves “Daixin Team.” It is not a name known to DataBreaches previously. Their onion site contained files allegedly from Fitzgibbon that they uploaded for the public to grab.

The Data Leak
All told, and with a filelist provided, Daixin claims to have exfiltrated 40 GB of data.
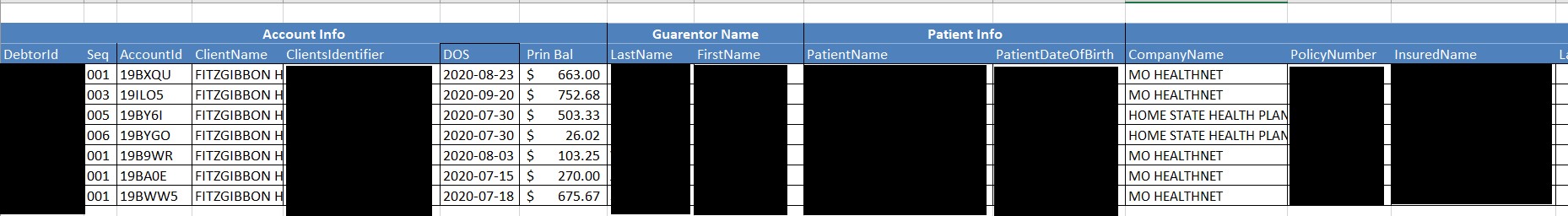
Having skimmed the full leak, DataBreaches found numerous files with protected health information of patients — in various files and with varying fields, there were patient names, diagnostic or treatment information, date of service, demographic information, health insurance information, and billing data. Some files contained records on named patients whose delinquent accounts were being considered for legal action, while another folder contained records on patients where Fitzgibbon decided not to pursue legal action against the patients. Elsewhere in the leak, DataBreaches found a folder with thousands of scanned pdf files on cancer patients with detailed medical reports on them. Those files were from 2020- current.

Among the insurance-related files, DataBreaches noted two .csv files in particular with personal information and health insurance policy information on patients. One of such file contained more than 1 million rows and the other contained more than 750,000 rows.
In addition to information on patients, there were also files relating to named employees. One folder contained salary increase records for named employees. Those files appeared to be password protected.
Routine hospital files involving budgeting, banking and other matters were also noted. But of particular concern, there were a number of files relating to the hospital’s cybersecurity, including the results of assessments the hospital had had conducted so that they could identify vulnerabilities that needed to be addressed. Cybersecurity details and reports that should have been secured from prying eyes are now freely available, in part because a password for one of the files was stored in the same folder with the to-be-protected report.
Other details about pentesting results, vulnerability scans, and self-reports on security measures were contained in other assessments, application for cyberinsurance, and a request for DHS assessment. The hospital appears to have been diligent in getting assessments and attempting to comply with privacy and security regulations, but appears to have failed to adequately secure all documents pertaining to cybersecurity.
Fitzgibbon Negotiates Ransom, Then ….. Crickets
DataBreaches sent email inquiries to the hospital on both Saturday and Sunday, using more than one addressee, but no reply was received. There is no notice on their website to alert patients of any breach or data leak of their personal or protected health information. Nor is there anything that indicates any disruption in care or services.
In the absence of a response from the hospital, DataBreaches asked Daixin Team’s spokesperson for more details. As part of the attack, Daixin allegedly encrypted the servers and backups, but not the workstations. They noted that although they had encrypted backups, the hospital allegedly had old offline backups (“maybe 10-20% of all data”).
According to the spokesperson, on June 9, a hospital representative entered the chat. The attack had been 5 or 7 days earlier (the spokesperson was not precise about the date). After Fitzgibbon entered the chat, they were allegedly given a test decryption and shown proof of data exfiltration.
Daixin’s spokesperson did not tell DataBreaches exactly how much ransom had initially been demanded or what amount was eventually agreed upon, but DataBreaches was given what was represented to be a chat log from June 21:
Fitzgibbon Hospital 2022-06-21 20:47:59:
It looks like we have no choice but to agree to this amount. As long as there are no fees for payment in bitcoins then we can submit this for approval. It is not easy for us as there are multiple organizations we have to get approval from including our board of directors. If we have an agreement we can send payment by Friday. Agreed? If so please add three days to the timer and we will let you know when the approvals are completed.
Admin 2022-06-21 20:54:10
It looks like you’re just stalling.
Fitzgibbon Hospital 2022-06-21 20:56:44
We are not. We promise. We were hoping you would take a lower amount because it would have been easier. But because of this larger sum we have to get different people to agree. We have limitations that we have to work through and get approved. It’s more of a formality process now. It’s possible Thursday we can send but want to be sure we have enough time without asking you again so we are asking until Friday.
Admin 2022-06-21 21:04:03
ok. If we have come to an agreement, then, as we promised, we give additional time for payment. Let it be on Friday. If there is no payment on Friday, the agreement is terminated with all the ensuing consequences.
According to Daixin, Fitzgibbon didn’t pay and never contacted them again.
On Saturday, Daixin informed DataBreaches of the incident and leak.
Was “Admin” right and the hospital was just stalling? If they were unable to pay on time, wouldn’t they have come back to the chat to seek more time or explain any delay? DataBreaches recently noted another incident in which the law enforcement reportedly advised a victim to make the bad actors an offer — not to pay it, but just to make it — to buy more time. Did that happen in this case too? Without a statement from Fitzgibbon Hospital, we do not know. But luckily for the hospital, Daixin did not hit any critical services.
Who is Daixin Team?
Daixin’s spokesperson was reluctant to provide this site with any information on the team, saying that they prefer to remain in the dark, but they did eventually answer some questions put to them.
In response to a question about whether they attack Russian or CIS targets, the spokesperson replied hat they have successfully attacked several Russian/CIS targets, but “as we understud, they doesn’t care about personal data leak and didn’t want pay. The data was sold.” The spokesperson was unable to say what was even in the stolen data, explaining that they did not translate, read or analyze it.
“Russian/CIS targets have not protection and in most of cases very easy, but not interesting,” the spokesperson added.
Their claim about having hit Russian/CIS targets is consistent with a previous communication in which the spokesperson had told DataBreaches that Daixin was not a Conti cell nor linked to any other ransom group. And although the group claims to have hit Russian and CIS targets, they claim they are not politically motivated and have no political preferences. Their motivation is solely financial, the spokesperson stated.
The spokesperson declined to answer a question about how long they have been operating as Daixin Team, but did claim that 90-99% of the targets pay them a ransom. The spokesperson also offered their opinion that constant attacks on USA could very quickly raise the level of cybersecurity in the country.
Because Daixin attacked a hospital, DataBreaches asked if there are any sectors or victims they definitely will not hit. “We discuss each target. If an attack can potentially lead to human casualties, we refuse,” the spokesperson answered, again mentioning that they had not attacked any of Fitzgibbon’s critical medical services.
As to what Daixin would like the public to know about them, the spokesperson answered, We keep our promises (both good and bad).”
This post will be updated if more information becomes available.