 Ever since threat actor groups started naming and leaking victims who do not pay their demands, groups have occasionally misidentified their victims. Today’s example is courtesy of Avos Locker, who added the Canadian Mental Health Association to their leak site in April.
Ever since threat actor groups started naming and leaking victims who do not pay their demands, groups have occasionally misidentified their victims. Today’s example is courtesy of Avos Locker, who added the Canadian Mental Health Association to their leak site in April.
Inspection of the data in the leak, however, quickly raised questions as to its source. Files with “Columbus Metro Housing Authority” were our first clue that the data were from cmhanet.com and not cmha.ca.

April Disclosure
The Columbus (Ohio) Metro Housing Authority breach was disclosed in April. The housing authority’s breach notice offered mitigation services but made no mention of any actual data leak. Perhaps they did not know at the time of the notice (or perhaps they did but decided it did not need to be mentioned?).
DataBreaches saw a lot of personal information in the leak from people who sought rental assistance and low-cost housing arrangements. Applications for tenant housing assistance contained all their personal details and financial condition as well as their Social Security numbers.
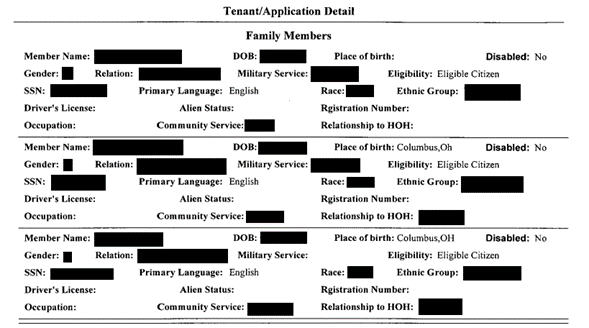
The housing authority’s disclosure did alert people that their personal and financial information had been involved. But it did not tell them about any leak.
DataBreaches contacted the housing authority to alert them to the data leak and to ask them if they had been aware of it and had subsequently notified anyone that their personal information had been leaked.
Several days later, we received a response that the support ticket opened in response to our email had been “resolved.” DataBreaches replied, noting that they had done absolutely nothing in response to our inquiry and had not given us answers to any of our questions, so the matter was not resolved, and to please re-open the ticket. We have heard nothing since then.
Getting no real response from CMHA, DataBreaches also contacted the mayor of Ohio to make the mayor’s office aware of the leak.
No response was received from the mayor’s office, either.
So has anyone notified the residents of Columbus, Ohio who applied for help through the CMHA that all their personal information was made freely available on the dark web? We are guessing that they have not been notified.
Perhaps local media in Columbus, Ohio can get a response or dig into this more.
Note that this was the second Ohio city to have a ransomware incident involving its city metropolitan housing authority. The Cuyahoga Metropolitan Housing Authority reported a ransomware attack attributed to the DoppelPaymer ransomware group in February 2021. DataBreaches does not know whether the two Ohio cities share any network or vendors for their metropolitan housing authorities or whether there was any connection between the Cuyahoga attack and the Columbus attack a year later.
If you were affected by this breach and were notified that your data was on the dark web, please contact DataBreaches.net with a copy of the notification you received. Contact chum1ngo[@]protonmail.com.
Dissent contributed to this story and provided editing help.