On June 28, DataBreaches received a message from an unrecognized sender. The subject was: “Breach of Marriott hotels! Very Important!”
DataBreaches’ first thought was, “Seriously? Is this yet another breach involving Marriott or are some kids just trying to leak old data?”
As it turned out, this was, in fact, a new breach.
But how was Marriott breached this time? What data was involved? And what individual or group breached Marriott?
Let’s address the last question first. DataBreaches would tell you their name, but they insist they have no name. DataBreaches will refer to this group with no name as “GNN” for now (for Group with No Name). Do not assume that this group with no name is a group of newbies or inexperienced, however. DataBreaches is beginning to wonder if they might be the most successful group we have never heard about.
The Breach
 According to GNN, they breached Marriott about a month ago and were able to exfiltrate 20 GB of data including some credit card info and confidential information.
According to GNN, they breached Marriott about a month ago and were able to exfiltrate 20 GB of data including some credit card info and confidential information.
Inspection of a few files provided to this site suggested that the files came from BWI Airport Marriott in Maryland (BWIA). When asked, GNN confirmed that it was BWIA Marriott’s server that they had accessed.
According to statements made to DataBreaches, GNN emailed numerous employees at Marriot about the breach. Marriott initially responded to them, but then stopped communicating:
“We are the ones who organized this leak and they were communicating with us,” GNN’s spokesperson informed DataBreaches, adding, “We were acting like a RedHat organization and they just stopped communicating with us.”
On June 29, DataBreaches contacted Marriott’s CISO, Arno Van Der Walt, who responded promptly and asked if DataBreaches would be willing to talk to Marriott’s external counsel at BakerHostetler. DataBreaches agreed, and spoke with their counsel that afternoon.
Based on what GNN had already shared with this site, DataBreaches was not surprised that Marriott immediately confirmed that there had been an incident and that some data had been exfiltrated. Also unsurprisingly, they described the incident as being less significant than GNN had described it.
But while GNN had declined to answer any of my questions as to how they had gained access, Marriott informed DataBreaches that the breach occurred because social engineering successfully tricked one associate at a single Marriott hotel into giving the threat actor(s) access to that associate’s computer.
Marriott added:
We have no evidence that the threat actor had access beyond the files that were accessible to this one associate.
Given an opportunity to comment, GNN did not really dispute many of Marriott’s statements, saying that for the aspects they knew about, Marriott’s version was pretty close to what had happened.
DataBreaches does not know when GNN first contacted Marriott with any monetary demands, but Marriott claimed they had identified and were investigating the incident before they were ever contacted by GNN. Marriott also claims that the incident was contained in six hours. GNN could neither confirm nor dispute either claim.
Both Marriott and GNN agree that Marriott did not pay any monetary demand. Marriott’s statement was silent on the issue of whether they had negotiated at all, but GNN’s statements to DataBreaches indicated that there had been some kind of communications:
They were communicating with us and went silent for no reason, it might be because of the high pricing, but we are always willing to find a deal with our clients and told Marriott that we can provide all the discounts in the world.
Stolen Data
Marriott acknowledged that while most of the data acquired by GNN was what Marriott described as non-sensitive internal business files, they will be notifying approximately 300-400 individuals and any regulators, as required. They did not provide a full description as to what kinds of personal information were involved for the individuals being notified.
Law enforcement has reportedly been notified, and Marriott states that they are supporting that investigation.
GNN commented on Marriott’s security:
Their security is very poor, there were no problems taking their data. At least we didn’t get access to the whole database, but even the part that we took was full of the critical data.
GNN considers some of the proprietary information and the personal information of guests and employees as “critical data.” They provided DataBreaches with samples from the 20 GB of files that they had exfiltrated.
A number of the files in the sample were, indeed, internal business documents with confidential and proprietary information such as how to access a labor management and scheduling platform. From the dates on the files, some of these manuals and audits might no longer be currently applicable. DataBreaches is not including them in this report but notes that a relatively recent file concerning average wages by department might be of interest to employees or competitors.
Apart from internal business documents, other documents contained information on hotel guests and personnel. DataBreaches reviewed a number of documents where airlines made reservations for their flight crews to stay at BWIA. The forms included the crew members’ names (first initial and last name), what flight number they would be arriving on, what flight number they would be departing on, their position on the crew (pilot or flight attendant), and their assigned room number by BWIA. The arrangements also included what appeared to be corporate credit card numbers for the airline or travel agency making the guests’ arrangements. Screencaps of portions of two such files appear below:
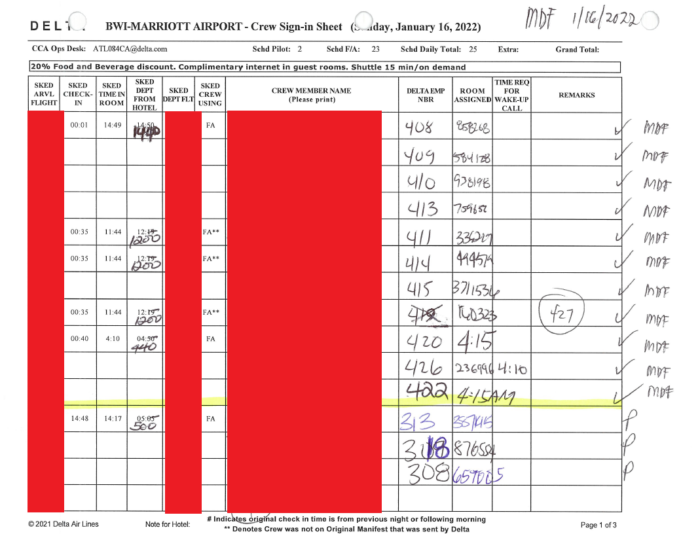
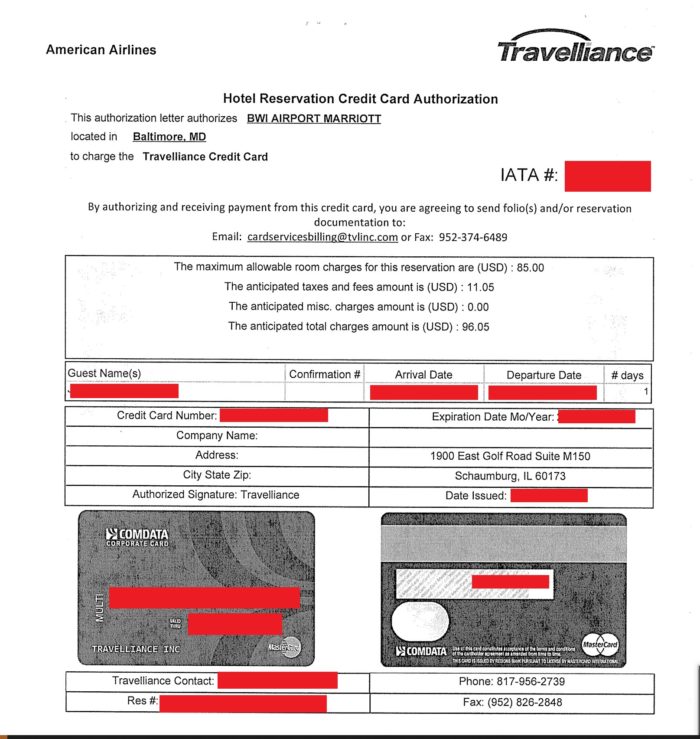
DataBreaches also reviewed what appeared to be a Human Resources-related file: a personnel assessment of a named event supervisor at BWIA Marriott. Although the named employee was rated positively on all measures and the narratives about her performance gave glowing reviews, it is not clear what that file would be doing in the hands of the same associate who had access to guest reservations and credit card information. And it is certainly not the kind of confidential personnel file that an employer would want leaked.
DataBreaches does not know whether the 300-400 people Marriott will be notifying are mostly guests, personnel, or a combination of both.
Marriott’s Response
As noted above, Marriott immediately acknowledged that there had been a breach. Their statement for publication did not reveal how they first discovered the breach nor all the steps that they have likely taken in response including, perhaps, retraining any employees to avoid social engineering. From experience, DataBreaches understands that entities do not want to publicly reveal security measures or changes in measures, but one can only wonder what would have happened if GNN had managed to trick a different associate who had access to a different server.
So Who is GNN?
Is this group with no name a group of newbies who got lucky, or are they so skilled that they have managed to avoid media coverage while attacking major corporations like Marriott? DataBreaches suspects it’s the latter, but keep in mind that at this point, their claims about themselves and their history have not been and cannot be verified by DataBreaches.
In communications with DataBreaches, GNN claims that they are an international group that has been working for about five years. They say they have avoided media coverage by establishing a reputation for keeping communications and relationships confidential.
GNN also tells DataBreaches that they never encrypt anything because they do not want to interfere with business. When asked if they attack Russian and CIS entities, they did not answer with a simple “yes” or “no,” but responded, “We are attacking all the businesses all over the world. They say they do not attack critical government infrastructure and focus only on businesses.
When asked why they reached out to DataBreaches (although they obviously showed good taste in that), their spokesperson indicated that it was because they had decided to change their business structure. If that’s the case, do not be surprised to read more about this group’s activities on DataBreaches. The Marriott breach may not be huge as far as other breaches go, but this group successfully attacked Marriott and exfiltrated data. That alone is impressive.
Previous Breaches Involving Marriott
In the time since this blog first opened, DataBreaches has reported on a number of data security incidents involving Marriott:
- In September 2010, HEI Hotels & Resorts disclosed that a “vulnerability in an information system at certain of its hotel properties may have been exploited.” Those properties included a number of Marriott-branded hotels.
- In November 2010, a Hungarian who had decided that infecting Marriott and then trying to extort them for a job was a great employment strategy learned that oh boy, maybe it wasn’t such a winning strategy.
- In April 2011, Marriott Rewards program customers were notified about a breach involving Marriott vendor Epsilon.
- A 2014 breach at Starwood that neither Starwood nor Marriott knew about when Marriott acquired Starwood in 2016 was first reported In November 2018. Marriott disclosed that the breach impacted almost 500 million guests, a number that they eventually re-estimated at 383 million or less. That incident resulted in a $100 million class action lawsuit in Canada and an £18.4 million fine by the U.K.’s Information Commissioner’s Office. Other cases in the U.S. and elsewhere have yet to be resolved (read, for example, about how claims in one case were recently upgraded by a judge in May of this year.
- While litigation from the 2018 breach was still percolating, in October 2019, Marriott announced that a breach at an unnamed vendor had impacted some of its associates.
- Months later, in March 2020, Marriott had to notify 5.2 million guests whose personal information was accessed between mid-January and February 2020 after two employees’ login credentials were compromised.
- And now in 2022, a group with no name breached BWIA Marriott.