Is “Bl00dy Ransomware Gang” a new ransomware group on the scene, a rebrand, or neither?
In July, a new channel appeared on Telegram called the “Bl00dy Ransomware Gang.” In August, information about alleged victims started to appear. So far, the gang has leaked some data allegedly from three victims in two incidents. In each case, there is some confirmation that the victims may have been attacked, but there is no confirmation from the named victims that this group attacked them. Here’s what we know so far:
One of the claimed victims is a medical practice in New York called Primary Care of Long Island (PCOLI). PCOLI was added to the Telegram channel on August 7. A second website, oncallpractice.com, was also listed as part of the same incident. Both businesses are listed at 820 Suffolk Avenue, Brentwood, in a building that houses several medical and dental practices.
While the oncallpractice.com website is currently “down for maintenance,” the firm appears to be a business associate or vendor offering billing, appointment booking, and technology services. Their Facebook page has not been updated since July 17.
PCOLI’s homepage has a prominently displayed breach notification. According to an undated notification letter, PCOLI believes the breach occurred on or about May 23, 2022. They also state:
On June 8th we were informed that the intruder may have transferred files from our systems which may include your name, phone number, address, social security number, and date of birth.
Their notification does not mention any encryption of files, disruption to services, or ransom demand.
From the small amount of proof offered by the threat actors, the types of information acquired included more than what the notification letter describes, but it is not clear whose system the files may have been exfiltrated from. DataBreaches saw images of a health insurance card for an individual patient with images of their driver’s license, documentation concerning their eligibility for health insurance coverage, and a Visit Note describing a dental appointment. But all of those appear to relate to a third entity, Brighter Dental Center.
Brighter Dental Center is also located at the same address in Brentwood, New York, but Brighter Dental Center was not listed as a victim or target of the ransomware gang. If the dental service uses OnCallPractice (and DataBreaches does not know if it does), it is unclear whether the records were exfiltrated from the dental practice or possibly from OnCallPractice.
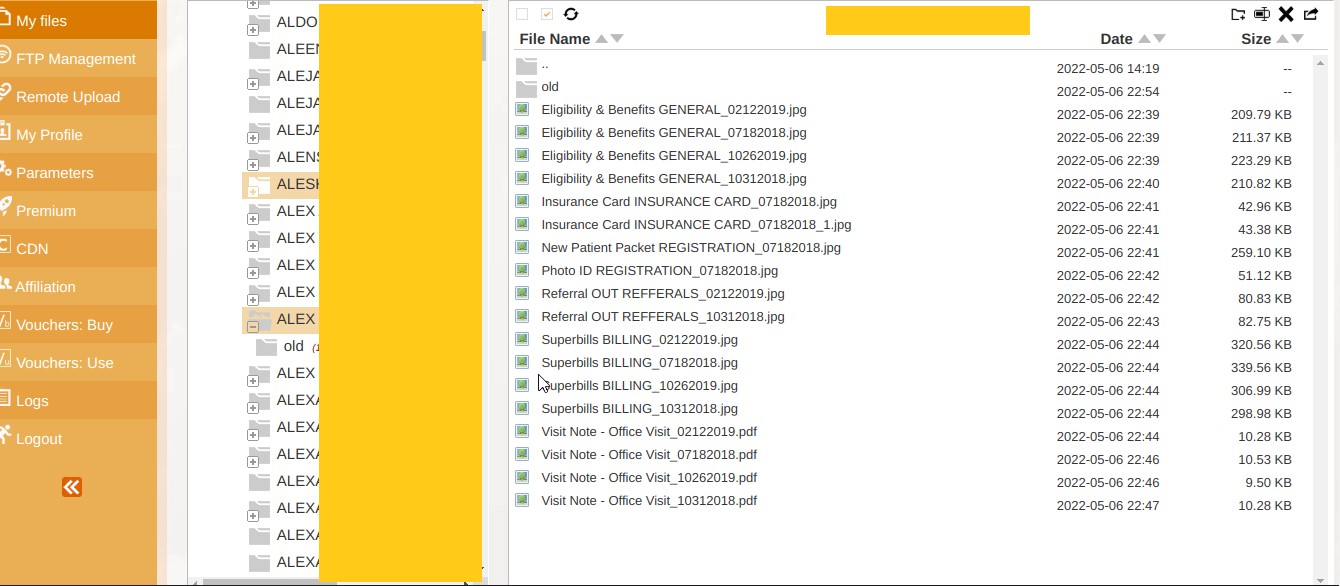
One of the screenshots provided by “Bl00dy Ransomware Gang” reveals what appear to be patient names and other information, but it is not clear what the source of the data is. Redacted by DataBreaches.net. The redaction at the top of the image covers the patient’s name and date of birth.
DataBreaches reached out to PCOLI and OnCallPractice with inquiries. It is unknown to DataBreaches whether there is any business associate agreement or relationship between the two entities. Nor does DataBreaches know if there is any association between either or both of these entities and Brighter Dental Center, who DataBreaches also contacted.
None of the three entities replied to inquiries. Nor did an unrelated business firm the group claimed as a victim in another attack reply.
Who Are the “Bl00dy Ransomware Gang?”
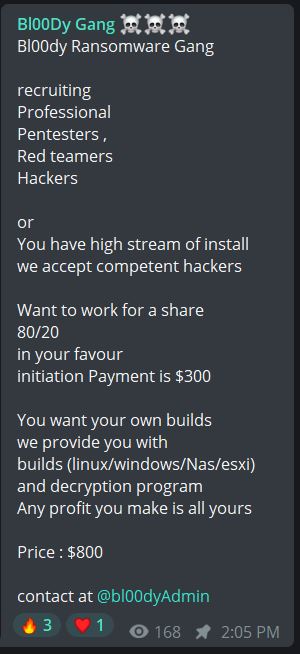
DataBreaches had never heard of this group before and, so far, has been unable to find any reports on them or analyses. The only reference found to ransomware by that name so far was an MD5 hash. So how does the group describe themselves?
In a post in their channel, they claimed they encrypted all of a victim’s files with a *.bl00dy extension and then took the servers offline. More than three weeks later, one of the four subdomains was 404, but the other three appear to have been restored.
In a post on their channel, the group seeks to recruit pentesters and others, offering an 80/20 split. They also offer custom builds for Linux, Windows, NAS, or ESXI for $800, with the purchaser keeping all profits for themselves.
But who are they, and if they are legitimately a ransomware group and not some scam, what family of ransomware is this — or is it something unique that they have coded themselves? DataBreaches does not know, so in addition to reaching out to their alleged victims, DataBreaches also reached out to the Bl00dy Ransomware Gang’s contact person to ask them questions; No reply has been received as yet, but the contact’s Telegram account has not been accessed since August 26.
This post will be updated if replies are received or if more information becomes available. DataBreaches considers the group’s claims unconfirmed at this point because none of the victims have confirmed any ransomware attack or attack by a group with that name.
Update: It appears that Dr. Priti Patel notified HHS of a breach as “Priti Patel Physician PC” on August 14. Dr. Patel is associated with PCOLI. The report to HHS indicated that 6,877 patients were affected by a hacking/IT incident. It does not indicate that any business associate was involved.
Update2, August 29: A spokesperson for Bl00dy Ransomware Gang confirmed that they got all of the entities mentioned above, claiming that they have a lot of evidence to back their claims. They added that “Dr. Prashant manage it.” Dr. Prashant Patel is the owner of Brighter Dental Center. None of the entities have replied as yet.
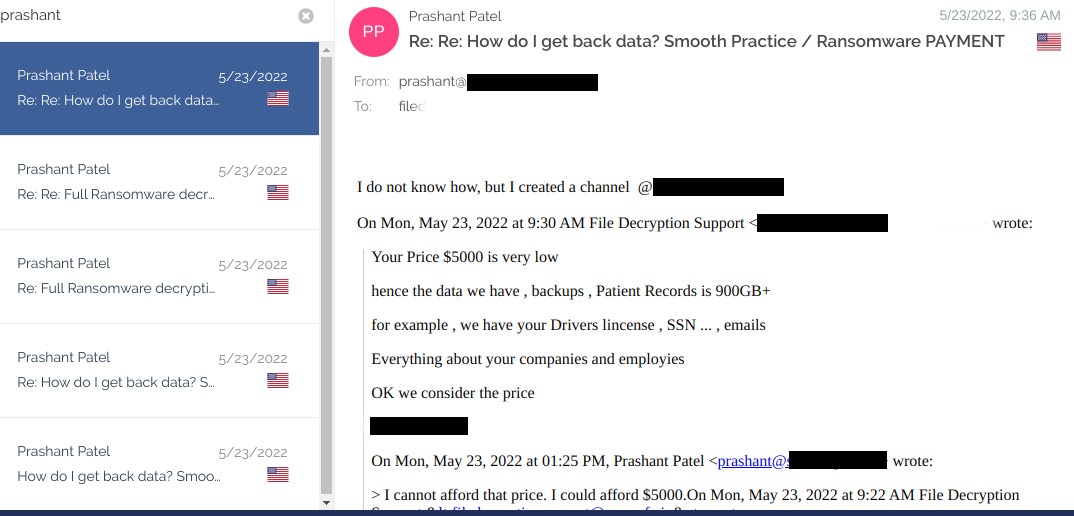
Update3, September 11: Dr. Prashant Patel/Brighter Dental continues to ignore email inquiries and OnCallPractice’s site is still “under maintenance.” A spokesperson for the ransomware gang tells me they are considering selling the data. They have previously claimed to have 900 GB of files from the three practices.
The spokesperson has also provided additional information and claims, including snippets from a chat between them and Dr. Patel on May 23, 2022. That date is significant because Dr. Priti Patel’s notification letter states, “On May 23, 2022 the intruder obtained access to our network. On June 8th we were informed that the intruder may have transferred files from our systems which may include your name, phone number, address, social security number, and date of birth.”
If Dr. Prashant Patel knew on May 23, his notification clock for Brighter Dental patients began ticking then. Yet more than 60 days later (the outer limit under HIPAA), Brighter Dental still has not issued any notification or disclosure that DataBreaches can find. Nor has OnCallPractice.