On January 9, DataBreaches noticed that Aviacode had been added to the leak site for 0mega. Aviacode, which is part of GeBBS Healthcare Solutions, offers medical coding services, medical coding audits, coding denial management, clinical documentation improvement, and revenue cycle management for billings and claims. As such, it is often a business associate for HIPAA-covered entities.
Seeing 0mega’s claims, DataBreaches sent an inquiry to Aviacode. They did not reply. As 0mega later told DataBreaches, Aviacode did not respond to them, either.
On February 11, 0mega dumped more than 200 GB of Aviacode files.
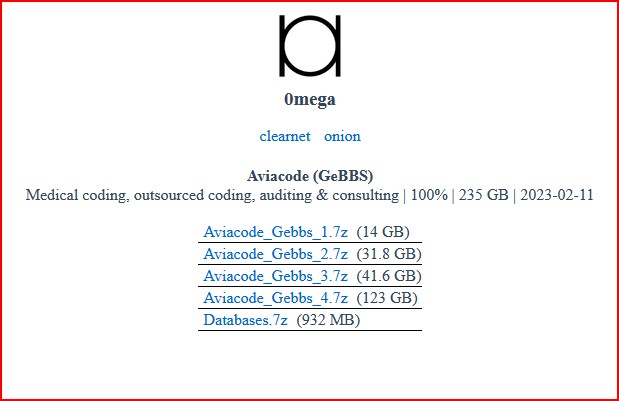
By now, neither Aviacode nor GeBBS has responded to inquiries by DataBreaches. Well, let’s correct that to say that in response to inquiries about the claimed data breach, their marketing department started sending this site unwanted press releases that are nonresponsive to inquiries.
Aviacode is headquartered in Utah; GeBBS is headquartered in Los Angeles. State laws about breach notifications will apply. DataBreaches has not found any press releases or notifications to state regulators or HHS at this point.
DataBreaches was unable to download many of the 200 GB of files and did not spot any patient databases in the data this site did inspect, but we did discover concerning employee and contractor data. As examples:
One screenshot showed folders with data on employees, payroll, tax information, and users.
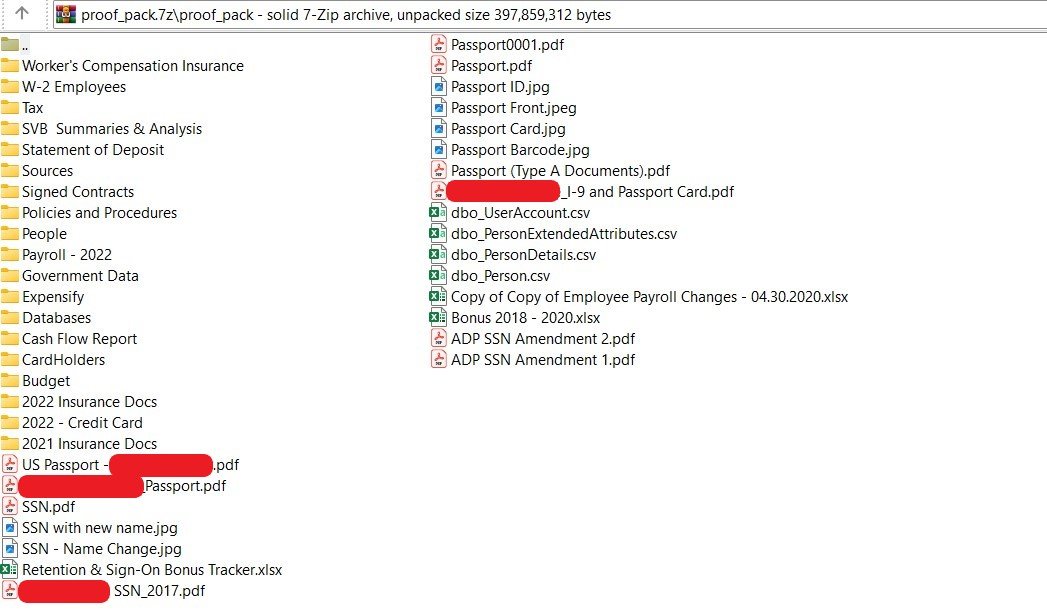
A second directory contained vendor and employee wage information (1099s, W-2s) from 2015-2017. Yet other files contained data for subsequent years. The following image shows the types of contractor/vendor information that has been leaked.
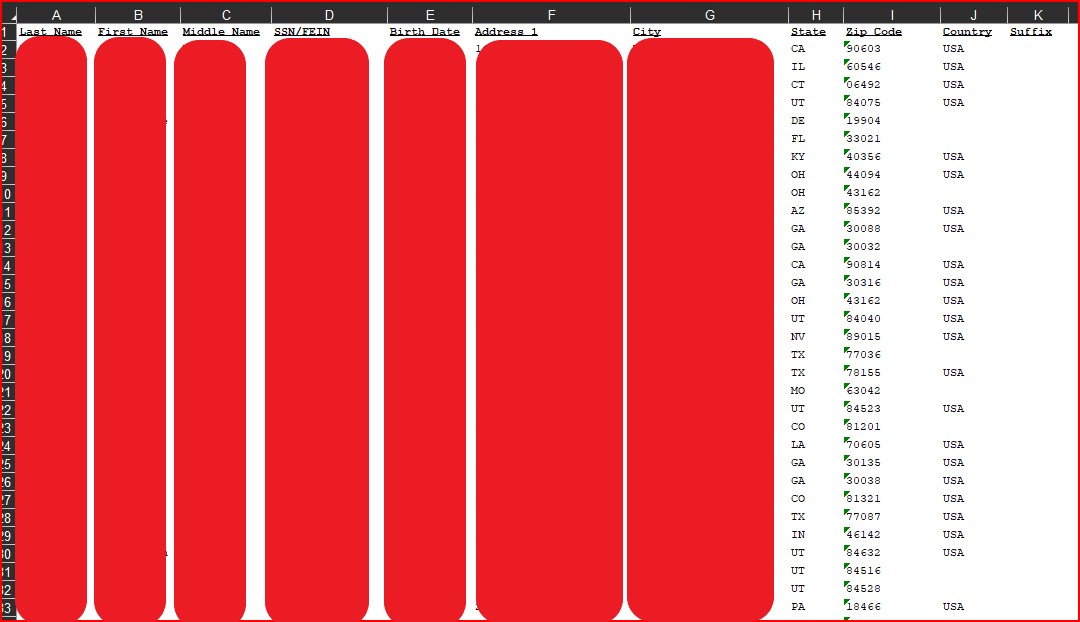
Other employee-related files included employees’ salary information, position, credentials, date of hire, and in a few cases, passwords. There were also files on terminated employees that contained all of their information including their background checks.
DataBreaches has yet to spot any extensive admin or password data, but the password data that DataBreaches did see was concerning because every user had the same password of “Simple2871!” DataBreaches did not attempt to gain access to Aviacode, so does not know if that password was working at the time of the attack. Hopefully, if it ever was working, it has been changed.
According to 0mega’s spokesperson, as early as January 1, 2023, 0mega locked Aviacode, but Aviacode never responded to any of their communications. When asked whether 0mega was sure that Aviacode had even read their communications, their spokesperson replied:
Indeed, these guys do not behave like gentlemen also. We have attacked their mail server and created a mailing list including all their top management. After that they had held a meeting with all company tops, they all had received our message and got together to discuss the situation. We watched this meeting online. That channel had some difficulties, it prevented us from catching every word, but the main idea was clear – they all do not know what to do. They can not cure their net but still never come up to negotiations with us. They could have come to a solution in several hours of negotiations and cured their net in a day but they never did.
0mega also informed DataBreaches:
We have been observing the command line of their admins. The reactions were far from competent and adequately qualified. They simply do not know their work. Everything they care about is their salary bonuses and the fact that their fails will not be revealed. And that is the element that prevent Tops from making correct decisions. They have lost access to mail servers, backups, network management servers – to everything. And, being horror-struck, lie to everyone that they have control over everything. No, they don’t.
It is now more than 1.5 months since Aviacode’s files were allegedly locked. Have they recovered from the attack? They haven’t said because they haven’t even confirmed or publicly acknowledged any attack.
Has Aviacode notified its current and former employees and contractors that their SSN, date of birth, addresses, and other information has been publicly leaked, or are employees and contractors/vendors unaware?
Eventually, DataBreaches may be able to review more of the data leak to see if there is any protected health information in there that would trigger notification obligations under HIPAA and HITECH, but it’s clear from what DataBreaches has already seen that Aviacode is likely required to notify a number of state attorneys general about the employee and contractor data.
As to 0mega ransomware, not much is known about it since it first appeared in mid-2022. The leak site has only listed three victims since it opened.
If any reader has received a notification from Aviacode or GeBBS about this incident, please contact this site via email to reports[at]databreaches[dot]net.