Alexander Martin reports:
Researchers from the Chinese cybersecurity company Qi An Pangu Lab believe they have identified six members of the “Against The West” hacking group, according to a report published Sunday by state-controlled media.
The report implicitly alleges without evidence that the hackers are connected to or sponsored by Western nation-states. The six display “a clear pro-US and pro-West slant,” the Global Times tabloid newspaper wrote. Members of Against The West (ATW) indeed have described themselves as pro-Western and claim to have targeted organizations that are “against the West.”
Read more at The Record.
There’s little doubt that the individuals involved in ATW are pro-West. And some of what is reported about them is consistent with what a spokesperson had told DataBreaches in an April 2022 interview.
AgainstTheWest (“ATW”) had a history on Twitter and Telegram that was replete with drama as members left or split or fought, and as accounts were canceled by platforms.
When the Breached forum opened in early 2022, ATW, who had been on Raid Forums prior to its seizure, joined.

ATW was permanently banned in September, however, by the forum’s owner, Pompompurin.
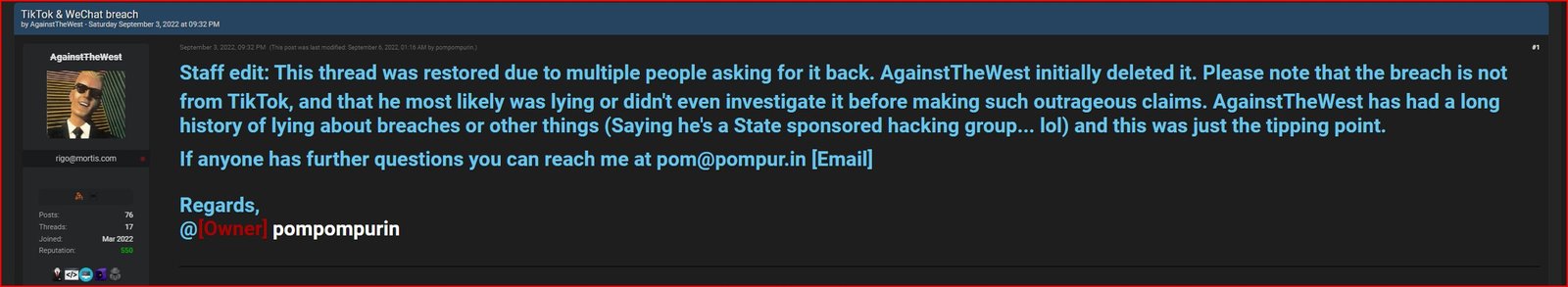
The Staff Edit note on ATW’s TikTok & WeChat listing explains:
This thread was restored due to multiple people asking for it back. AgainstTheWest initially deleted it. Please note that the breach is not from TikTok, and that he most likely was lying or didn’t even investigate it before making such outrageous claims. AgainstTheWest has had a long history of lying about breaches or other things (Saying he’s a State sponsored hacking group… lol) and this was just the tipping point.
The concerns about false or exaggerated claims were echoed by the Chinese researchers. The Global Times reports the researchers’ findings about some of ATW’s claims:
For example, on January 7, 2022, ATW claimed to sell “a large amount of government, NGO, institutional and corporate data in China, involving 102 Chinese entities.”
However, experts from the lab found that the so-called source code is the test data or project code files developed by small and medium-sized software development enterprises. Experts also found that, in order to gain attention, ATW tends to distort and exaggerate its attacks.
ATW does not have a sterling reputation at this point, then, but is still of concern to China because it targets them. How much specific information do the researchers have on their names or locations has not been revealed — at least, not yet.