On March 12, DataBreaches reported on the Health Benefit Exchange Authority data that was first leaked by a forum user known as “IntelBroker” and then by “Denfur.”
The DC Health Link incident attracted a lot of media attention because it involved members of Congress, their staff, and their families. As StateScoop reported today, DC Health Benefit Exchange said on Friday that 56,415 customers had their data swept up in the breach. But it wasn’t just members of Congress and those associated with them whose information was compromised. StateScoop reports that the data set posted Sunday by Denfur also included hundreds of names spread across at least 20 foreign embassies and thousands of other employers. And as CyberScoop previously reported, the data set also included former national security and defense officials and “a wide swath of the capital city from employees of coffee shops, to dentist offices to civil society groups.”
After DataBreaches’ post appeared, Denfur contacted DataBreaches to discuss the leak. By agreement, DataBreaches is not disclosing his actual (main) account on BreachForums but notes that the “Denfur” account is just an “alt” to protect his main account while leaking the DC Health Links data.
Based on what Denfur claimed to DataBreaches, DC Health Link should never claim they were the victim of any sophisticated cyberattack because no authentication was required to access the data at all.
IntelBroker “literally Google dorked to find it,” Denfur told DataBreaches.
DC Health Link’s incident page and updates do not state that the data had been unprotected. If Denfur’s claim is confirmed, news sites reporting that DC Health Link was hacked need to correct or update their reporting.
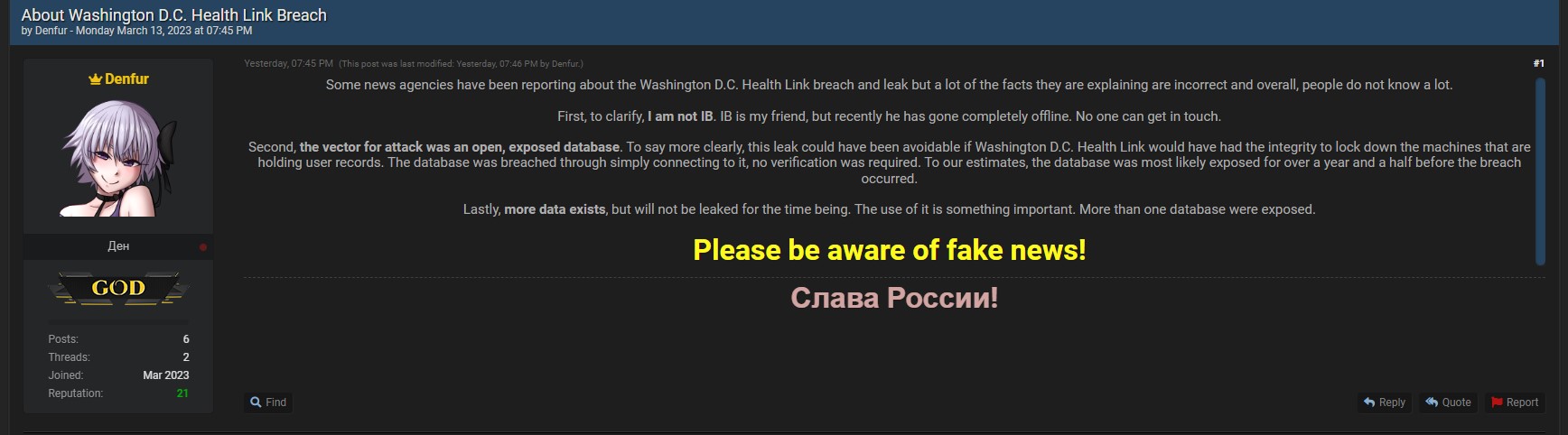
Last night, Denfur posted some additional information about the leak. In that post, he wrote, in part:
Second, the vector for attack was an open, exposed database. To say more clearly, this leak could have been avoidable if Washington D.C. Health Link would have had the integrity to lock down the machines that are holding user records. The database was breached through simply connecting to it, no verification was required. To our estimates, the database was most likely exposed for over a year and a half before the breach occurred.
Denfur’s post also reiterates earlier claims that IntelBroker has more as-yet unreleased data. From statements made to DataBreaches by Denfur, it sounds like IntelBroker may have acquired millions of records from government systems, but Denfur does not have those data and DataBreaches was unable to reach IntelBroker to ask about it.
Other data IntelBroker allegedly has yet to leak includes additional data from DC Health Links. But again, DataBreaches was unable to confirm that claim in the absence of data that only IntelBroker reportedly holds.
So where is IntelBroker? IntelBroker’s listing had been removed from BreachForums, and IntelBroker initiated a self-ban shortly after the listing was removed. DataBreaches asked Denfur, who describes himself as a friend of IntelBroker’s, whether IntelBroker removed the listing and self-banned out of fear of law enforcement. Denfur informed DataBreaches that after IntelBroker’s listing appeared, there were a lot of brute force attacks on IntelBroker’s account and the forum owner wanted the account banned to block the attacks. So IntelBroker deleted the listing and self-banned his account, Denfur claims.
But IntelBroker hasn’t been seen since then, and it is now about 5 days. Denfur tells DataBreaches that he does not know why IntelBroker has been out of touch and is concerned.
Is IntelBroker just laying low? Perhaps. If he is sitting on data from the government and more data from DC Health Link, law enforcement is undoubtedly in high gear pursuing him.
DataBreaches also asked Denfur about his own role in leaking the DC Health Link data. Why did Denfur create an alt and offer the data for only 8 forum tokens instead of trying to sell it? And why did he eventually just give it all away for free?
“It was an experiment to see if I could mess with the news cycles,” Denfur told DataBreaches. “I paid Intel $400 to let me leak it, and I really just wanted to cause a bit of chaos. Money is cool, but I have a lot of money. Sometimes you want to have fun.”
So the “Glory to Russia” [written in Russian under his first listing] was b.s.?” DataBreaches asked him.
“I am Russian,” Denfur replied, “but I knew that having that so public would influence how the news talked about it.”
Denfur declined to answer a question about whether IntelBroker was also Russian.
At the end of the interview, when DataBreaches asked if there was anything he had not been asked that he wanted to say, he replied, “Yes, just one more thing I would like you to include if you do write. Snowden did nothing wrong!!”
And all is for the best in this, the best of all possible worlds, right?
Russia is a failed state. This leak is amateur hour. These guys didn’t even de-dupe initially. DC Health Link is also a joke. Horrible “security”