Unique Imaging, Inc. has three locations in Florida: Aventura, Biscayne, Miami, and Dadeland. If you were to visit their website today, you wouldn’t see any sign of anything amiss, but appearances can be deceiving. A ransomware group claims that they have been living in Unique Imaging’s network for months and helping themselves to patient data at will.
DataBreaches first became aware of the situation when the Trigona ransomware group opened a dark web leak site and listed Unique Imaging on it. At the time, there were 76 days left on a countdown clock for the listing with prices listed for an auction of the data.
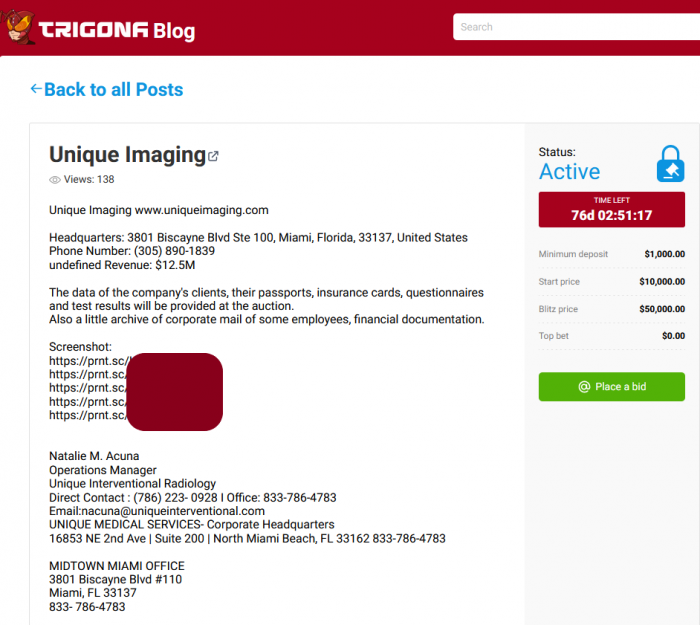
As it turned out, the auction data was a bit deceiving, but more on that later.
On April 18, DataBreaches emailed Unique Imaging to ask them about the claimed breach. No reply was received. While they didn’t reply to this site’s inquiries, Trigona did. They provided additional proof and data relevant to specific claims they had made.
After reviewing the additional data, DataBreaches sent a second email to Unique Imaging on May 1. A contact form message was also sent to them, alerting them to check their email. Unlike the first email of April 18, the second one was also sent to Christopher Woodhouse, M.D., Medical Director for Unique Imaging. The email included a question about Trigona’s claim about still having access with some of the proof Trigona had provided on that point.
Once again, no reply has been received.
Because DataBreaches can find nothing that indicates Unique Imaging has disclosed this breach to patients or regulators, DataBreaches will provide an overview of what Trigona has claimed and what they have provided this site.
Protected Health Information
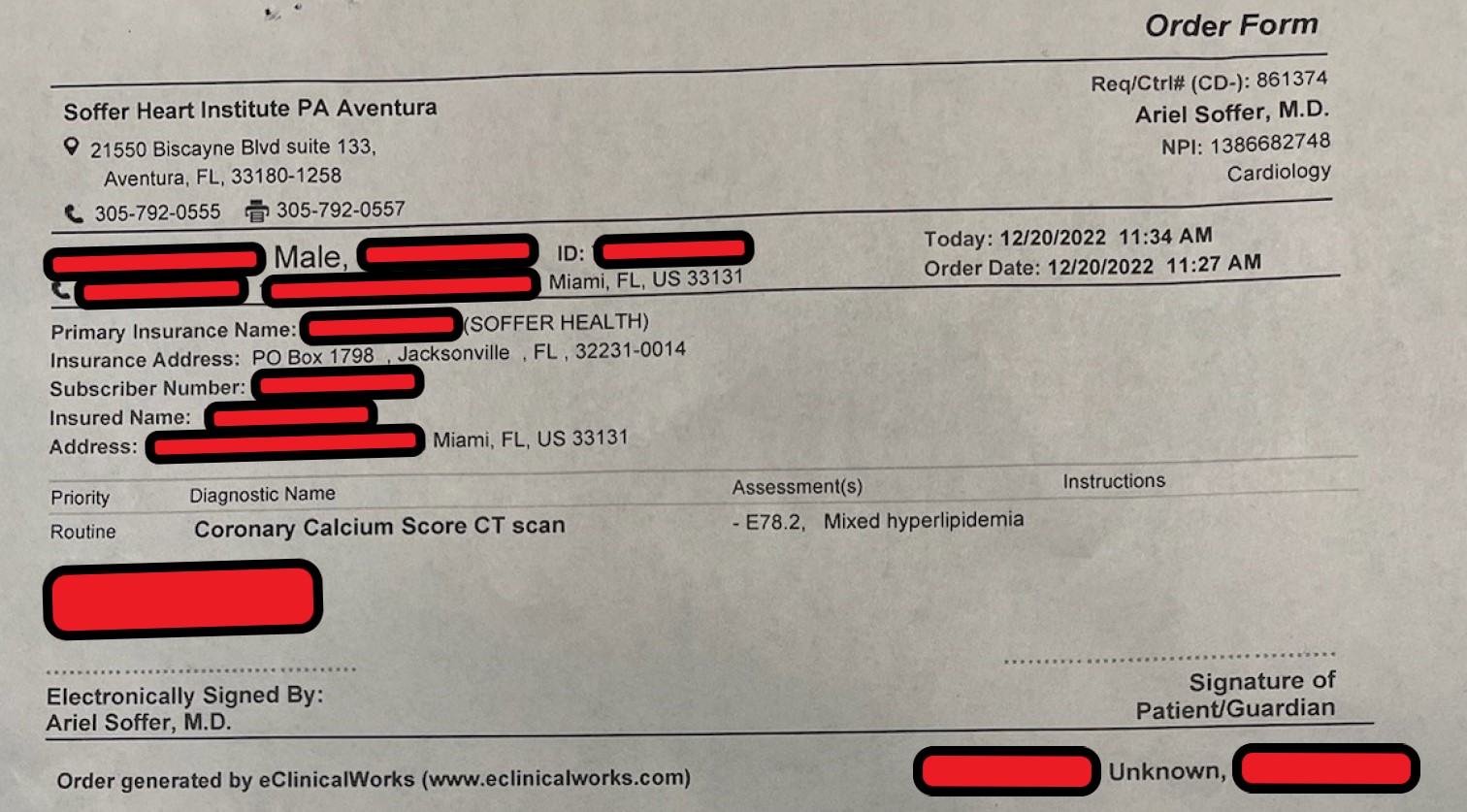
Trigona provided this site with a small sample of data that included hundreds of scanned pdf files with prescriptions, clinical results, and other protected patient health information. There were also health insurance cards, images of driver’s licenses, and purchase orders.
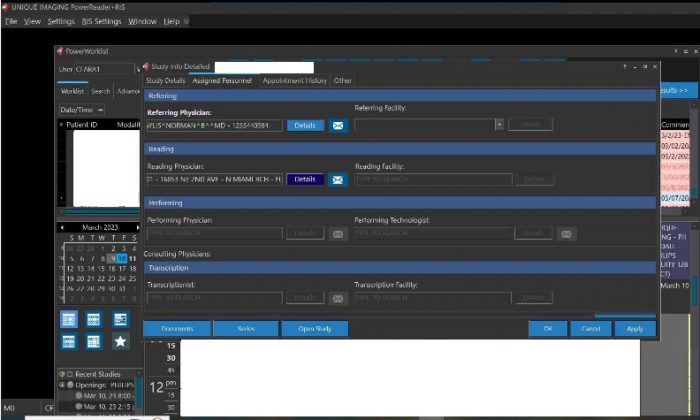
Of significant concern, two screencaps provided on their leak site indicate that Trigona accessed Power Reader RIS. RIS (Radiology Information System) is an electronic health record (EHR) system specific to radiology. The screencaps below were taken from Power Reader RIS. DataBreaches redacted exposed patient information in the screencaps, but the fact that Trigona was able to access this system means that they may have had access to a great deal of protected health information.

Via exchanges on qTox, DataBreaches asked Trigona additional questions about the incident and their group. Although they said they could not recall the exact date when it was first clear that Unique Imaging knew about the breach, Trigona ‘s spokesperson informed DataBreaches that they had also called them on the phone on February 27 and spoke with Unique Imaging’s CEO. She allegedly first told them to call her lawyer, but later allegedly asked them to email her information. Subsequent attempts to talk to them by phone reportedly resulted in hangups.
Trigona claims they have been in Unique Imaging’s network for approximately six months. DataBreaches did not see any timestamped proof to support a claim of six months in the sample provided but did see a timestamp in December. To prove their claim that they still have access, Trigona created an account for DataBreaches on the network, sent us a log of the account creation, and invited us to access the account. We didn’t, of course, but sent that information to Unique Imaging to make sure they were aware of the claim and proof.
“We are still using them for our own purposes and are still downloading the data of interest,” Trigona told DataBreaches. When DataBreaches later asked them what their purposes were, they replied, “We send infected emails on behalf of the company to customers or partners. There are also groups that use the data to take small loans and cash them out. Actually there are a lot of options.”
Trigona did not reveal how much data they had exfiltrated or what their initial ransom demand was with Unique Imaging.
About Trigona
Trigona was first spotted publicly in June 2022, but their spokesperson told DataBreaches that their group had been operating privately since the beginning of last year. They also claim that there have been many more attacks this year than the 190 estimated for 2023 by Bleeping Computer in a recent article. When asked why they only recently opened a leak site, Trigona’s spokesperson responded, “To make the attacked companies understand the seriousness of the situation.”
DataBreaches asked if they were a closed group or had affiliates. “We are a closed group and are not represented in any of the thematic forums,” they responded. They declined to comment on questions raised by others about their possible relationship to AlphV or why some of their earlier listings had appeared on AlphV’s leak site, observations made by others in their reporting on Trigona.
Trigona has recently attracted attention and technical analysis. For technical reports on Trigona, see reports by Zscaler (April 2023), Arete (February 2023), Unit42 (March 2023), and Bleeping Computer (April 2023).
Trigona confirmed to DataBreaches that they use the double-extortion model involving both locking a victim’s files and demanding payment to provide a decryptor and delete files. They currently use chacha20 and ECC for encryption.
When asked if there are any countries or sectors they won’t attack, Trigona answered that they only attack Tier-1 countries. They say they generally do not attack “state-owned enterprises and companies of strategic importance.” On follow-up, they added that they do not ban certain countries or industries “but consider each case based on our interests and security reasons. You were provided with just a few examples that we prefer not to mess with. We only offer a platform for work, and the partners themselves form preferences and exceptions in their work.”
The fact that they have listed Unique Imaging and a second medical facility in Australia indicates that they are not averse to hitting medical entities.
They declined to get specific about any range of ransoms they might demand, noting that the amount set reflects the importance of the victim, the amount of data, the quality of the data they obtain, and (at least in this case), the victim’s refusal to negotiate. They noted that their prices include network analysis and security audit services. They prefer Monero for payment.
Trigona’s ransom notes include victim-specific links to access their chat. Victims can provide three files to test the decryptor.
Trigona’s leak site appears to put victim data up for auction if the countdown clock runs down. There are “minimum deposits,” opening bids,” and a “blitz” price. None of that is real, however. If one reads further down in the Unique Imaging listing (not shown in this article), it says, “For intelligence agencies and smart people trying to hack this auction: This is just an informational blog, not a real auction, we provide our partners with private access to the auction to participate in it. This blog is for informational purposes only for victims, journalists and future partners.”
Although Trigona doesn’t leak the data publicly when a victim refuses to pay, they may do that in the future. “We are in the process of transitioning to the glasnost format. Before that, we preferred to sell data in a closed format,” they told DataBreaches.
DataBreaches also asked Trigona if there was one feature of Trigona ransomware that they are most proud of. Trigona answered: “Our partners are better protected than our competitors. The data is stored and transmitted in encrypted form, and the rest does not carry a payload. The software also has advantages: speed is constantly improving without changing the algorithms and there are ways to reduce the likelihood of data corruption. Our project is developing rapidly and listens to the opinion of partners. In addition, we do not deceive partners and offer transparent conditions – we understand that reputation is extremely important.”
What Next?
DataBreaches will continue monitoring this incident and Unique Imaging’s incident response. An update will be posted if more information becomes available.