It appears that Pain Care Specialists in Oregon became the victim of an attack by AlphV. The threat actors added the medical entity to their leak site earlier today with some files with personal information on employees and patients.
AlphV’s listing noted that the breach occurred on September 13, and, “As a result of our hack attack the network has been encrypted and over 150GB of sensitive data were stolen from there. Those data includes patient’s and employee’s medical records, social security numbers, employees ID’s, contracts, drug screens, payments and another sensitive info. In addition we have gained access to portals of federal medical regulation web-resources that allows managing of prescribed medicine and provides access to medical records of various individuals.”
Consistent with other leak site posts, AlphV demonstrates that they look at claims that sites make and then point out how named entities do not adhere to promises the entity makes. In this case, AlphV writes that Dr. Poly Chen:
violates their own policy which states that “Patients can expect that all communications and records about their care will be confidential, unless disclosure is allowed by law” We have faced complete indifference from Poly Chen, Yonguen Cho, David Keen, Donald Winder and other top management representative of this business. They are receiving and reading our messages but still refusing to answer.
AlphV gives Pain Care Specialists until September 26 to contact them or all the data will be freely leaked.
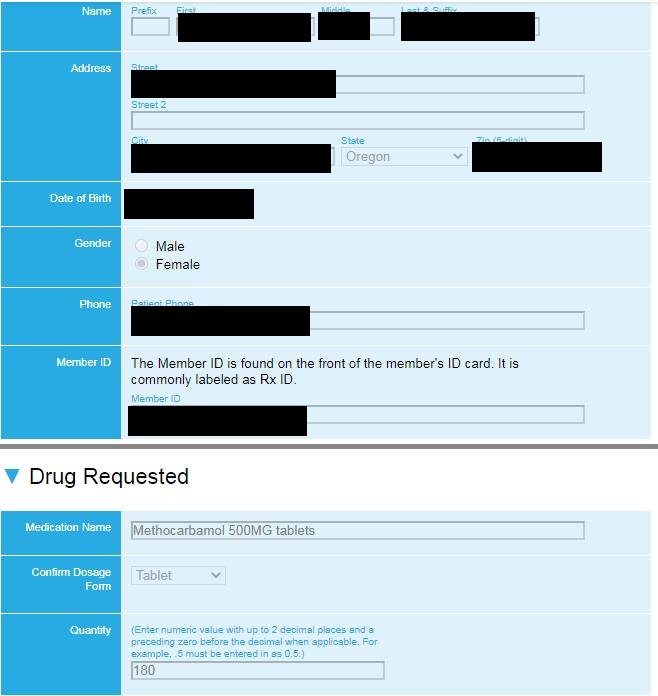
In an email to Dr. Chen and others on September 18, AlphV provided them with an update about data leaked from the network. In that email, a copy of which was openly cc:d to DataBreaches, AlphV claimed they had acquired:
– detailed information about employees (contracts, ssn, phone, home address, ID’s, drug screens, etc)
– doctor’s info (contracts, signatures, certificates, ssn, phone, home address, ID’s, etc)
– SCS/PNS/DRG Representative Information (phones, emails, etc)
– patient’s info (medical records, prescriptions, home address, contacts, ssn, etc)
– medical providers and controllers contacts
– partners and other business contacts
– access to electronical medical services (covermymeds, eCW/eMR, ORPDMP, and
– access to sensitive details about patients (phone numbers, SSN, medications given, etc, example below)
In addition to those claims, AlphV warned them that if they did not contact AlphV, “we will start informing contacts we found within your files about their data being leaked from your network. Of course we will make those calls exhausting for the subscribers we will be calling.” A list of names and phones numbers followed that.
AlphV followed that with a version of the carrot and the stick:
We are offering your management to pay us a fee for following services:
– we will provide tool to decrypt your files in case if you had no backup for them
– we guarantee complete deletion of your data from our servers
– we will provide data deletion log for your files from our servers
– we will give network improvement strategy which will help your IT security to become superior
– we will provide independent network penetration test of your network
– we guarantee you will never see us againIn case if management or representatives of “PainCare Specialists” will completely refuse to contact us until September 26th the opportunity to protect their data will expire and all the leaked data will be shared through web. When this happens a dozen of federal regulators will investigate your business slowing down your business processes, working licenses will be issued. Following reputation loss and possible court fines is higher than recovery fee we are offering you to pay.
It may be true that the amount being demanded might be less than certain incident response costs or consequences (the amount was not specified in the email and is not known to DataBreaches), but their statement seems to ignore the fact that the entity still has to notify and pay all those other incident response costs, and paying extortion just adds to the costs of the incident. Paying extortion or ransom demands does not seem to reduce the likelihood of litigation. Nor does it reduce the likelihood that regulators will investigate and either fine and/or impose a corrective action plan.
From the email, however, it is clear that AlphV claims to have locked them, so paying extortion may actually be cheaper than being down for days or weeks if they are unable to recover necessary files (that is, of course, assuming that they would be able to recover all their files if they pay). A maintenance notice on their website today indicates that they may be trying to deal with some issues.

DataBreaches sent an email inquiry to Pain Care Specialists early today to ask whether they did have a backup that they could use to restore files, and to ask other questions about the scope of the breach. No reply has been received.