When reviews of data breaches in the education sector are written for 2023, they will almost certainly mention the 2022 attack on the Los Angeles Unified School District that wasn’t fully disclosed until 2023 and the Minneapolis Public Schools breach. Both of those incidents involved threat actors leaking sensitive information on students. But any 2023 review will likely also need to include the attack on Clark County School District (CCSD) in Nevada for all of the student and employee data that was stolen and leaked.
In previous coverage, DataBreaches reported that CCSD claimed they discovered the breach on October 5, but had not been giving parents the kinds of information understandably anxious parents were seeking about their children’s information. Even after some parents reported receiving direct contact from the hackers who included copies of their children’s education records, and even after the hackers leaked information on more than 200,000 students, the district has not come out and forthrightly addressed whether the leaked data are real (they appear to be real and parents who received their children’s files from the hackers confirmed the files they received were accurate).
On October 25, SingularityMD (as the hackers call themselves) posted a statement on a code-sharing site and also contacted parents via Facebook. DataBreaches expected their post on the code-sharing site would be quickly removed by the platform once the district requested its removal, but it remained publicly available if one knew where to find it. Did the district even know it was there? On October 28, three days after the post appeared, DataBreaches noticed that it had not been removed and reported the post to the hosting platform. Less than 24 hours later, it was removed.
When the district’s incident response is reviewed, as it surely should be, someone should also be sure to investigate what steps the district took to find out where the data were being leaked and what attempts they made, if any, to get links to the data removed — from Facebook, from the code-hosting platform, and even from a tweet on X (formerly Twitter) that included all the links to the data.
Hackers reveal more details
Having established contact with SingularityMD, DataBreaches sent them some questions. The following are their answers, which DataBreaches has redacted or edited in places to correct typos or so as not to disclose sensitive information or links:
DataBreaches (DB): This is a somewhat stupid question but I have to ask: why “SingularityMD” as your name? Is there any connection to the professional service at that domain name?
SingularityMD (SM): The name was chosen at random. This has nothing to do with whatever else shares this name.
DB: Did CCSD respond to you at all or have they just ignored all contacts from you?
SM: We had a dialog with them where they were provided proof of life (a 1GB sample of the data). The day of the deadline they asked for an extension to attempt to run our request past the board but then did not reply from that point onwards. There were approx 12 emails back and forth.
DB: If you’re willing to say, how did you gain access to their network?
SM: We compromised a student account, then accessed information available to any student to escalate from there to teacher to systems level access for one or two systems. This was not a fancy high tech operation.
When DataBreaches asked how they were able to access the student’s account, they responded that they obtained the student’s date of birth (YYYYMMDD) from social media, and the email address from the student’s account on “TikTok, etc.” where the student ID had been used as the username because the student authenticated their school account when setting up the social media account. Asked to explain what information was available to any student that allowed them to escalate from the student’s account to teacher to systems level, they replied:
SM: Google groups and google drives, if not configured correctly will expose teachers and staff files and conversations. In rare instances teachers have created shared drives and given the google group access to this drive. So if one was to add themselves to the group, they can then also access the drive contents. Nothing fancy at all.
DB: Did you get any really sensitive student files like IEPs (Individualized Educational Programs) or psychological evaluations?
SM: We extracted the Google Group dedicated to IEP compliance across the district “SEMS IEP Compliance” which includes posts as far back as 2021. There are numerous posts to this group which include spreadsheets of full listings of IEP across the district by student and school. The largest spreadsheet by file size contains 43,000 student records including case managers, start and end dates etc. I believe we have multiple IEP PDF’s from another group that all will be uploaded in due course.
This is one group of many, I have included a screenshot of a selection of the google groups we have exported. We have exported groups which are linked directly to fax machines which we have not processed. Groups based on student registration which includes proof of identify for lots of parents. Groups with proof of identify for shared housing requests. There is also lots of google drive exports.
 |
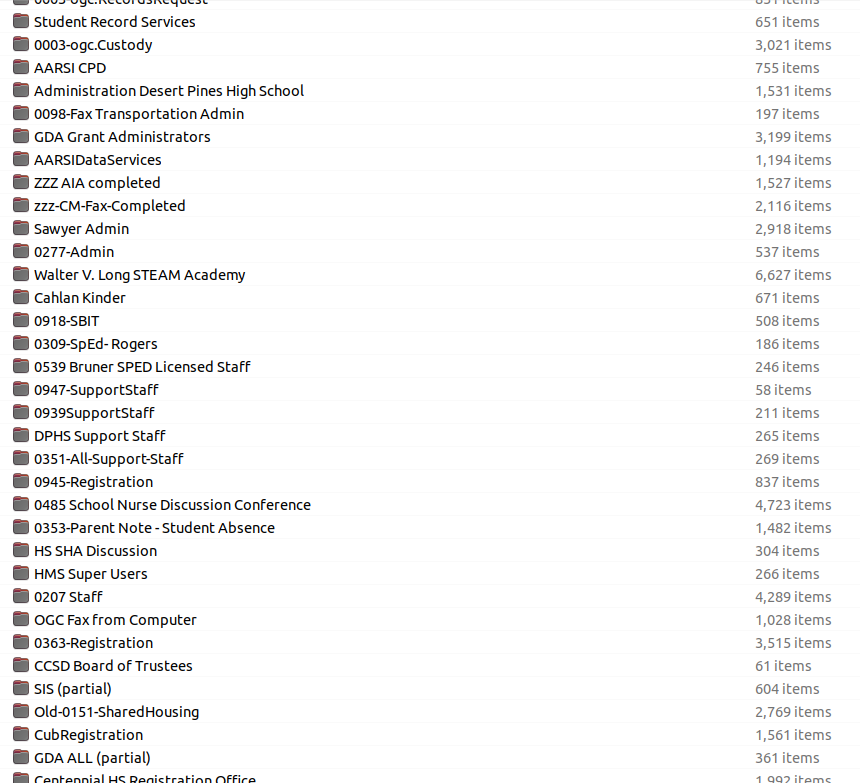 |
DB: How much more data from CCSD are you sitting on that you will leak eventually? Is it employee data, too?
SM: 474,436 items, totalling 68.8 GB Note that much of this is compressed. We have only leaked approximately 4 GB.
With respect to the question about employee data, they replied:
SM: No payroll or staff software was accessed besides Infinite Campus, I will talk about the serious issues with Infinite Campus after the next school is contacted. Extracts from the software HFM were placed on Google Drive and contained salaries and contact information for all staff as of 2022. Budgeting workbooks also include salaries.
DB: With all the schools out there, why did you pick CCSD to attack?
SM: CCSD is an easy target, all school districts are easy targets. The more people have access to any network the easier it is to access. Students’ accounts make for an easy access point. I would recommend school districts separate the student network from the teacher network to make this process harder for teams like us.
Noting that they had commented on CCSD’s password policies, DataBreaches asked directly if they picked CCSD because they were a former student or IT employee of the district. They replied:
“Simply was one of the earlier networks we managed to access. The note about their policies is from google group discussions (going back to 2016) where administrators would post annually when they have reset the passwords back to YYYYMMDD and giving teachers other instructions.”
SM also added some other comments to their reply to DataBreaches:
We would have obviously preferred they paid, so uploading this is not our priority but is necessary as we do already have access to a number of additional organizations which, as yet are oblivious to us. If you are astute you will notice from the news that we have sent emails from other school districts, these are typically instances where we have not been able to elevate our access above the student level and so are happy to use these as burner accounts.
For our next target we will reduce our fee for disposal of the documents from $80k USD to $15k USD as we would like to make this easily acceptable so that we can prove we will dispose of the documents upon receipt.
As a final note, as of last check yesterday, we still have access to CCSD at the teacher level.
DataBreaches sent an email to the district last night informing them of SingularityMD’s access claim and suggesting their IT personnel read this post for other details provided that might need to be addressed to prevent re-attacks or future attacks by others. As of publication, no reply has been received.