By “Dissent Doe, PhD” and “Batman”
March 7 started out fairly normally – until DataBreaches.net was hit with about 11 million requests in less than an hour. Most of them were from Russia, but of course, that didn’t prove anything. But it seemed clear that DataBreaches had ticked someone or some group off. Again.
Ticking off some ransomware groups or individuals is not exactly rare for this site or blogger. Then again, ticking off some victims is not exactly rare, either.
Did AlphV get mad because DataBreaches reported on their exit scam and fake listings? Or did LockBitSupp get mad because DataBreaches reported on their repeated failures to leak data after threatening they would? Or was it some clown this site reported on recently?
Who was behind this attack? DataBreaches still has no idea, but the attacks have continued every day since March 7. If those behind the attack are smart, they’ll never admit they have wasted so much money trying to take this little blog down.
Luckily for DataBreaches, several people—some with “white hats” and some with “black hats”—came forward to offer their help and expertise.
Enter—let’s call him “Batman” for now—stage left. DataBreaches will let Batman explain what happened next.
“I Think We Can Take Them” — Batman
A day or two after the attack started, I got involved. Since then, I have been involved on a daily basis to keep DataBreaches online.
Did I succeed? YES! How did I do it? Magic. Well, not really. Here’s a bit of how the attack has been mitigated:
The site’s backend server had been on the Akamai/Linode network and the attackers had found the backend. I moved the site over to new hosting and added a Content Delivery Network with enough servers to handle the large number of requests that started coming in. Since then, it has been a game of cat and mouse with the DDoSer. One day the DDoSer upgrades, one day we upgrade. All of his IP addresses are reported to Spamhaus, which has resulted in about 80% of their IPs being blocked.
On a daily basis now, there are about 850-950M Requests Per Hour. Sometimes there are about 30-40M Requests Per Minute, but those are short-term spikes. To mitigate those, we add new load balancers daily and reconfigure our firewall. Some screencaps of analytics at different times appear below. Short spikes generally have little impact.
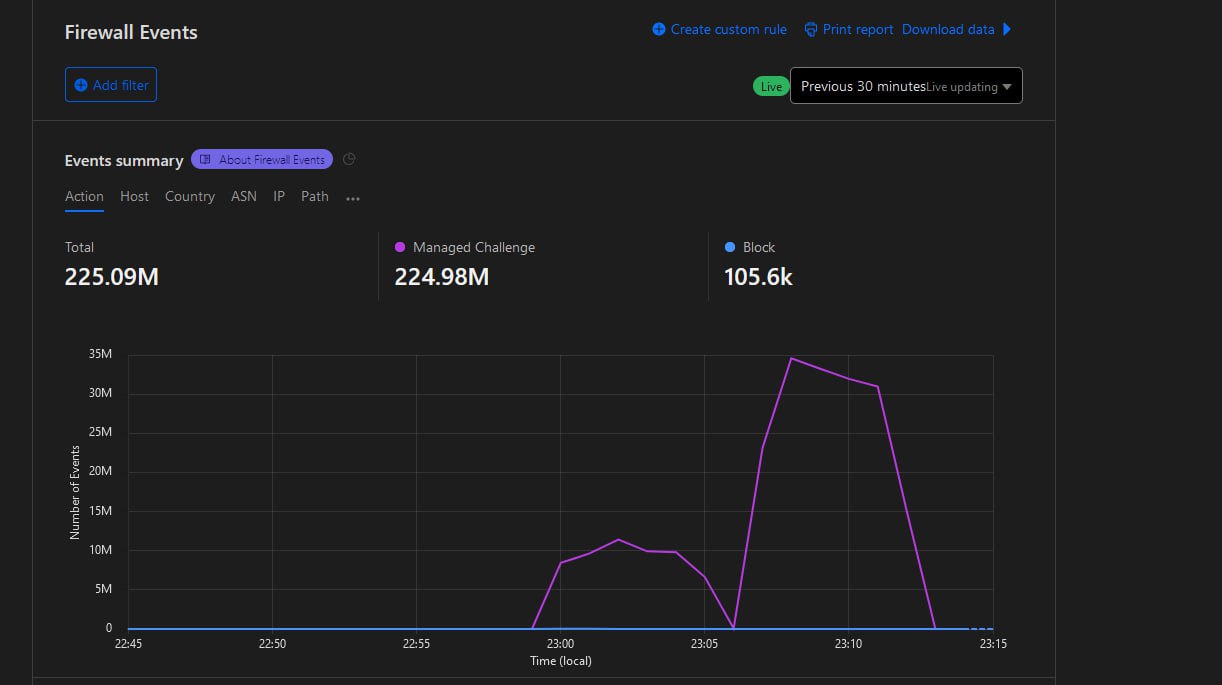
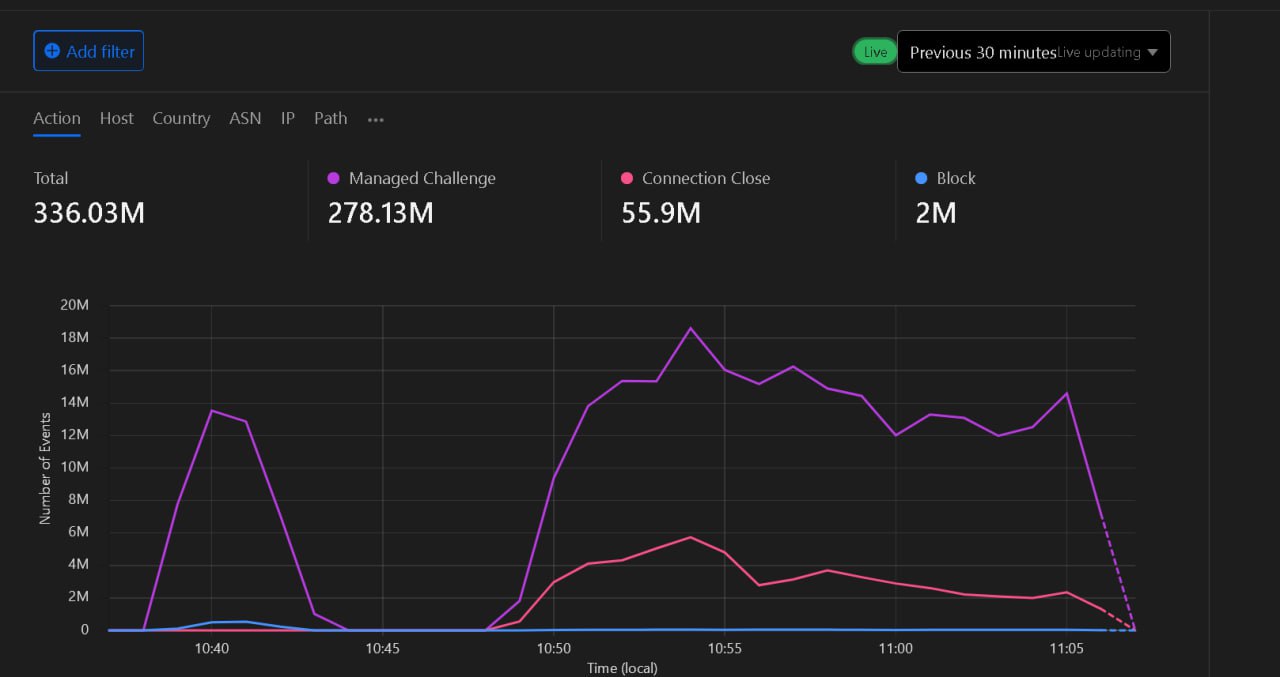
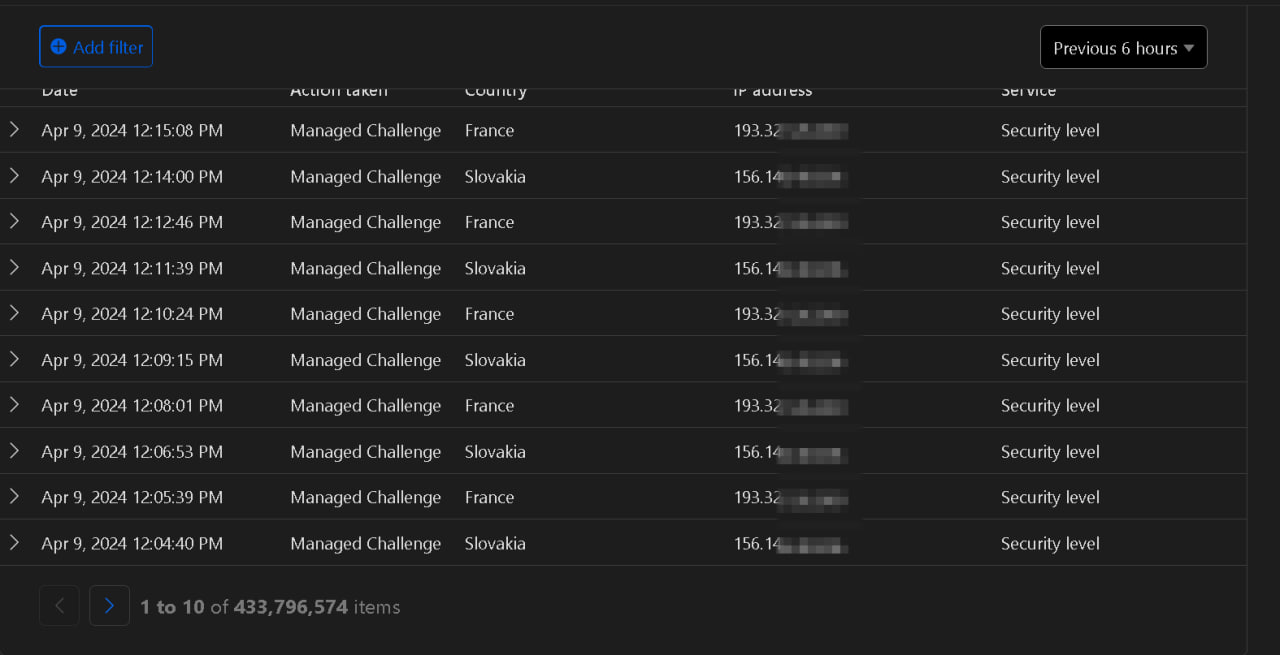
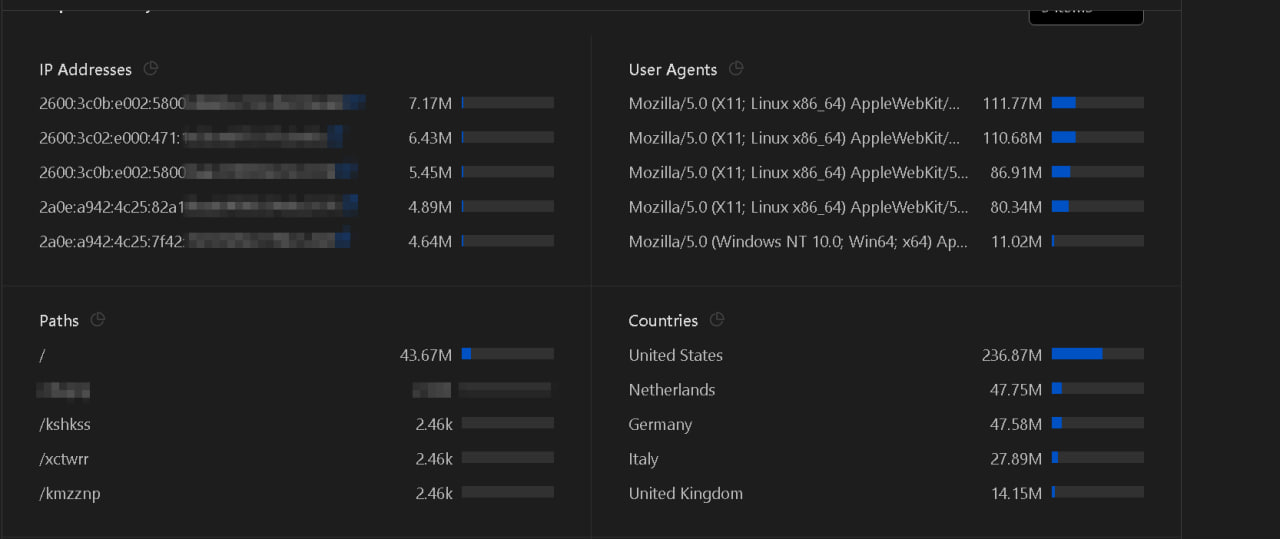
“I’m Still Here” — Batman
Special shoutout to the lame DDoSer: We are able to take more than 5B requests per hour, so we do not mind you adding more power to your attacks at all. Just kiss your customers goodbye.
To everyone else: What can we say? If you’re thinking of hiring a DDoSer, we would give a 1-star review to the DDoSer whose ToxID is C68B75E6722F0A678FDA7FB0713F60F857F937EA8A8C8B057FAE3752124A932C83CBC097C1D4 and suggest you save your money.
We do not know how much someone has paid him over the past 1+ month to DDoS this site, but they have wasted their money on him.
Update 1: It looks like the DDoSer had himself a little hissy fit after the post appeared. There were 24.7 billion requests in a 12-hour period.
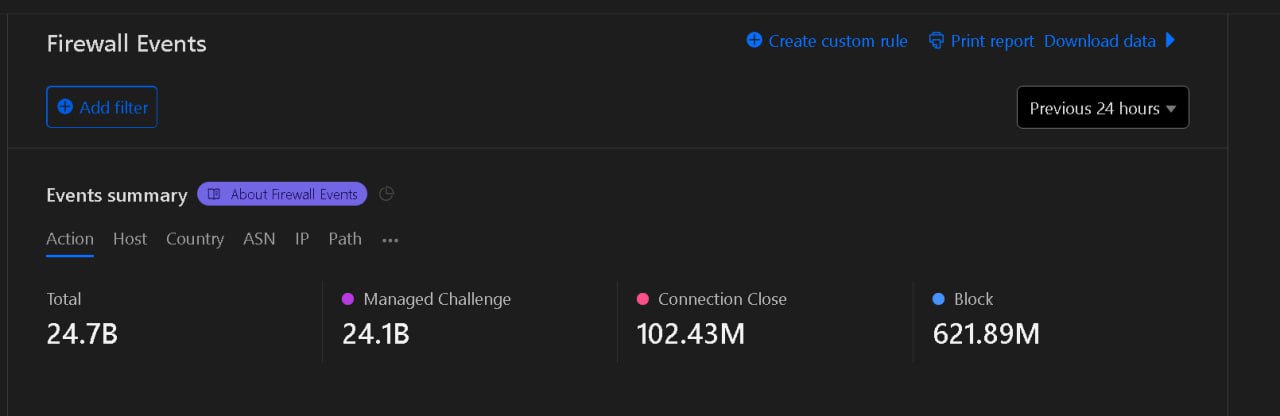
I just love this site. It’s far from dull.
Congrats, Dissent, for your courage and smarts in dealing with this guy. Welcome Batman! You rock.
Jeanne P.