Group Health Cooperative of South Central Wisconsin (GHC-SCW) is a non-profit, member-owned health plan providing services to more than 80,000 members in Wisconsin. This week, they provided reports to HHS and the Maine Attorney General’s Office about a breach they previously disclosed in February.
On January 25, GHC-SCW posted an announcement on its website that they had identified an intrusion in their network by an unknown attacker on January 24. On February 9, they updated their announcement. Now, they provide even more details, including that on January 24, they had promptly isolated and secured their network. As a result, the attacker’s attempt to encrypt their system was unsuccessful.
“As part of our response effort,” they write, “we reported the incident to the Federal Bureau of Investigation (FBI) and hired outside cyber incident response resources to assist us in restoring and verifying the security of our network and systems, and to investigate the attack. These resources successfully allowed GHC-SCW to bring our systems back online methodically and safely.”
Despite their quick detection and proactive response, the attackers were reportedly able to access and exfiltrate data:
On February 9, 2024, during our investigation, we discovered indications that the attacker had copied some of GHC-SCW’s data, which included protected health information (PHI). The PHI that the attacker stole may have included name, address, telephone number, e-mail address, date of birth and/or death, social security number, member number, and Medicare and/or Medicaid number. Our discovery was confirmed when the attacker, a foreign ransomware gang, contacted GHC-SCW claiming responsibility for the attack and stealing our data.
Although they do not name the foreign group, on March 9, Black Suit claimed responsibility for the attack on their dark web leak site. Their listing claims that both patient and employee data were stolen. Although they make a number of claims, Black Suit does not provide any proof of claims with the listing.
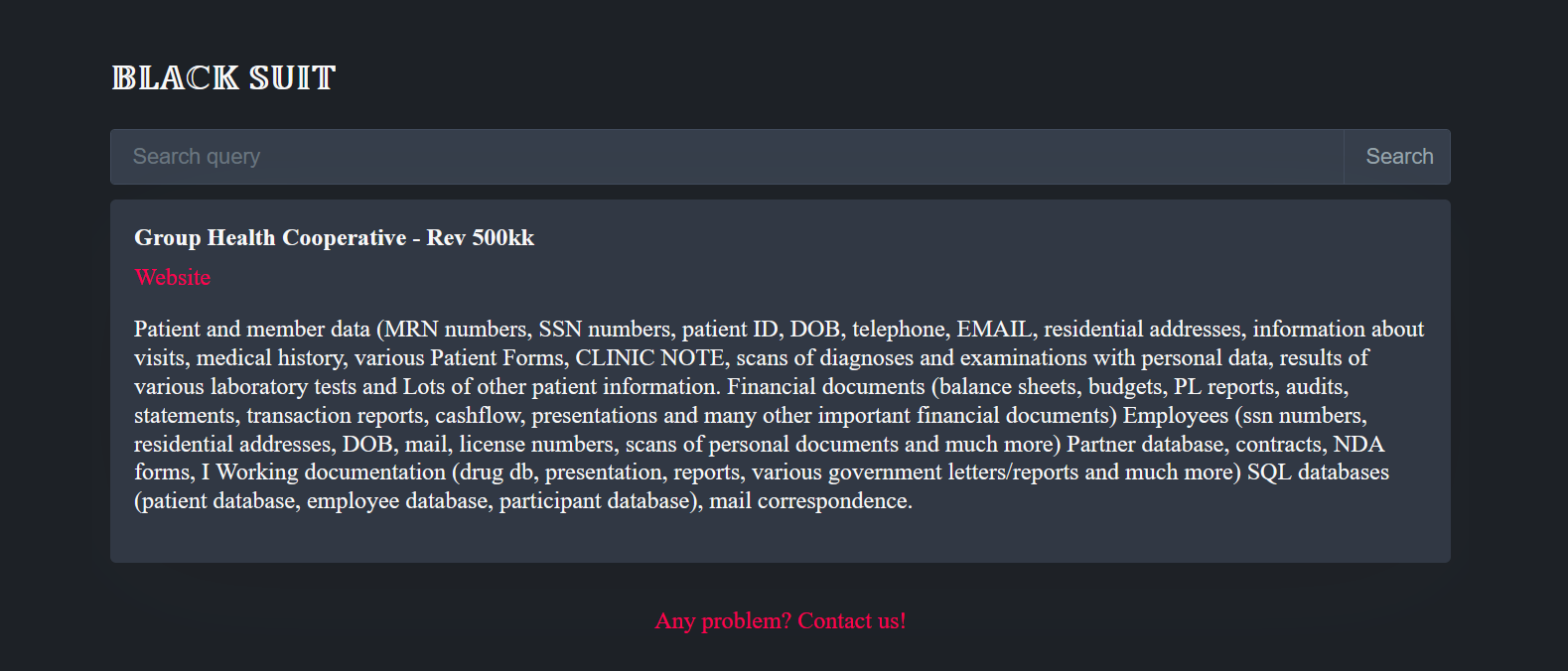
GHC-SCW reports they have no indication that information ahs been used or further disclosed, but the fact that a listing appears on BlackSuit suggests that the cooperative did not pay any extortion demand and that the threat actors may either leak data or sell it at some point.
A total of 533,809 patients were reportedly affected by the incident.