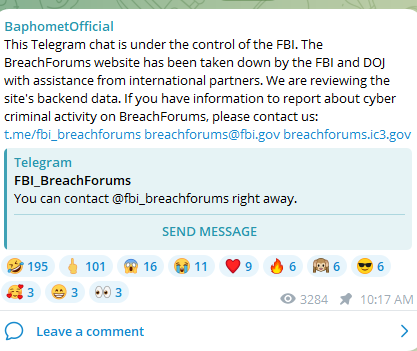
It probably will not surprise anyone who has checked BreachForums recently, but there is now a seizure notice on the forum. The notice claims that BreachForums is under the control of the FBI and has been taken down by the FBI and DOJ with assistance from international partners.
The forum’s owner, ShinyHunters, or whoever is currently in control of ShinyHunter’s telegram account, confirmed to DataBreaches that the seizure notice was real.
Two sets of recent postings on the forum may have contributed to the timing of the notice. The first was a leak of data from Europol posted by IntelBroker, a Russian threat actor who had also been responsible for posting the DC Health Links data in March 2023. That leak on the first BreachForums was soon followed by the arrest of “Pompompurin” (Conor Brian Fitzpatrick) and then in June, the seizure of the first BreachForums.
Now, more than a year later, IntelBroker, who became a moderator on the latest BreachForums, listed data for sale from Europol and provided some proof of claims. None of the documents in the sample were marked Classified, but some were marked “For Official Use Only.” The types of files he claimed to have had (and to have sold) included:
Alliance employees, FOUO source code, PDFs, Documents for recon and guidelines.
List of agencies within Europol breached:
CCSE
Cryptocurrencies – EC3
Space – EC3
Europol Platform for Experts
Law Enforcement Form
SIRIUS

Europol confirmed that there had been an incident but downplayed it somewhat, telling Bleeping Computer, in part, “No operational information is processed on this EPE application. No core systems of Europol are affected and therefore, no operational data from Europol has been compromised.”
But the Europol listing wasn’t the only listing likely to catch law enforcement’s attention this week. Three 0days (zero-day exploits) were put up for sale by a user calling themself “Cvsp.” One listing was for a VMware ESXi VME exploit (price $1.3 million), one listing was for a Windows LPE exploit (price $150,000), and the third listing was for an Outlook RCE exploit (price $1.7million).
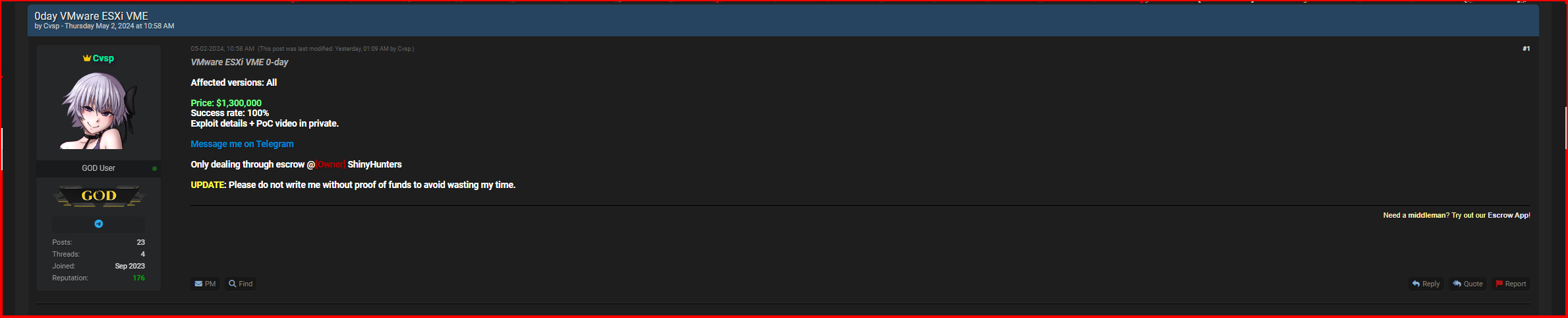
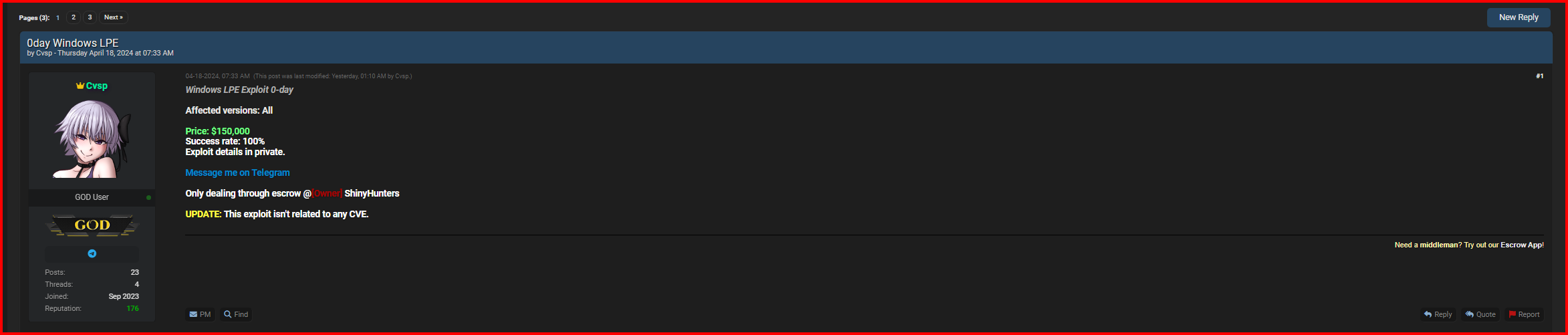
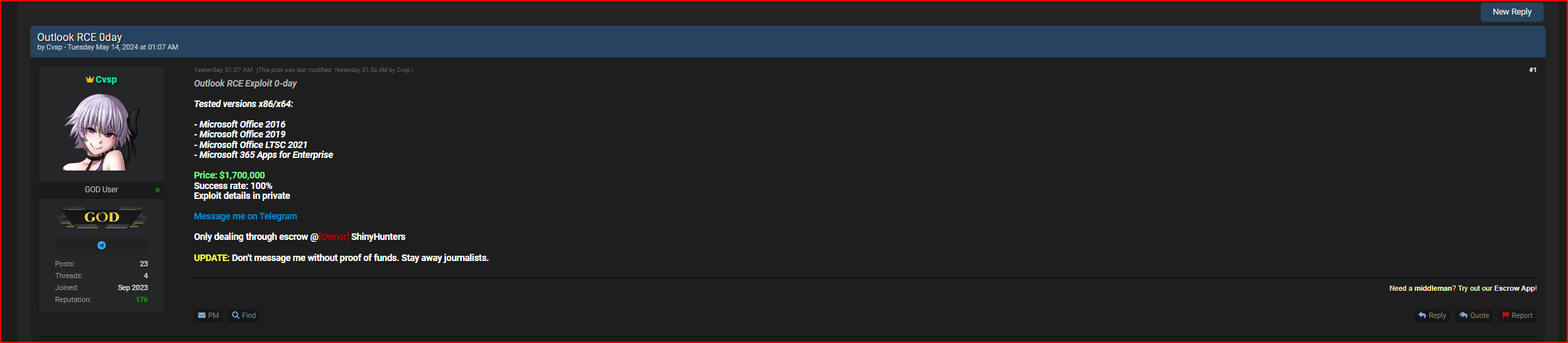
 Those 0day listings are likely to be taken seriously. Although they were posted by a relatively new user account, many people on the forum know that the user is a Russian threat actor who is a serious hacker.
Those 0day listings are likely to be taken seriously. Although they were posted by a relatively new user account, many people on the forum know that the user is a Russian threat actor who is a serious hacker.
In addition to the forum seizure notice, a check of Telegram shows that both BreachForums’ Telegram channel and the channel for the administrator known as Baphomet also have seizure notices. Bleeping Computer reports that IntelBroker claims that Baphomet has been arrested, but DataBreaches has been unable to reach IntelBroker to ask about that claim as he appears to have deleted the account he used to contact this site in the past.
The seizure notice shows avatars for Baphomet and one other person, both behind bars.
Updates
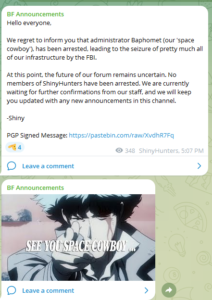
May 15: ShinyHunters informs DataBreaches that Baphomet has been arrested.
May 15: Shiny posts, “We regret to inform you that administrator Baphomet (our ‘space cowboy’), has been arrested, leading to the seizure of pretty much all of our infrastructure by the FBI. At this point, the future of our forum remains uncertain. No members of ShinyHunters have been arrested…..”
May 16: The splash screen seizure notice is gone and replaced with screens pointing people to a Telegram channel. ShinyHunters informed DataBreaches:
Lmaooo
I did beat fbi
recovered domain
and faster to recover backup
ShinyHunters has not yet answered questions about how they did that but later added
shit is going crazy
basically my telegram group chat just got wiped
and a guy called “dev” took it for me again
and he just got banned in real time
Another moderator wrote: “them doing this shit in real time to Dev show exactly how pissed and on their toes they are”
I got domain back too yep
The government has yet to issue any statements and has declined to comment when contacted by other news sites.

What is also not yet clear is why FBI seized the forum’s Telegram channel and Baphomet’s channel but not ShinyHunter’s Telegram channel. By yesterday afternoon, rumors already started circulating that ShinyHunters (the forum owner) was cooperating with law enforcement.
Correction: An earlier version of this post said the avatars in the seizure notice were for Baphomet and ShinyHunters. But the second avatar is not the the avatar ShinyHunters uses and ShinyHunters has not been arrested as far as this site knows. So who is the second person arrested if an arrest has already been made?