Executive Summary
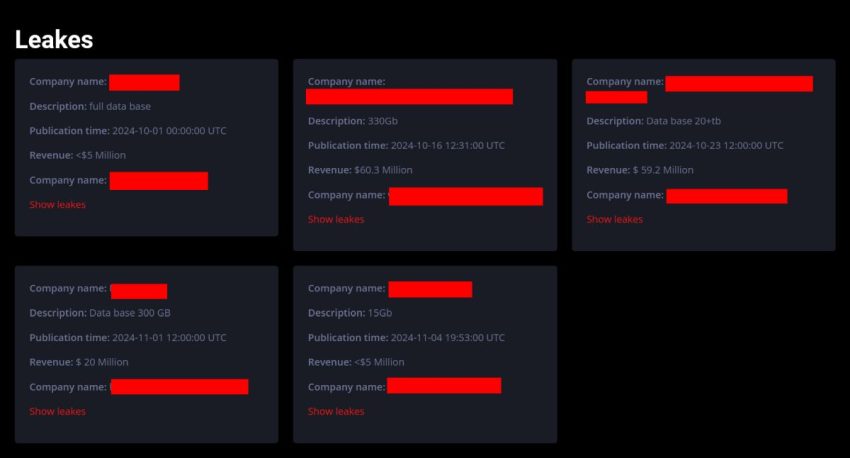
Trinity ransomware is a relatively new threat actor, known for employing a double extortion strategy. This method involves exfiltrating sensitive data before encrypting files, thereby increasing pressure on victims to pay the ransom. This ransomware uses the ChaCha20 encryption algorithm, and encrypted files are tagged with the “.trinitylock” file extension. Trinity operates a victim support site for decryption assistance and a leak site that displays their victims. It also shares similarities with two other ransomware groups— 2023Lock and Venus—suggesting possible connections or collaborations among these threat actors. The group’s tactics and techniques are sophisticated, making them a significant threat to the U.S. HPH. HC3 is aware of at least one healthcare entity in the United States that has fallen victim to Trinity ransomware recently.
Read the full profile at https://www.hhs.gov/about/agencies/asa/ocio/hc3/products/index.html#threat-briefs or below:
trinity-ransomware-threat-actor-profile