For many years, the FTC has published guidance for businesses to Start with Security. Their advice has always included having a clear way to receive security alerts about vulnerabilities. That advice has been repeated in all updates, including their 2023 version.
Why do I mention that now? Because once again, attempts to warn a company that they were exposing personally identifiable information of customers failed to be received or handled properly.
In this case, the company was Roomster. At the very least, they fail to have a clearly publicized and effective channel for people to use to contact them about security issues. Researcher @JayeLTee had to go searching through their entire site to find even one email address he could use to try to contact them and that was buried in their privacy policy page, where, if people read all the way down through the policy, they will find this small paragraph:
- Security. We implement reasonable security measures intended to protect against the loss, misuse and alteration of the information under our control. Please be aware that no data transmission over the Internet can be guaranteed to be 100% secure. As a result, Roomster cannot guarantee or warrant the security of any information you transmit on or through the Service and you do so at your own risk. If you wish to report a security vulnerability please send an email to [email protected].
That contact information should have been on the home page of the site or at least prominently linked from the home page. Their site also has no phone number posted to use to call them to alert them to a vulnerability or problem.
But apart from its failure to have a clearly publicized and effective channel to enable people to report security issues, Roomster failed to have an effective plan in place to respond to alerts from unknown individuals.
As JayeLTee reported on his substack, Roomster did not reply to his first notification that they were exposing customer data. In fact, they didn’t respond directly to any of three emails he sent them. They didn’t respond to DataBreaches, either, when this site reached out to their CEO on LinkedIn.
On January 3, DataBreaches published a post about Roomster, “No need to hack when it’s leaking: Roomster edition.”
Roomster Replies
On January 4, this site received a comment from Roomster’s counsel. A copy was sent via email to DataBreaches with a cc: to JayeLTee.
DataBreaches asked if they really wanted it posted as a public comment under the post, and they responded that they did want it posted publicly. You can read their full response here. It does not challenge any of JayeLTee’s findings but tries to explain or excuse their lack of response by focusing on the fact that both JayeLTee and Dissent Doe are pseudonyms and they were therefore suspicious and didn’t reply. Let’s dig into that a bit more.
In their response, they state that they did not respond to JayeLTee because he was unknown to them and had no real name or contact information. “Clearly you may know who JayeLtee is, but we do not and had every reason to believe that this was just a random contact or maybe even an attempt at “extortion”, counsel writes, adding later, “Subsequent to the letter we received a communication from @JayeLtee – again not knowing who this person was or is – but the issue had been resolved.”
Noting that they responded promptly when contacted by the NYAG’s Office, they also state that they did not even read my LinkedIn message to them: “We did not open it – again we have no way of knowing if this is an extortion attempt or a ransomware attempt or some other nefarious purpose. While it appears that “Dissent Doe” (you) and JayeLtee’s intentions were clearly honorable, we have NO WAY of knowing that and always proceed with caution in opening attachments and emails from what appears on their surface to be suspicious. This needs to be viewed in the light of us having immediately responded to the appropriate government officials and resolved any questions on the matter.”
DataBreaches is officially calling “b.s.” to their assertion that they had NO WAY of knowing that our intentions were honorable.
Did anyone even take one minute to search Google for “@JayeLTee?” It would have shown his moniker linked to researching leaks. Did anyone either look at Dissent Doe”s posts on LinkedIn or simply google “Dissent Doe?”
Caution is Fine, But is Failure to Investigate Negligent?
As Roomster’s counsel notes, in this day and age, everyone should be cautious about unsolicited emails from unknown parties. DataBreaches’ About page even acknowledges that in an entire subsection on verifying that contacts are genuine. It states, in part:
You can help yourself avoid a PR or regulatory nightmare by ensuring that you have clearly displayed ways for people to notify you of any data security concerns and by training your staff to escalate notifications. If they are concerned that the notifications are fake or a potential scam, they should not click on any links, but they should still get a supervisor involved or someone who can pursue the notice to determine if it’s real.
That particular paragraph has been part of the About page since 2020.
What did Roomster do when it got the first email from @JayeLTee? If they were cautious or skeptical, fine, but did they escalate the email to someone who would investigate it or did they just ignore it?
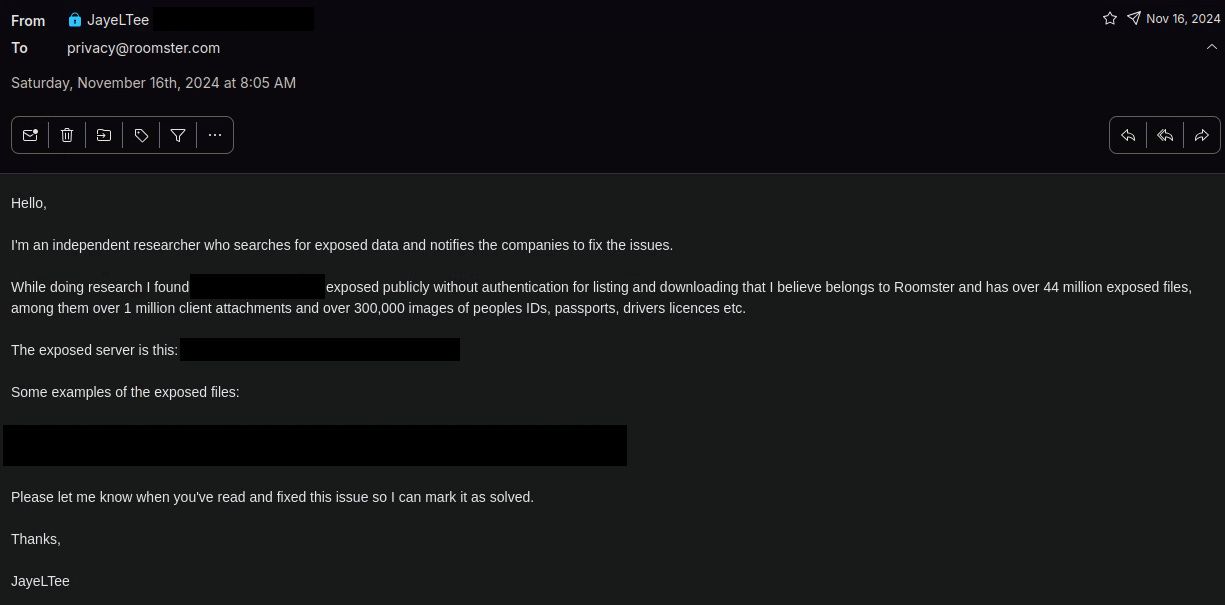
Note that JayeLTee’s email, redacted for publication, provided Roomster with specific information including the URL of an exposed Roomster bucket. It also provided them a few file links to exposed files so they could verify for themselves that it was Roomster’s data that was exposed. Anyone who handled their bucket for them would have recognized the bucket as being theirs and would have been able to safely check the links to discover that yes, their files were exposed without any authentication required.
So what happened in response to JayeLTee’s first email? Did any of their IT or security people even read it? And what would have happened if he had not persisted in trying to get them to secure their data?
As a reminder: some of our country’s founding fathers used pseudonyms to protect themselves. Some researchers use pseudonyms to protect themselves from companies that would harass them or try to tie them up in expensive litigation if they publish their findings. DataBreaches understands the concern. Being pseudonymous is not the same as being anonymous or unaccountable.
Good Advice from the FTC and Nam3L3ss
The FTC’s Start with Security advises businesses to:
Heed credible security warnings and move quickly to fix them.
When vulnerabilities come to your attention, listen carefully and then get a move on. In the HTC America case, the FTC charged that the company didn’t have a process for receiving and addressing reports about security vulnerabilities. HTC’s alleged delay in responding to warnings meant that the vulnerabilities found their way onto even more devices across multiple operating system versions.
Sometimes companies receive security alerts, but they get lost in the shuffle. In Fandango, for example, the company relied on its general customer service system to respond to warnings about security risks. According to the complaint, when a researcher contacted the business about a vulnerability, the system incorrectly categorized the report as a password reset request, sent an automated response, and marked the message as “resolved” without flagging it for further review. As a result, Fandango didn’t learn about the vulnerability until FTC staff contacted the company. The lesson for other businesses? Have an effective process in place to receive and address security vulnerability reports. Consider a clearly publicized and effective channel (for example, a dedicated email address like [email protected]) for receiving reports and flagging them for your security staff.
Businesses would do well to comply with the FTC’s long-standing guidance.
Responding to Roomster’s comment yesterday, another pseudonymous individual, “Nam3L3ss,” offered them some good advice about creating a responsive system. The problem with Nam3L3ss’s advice, however, is that unless Roomster changes their ways, they will continue to ignore alerts from pseudonymous researchers. Hopefully, this incident will result in Roomster making significant changes in their incident response and management in ways that are consistent with FTC’s guidelines.
