From the “Wait-What-Happened-Here Dept:”
On October 19, the Black Suit ransomware group announced that they had attacked Rutherford County Schools in Tennessee. Their listing, posted on their dark web site, included what appears to be an indication of what data and how much data they were able to exfiltrate. It did not indicate whether they encrypted the district’s files, or what any ransom demand amount was.
Unlike some groups that post proof of claims, Black Suit did not upload any screenshots or files to prove they had data.
More than two months later, the listing is still there, which suggests that district never paid any extortion demand, but there is no update and nothing to indicate that any data has been sold or leaked.
Did Rutherford County Schools ever make any statement about the October claims? DataBreaches sent an email inquiry about that.
Shortly after publication of this article, DataBreaches received a reply to this site’s inquiry about the Black Suit listing. James Evans responded:
We were not involved in a cyber-attack from Blacksuit in October. That was a different Rutherford County Schools.
So even though Black Suit specifically linked to and named the Tennessee district, RCS says it wasn’t them. That’s another example of why it’s always important to look for proof of claims.
Rhysida leaks sensitive data
On December 11, the Rhysida group announced that they had attacked Rutherford County Schools in Tennessee.
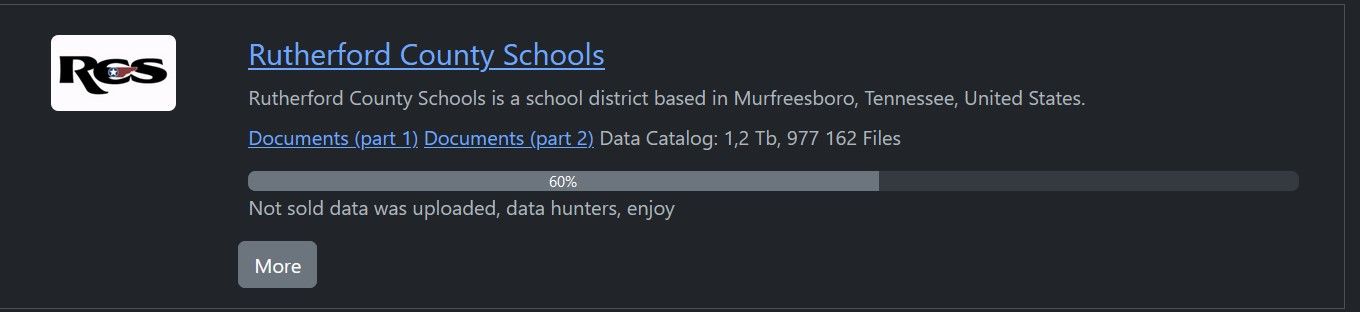
Current listing on Rhysida’s leak site. Image: DataBreaches.net
The current listing indicates indicated that 60% of 1.2 TB of data they claimed to have acquired was being leaked with a message, “Not sold data was uploaded, data hunters, enjoy”
The leak contains a great deal of sensitive records on students and employees. Inspection of some of the more than 9,000 files in a health records folder uncovered reports on students who were seeking or referred for home study due to physical or psychiatric issues. The reports contained detailed information on the student, the family, the reason for the referral for home study, any medications the student was on, and other details. Other files were health information requests with reports from physicians, allergy action plans, and other medically- or health-related information on named students. The files that DataBreaches skimmed appeared to be from 2015 – 2022.
Other files in a folder of SPED (special education) records also contained a great deal of personal information on students and their families, as these records often contained reports with psychoeducational evaluations for students who had been referred for special education services and an Individualized Education Program (IEP) or 504 Accommodation plan. Such evaluations contain IQ testing, interviews, academic achievement tests, physical examination reports, and social histories. There appeared to be about 30,000 files in .pdf or .tif format. Many of the .pdf files had a coversheet that indicated the files were for scanning. The cover sheets conveniently provided the student’s name, date of birth, student ID number, and Social Security number.
There was also a folder from Human Resources that contained thousands of employee files such as contracts, direct deposit applications, and other employment-related information. DataBreaches spotted forms with employment contracts with full Social Security numbers, photo IDs, and transcripts. The files skimmed appeared to be from 2015 through October 2024. As a quick estimate, there appeared to be about 30,000 files.
The release of the student and personnel information is likely to cause significant distress to the students, parents, and employees. The data that DataBreaches skimmed were all in .pdf format or .tif (for the larger evaluation packets of students). DataBreaches did not examine the entire tranche to see if there were any databases that might make misuse of information more convenient. But as inconvenient as .pdf files or .tif files might be for criminals, they still pose a significant risk to individuals whose information can be extracted and used for purposes of identity theft or to embarrass or extort families or former students.
Whether the threat actors have really sold any data or will be leaking any more data is unknown to DataBreaches at this time.
Protect Yourself
As a reminder: FERPA, the federal law protecting the privacy of education records, does not require a school district to send parents or students individual notifications of a breach involving a student’s personal information or education records. Nor does it require notification to employees of any breach of their information records.
Notifications may be required under Tennessee state law, however.
Former or current students over the age of 18, their parents, and current and former employees would be prudent to immediately place a security freeze on your credit report if you have not done so already. See this information on how to place a security freeze from USA.gov.
There is no fee to place a security freeze on your credit report, and if you ever need to lift it, it can usually be lifted over the phone quickly and then restored when you want it restored. It will prevent criminals from opening accounts using your identity information if a credit check is required to open the account. It will not prevent criminals from opening accounts using your information if a credit check is not required. For that reason, everyone who had their information stolen should consider filing a police report so that there is a record that your information has been stolen. Current and former employees may also wish to notify their banks and credit card issuers that their information has been compromised so that they can update any passwords and put a flag on the account in case of suspicious behavior.
If you login to bank accounts online or conduct transactions online, this might a good time to run a security scan on your computers and devices to make sure they are clean. Then change your passwords on your important accounts and add two-factor or multi-factor authentication so that no one can access your bank account online without that second authentication protection.
Those under 18 years of age should not have any credit report unless they had been authorized to use a parents’ credit card at some point, but parents may want to verify that their minor child has no credit report. See this information on how to check from the Consumer Financial Protection Bureau.
Current Status of the Breach
The district reportedly first discovered the breach on November 25, when the district’s network system became disrupted. Anosha Shariq of VPNRanks reports that the data were leaked after the district failed to comply with a $2 million BTC ransom demand.
The district reopens today after the winter break and classes for students resume tomorrow.
The most recent update on the district’s website was posted on December 27:
Latest updates: RCS network disruption
December 27, 2024
As you are aware, Rutherford County Schools experienced a network and systems disruption on November 25, 2024. Our team has been investigating this matter, with the assistance of third-party cybersecurity specialists, to determine the nature and scope of the event.
The cybersecurity specialists have informed us that some employee personal information was subject to unauthorized acquisition. We do not believe it includes all of our employees, but we are conducting a thorough investigation. In addition, some student information was subject to unauthorized acquisition.
The investigation will include a thorough review of the data that was potentially impacted. Once our review is complete, we will notify affected individuals in accordance with applicable laws.
Thank you,
Jimmy Sullivan, Ed.D
Director of Schools
Rutherford County Schools
