Patients not told their nude photos had been leaked on the internet.
There’s a follow-up on one of the plastic surgery ransomware attacks this site first reported in October 2023 after the Hunters International threat actors added Jaime S. Schwartz, MD, to their leak site with proof of claims.
At the time, Dr. Schwartz’s practice was one of a number of attacks on plastic surgery practices where threat actors posted some nude photos of patients and attempted to extort the surgeons by threatening to post all the patients’ nude photos with their names and details. And if the physicians refused to pay, some of the threat actors began attempting to extort the patients directly via website posts and phone calls offering to remove their data if the patient paid them.
As DataBreaches reported, Schwartz ignored attempts to acquire further information about the alleged breach and there was no evidence that he reported the incident to the California Attorney General’s Office or the U.S. Department of Health and Human Services. Periodic checks of HHS’s public breach tool found no indication that the incident was reported to HHS’s site for breaches affecting more than 500 patients.
Now CourtWatch, in collaboration with 404 Media, reports that a class action lawsuit has been filed against Schwartz by eight “Doe” patients. The complaint alleges the doctor did not timely notify patients that his practice was allegedly hacked twice by Hunters International.
Hacked Twice
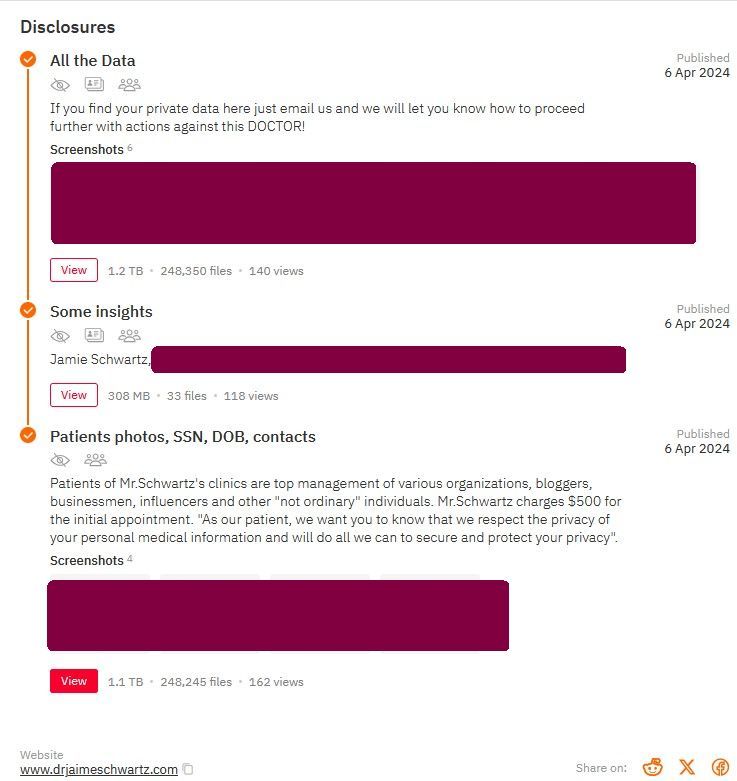
The complaint, which was filed in federal court in the central district of California, alleges that in or about September and October of 2023, Hunters International downloaded 1.1 terabytes of patient data, reflecting almost 250,000 unique files. The private data included, among other things, nude photographs and video of patients taken during the course of treatment, including images with both their faces and private parts visible, and images taken during surgery reflecting their surgical procedures.
That allegation is consistent with what Hunters International (“Hunters”) posted on their leak site and the proof of claims they posted, as DataBreaches reported at the time.
According to the complaint, Schwartz did not notify his patients of the breach at the time or make other required notifications. The plaintiffs allege:
“Approximately six months later, in March of 2024, Dr. Schwartz’s system was hacked a second time. On information and belief, the hackers again gained access to his entire system and all or substantially all patient data,” the complaint alleges. “Once again, however, Dr. Schwartz attempted to sweep the second hack under the rug. He failed to notify his patients as required by federal and state law. He waited to do so until after the hackers posted a public website (the “Hacker Website”), announcing the hack and leaking patients’ names, contact information, and nude photographs, and began contacting his patients directly.”
That last statement is a bit misleading, perhaps, as by November 2023, after the first hack, the threat actors had already posted some nude photos on their leak site.
Notifications?
One section of the complaint asserts that defendants were obligated to comply with HIPAA. But although it would seem likely that Schwartz would be a covered entity under HIPAA, there is no evidence on his website that he is. HIPAA covered entities are required to post a HIPAA Privacy Notice on their websites if they have a website. There is no HIPAA notice on Schwartz’s website, and the privacy notice on the site does not mention HIPAA at all. Nor is there any mention on that site of Schwartz accepting health insurance or billing insurers. If he does not engage in certain electronic transactions, he may not be a HIPAA covered entity, even though he has an NPI number and is a licensed and board-certified plastic surgeon.
But even if it should turn out that Schwartz is not a covered entity under HIPAA, his practice is still subject to California laws and laws of other states that require notification. Yet according to the complaint, not only did Schwartz not notify patients, but when patients called to ask, his staff allegedly minimized the breach, claiming only a few patients were affected.
According to the complaint, in a January 2025 notification to patients, Schwartz writes:
Our office discovered on June 27, 2024, that an unauthorized third party utilized a third-party vendor’s credentials to access the practice’s medical billing and practice management system. Upon discovering the incident, we engaged a specialized third-party forensic incident response firm to conduct a forensic investigation and determine the extent of the compromise. The investigation determined that data was acquired without authorization. After electronic discovery, which concluded on January 2, 2025, it was determined that some of your personal information was present in the impacted data set. We then took steps to notify you of the incident as quickly as possible.
If Schwartz is a HIPAA covered entity, he may find himself in hot water with HHS over these alleged incidents, apart from any civil litigation by plaintiffs. He may also find himself in hot water with California.
A search of Schwartz’s discplinary record shows that he received a public reprimand in February 2024 from the Medical Board of California. The record shows the accusation:
From May 2020 through March 2021, you aided and abetted the unlicensed practice of medicine and violated the ban on the corporate practice of medicine by engaging in a contractual relationship with a lay corporation (Orange Twist, LLC) that directly or indirectly controlled your medical practice at multiple Orange Twist med spa clinic locations throughout California, as more fully described in Accusation No. 800-2021-081344.
The accusation had been filed in February 2023. Schwartz agreed to a stipulated settlement and disciplinary order that required him to pay the board $221,924.75 for the costs of its investigation and enforcement action, to take an education course of his choosing, and a professionalism (ethics) course. No other charges seem to have been filed against him as of publication. Whether his patients may file charges against him with the medical board — or if they already have but it has not yet been made public — remains to be seen.
Schwartz was asked via his site’s contact form if he had any comment on the lawsuit. No reply was immediately available, but this post will be updated if he issues a statement.
Lawsuits against other plastic surgeons have yet to be resolved, but a lawsuit against Lehigh Valley Health Network that included the leak of nude patient photos by threat actors was recently settled for $65 million.