Bradford Health Systems in Alabama has posted a security notice on its website this week about an incident affecting employee and patient data. It begins:
On December 8, 2023, Bradford Health detected unusual activity within its network. Upon discovering this activity, it immediately initiated an investigation of the matter with the assistance of third-party cybersecurity specialists. The investigation determined that certain files stored on the network may have been accessed and acquired without authorization. After a thorough review of those files, which concluded on May 15, 2025, Bradford Health determined that certain individuals’ personal and/or protected health information may have been affected.
The potentially affected information reportedly includes: individuals’ names, driver’s license numbers, dates of birth, medical information (including diagnosis and treatment information, physician names, and Medical Record numbers), health insurance information, financial account numbers, passport numbers, payment card numbers plus a means of access to the account, and/or Social Security numbers.
Letters were sent out to those affected on May 30, 2025.
There is no offer in the website notice of complimentary mitigation services to those affected. Perhaps there is something in the actual individual letters, but despite Bradford’s statement that there is no evidence of misuse of the data, how could patients know to contact them if they never knew of the incident? Did Bradford ever post a media notice back in December 2023 or early 2024?
Ransomware Attack and Data Leaked
DataBreaches cannot find any entry on HHS’s public breach tool reporting any incident for Bradford Health, so we do not know how many patients were affected by this incident and how many employees were affected. But here’s what we do know:
On January 4, 2024, the Hunters International ransomware group added Bradford Health to its leak site. The entry indicates that they encrypted files and exfiltrated more than 760 GB of files, including personnel and patient data.
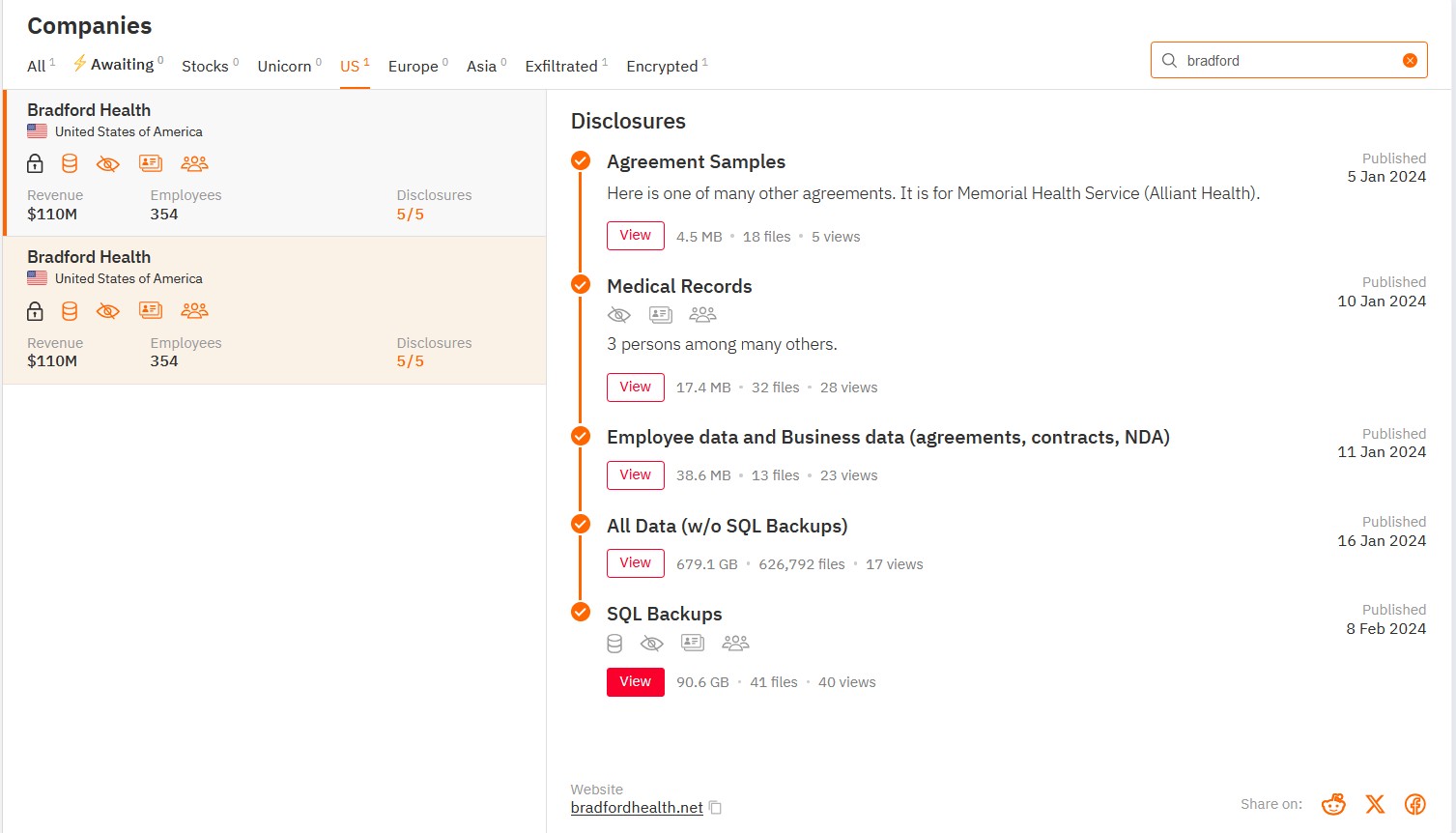
Between January 5 – February 8, 2024, Hunters published data, including a small sample of patient data and employee data. The file names of some of what they leaked remains on Hunters’ leak site, but the links no longer work to access the data. DataBreaches could not confirm whether Hunters ever leaked all of the data or not, and the threat actors do not provide any contact information on the site.
In January 2024, the breach entry on Hunters was reported on X.com (formerly Twitter) and other sites that scour the dark web for ransomware attacks. The listing on Hunters’ dark web site indicates that the leaked files were accessed on at least a few occasions.
But what happened to the data? Does Hunters still have all of it? Did they sell any of it? Bradford Health is known for its addiction and recovery services. The patient data may be quite sensitive and could potentially cause social or employment issues for patients. Were patients ever told that their data was leaked on the dark web?
DataBreaches emailed Bradford Health with some questions about the incident and their response. DataBreaches also reached out to two employees who had personnel files leaked in the Hunters proof of claims to ask them if their employer notified them of the breach at the time or the leak of any of their data. DataBreaches was unable to locate contact information for three named patients.
No replies from Bradford or the two employees were immediately available, but this post will be updated if replies are received.
The employees nor the patients were notified of any information leaked.
It was business as usual