While some of us were considering whether Hunters International was in the process of re-branding as World Leaks or not, World Leaks was busy adding a hospital to its leak site.
Kentfield Hospital in California is a critical care hospital that specializes in treating patients with complex medical needs who require an extended period of time for recovery in a hospital setting. It is one of Vibra Healthcare’s facilities.
Patient Data Involved
Although it has not been publicly leaked yet, DataBreaches was able to preview the data tranche and found that although it did not contain any EMR databases, it did contain a lot of protected health information on named patients.
There were folders with patient names as part of the folder names, with files relating to their admission, treatment, and discharge. For any one patient, there might be more than a dozen files with detailed information.
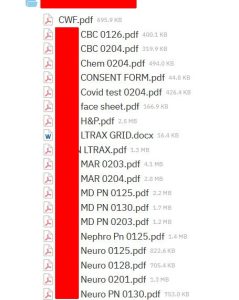
Figure 1 is a redacted screenshot showing a partial listing of files in one patient’s folder. Kentfield seemed to use a folder and file-naming convention that includes the patient’s first and last name for the folder name and their last name for individual files. Individual filenames also incorporated something about the content or subject of the file as well as the month and day. None of the files in this particular folder were encrypted or password protected. They contained a wealth of personal and protected health information with name, date of birth, medical record number, financial record number, diagnoses, medications, care, test results, etc.
Admissions-related folders contained patient folders, mostly from 2020 and 2021, but also with the first months of 2022.
Other patient-related files from 2023 and 2024 were noted, including investigations of complaints involving patient care, and quality improvement reviews initiated by CMS as part of its peer review processes
The tranche contained more than 28,000 image files where patients’ names and portions of their anatomy had been photographed to document wound care or other treatment issues.
Hundreds of files related to patients’ health insurance were also involved. Most of them were verification of insurance files, but some involved billing information.
DataBreaches did not check all of the files in the tranche, but with one exception, all of the patient-related files that were checked were unencrypted. The only password-protected files that DataBreaches noted were in a folder that indicated the files had come from Kaiser.
Personnel Data Involved
No databases involving detailed personnel information or payroll information were spotted, but there were a some files involving disciplinary issues and termination reports involving named employees. One file of new employee hires contained names, professional roles, and date of birth. DataBreaches did not find any files with Social Security numbers or W-2 data.
Kentfield’s Response
There is nothing on Kentfield’s website to alert patients or employees to any incident involving personal information. Because World Leaks claims that they do not encrypt systems or files, hospital functions and patient care may not have been disrupted by this incident, but the hospital would appear to have a reportable breach that will require notification to HHS, California regulators, some personnel, and patients.
DataBreaches submitted a contact form inquiry to the hospital this morning, asking when they first discovered a breach and what they were doing in response to it. No reply was immediately received. This post will be updated if a reply is received.
World Leaks declined to discuss the attack in terms of when they gained access and whether Kentfield had responded to them at all.