Ever since law enforcement announced the arrest of an administrator of the XSS.is forum, forum members watched threads disappear from the site, and then a seizure notice splash screen appeared. No administrator or moderator had made any statement about the arrest or situation despite pleas from forum members for some clarification, and attempts to discuss it were quickly deleted.
The concerns and speculation continued over on Exploit.in, where many members of XSS.is also have membership. Members noted that one of the police photos revealed paper wallets with some details visible, saying, “I wonder if user deposits are stored in that stack of paper wallets. One of them even has the private key exposed there.” Another forum member replied they spotted, “Checks from PrivatBank, an envelope from the post office, Monobank cards, a Kyiv Stara SIM card, a foreign passport, a child’s birth certificate (I think) – my own certificate, and waste paper for the house, apparently.”

Recovery Under Way?
Earlier today, “Admin” (aka “Root”) from XSS.is posted something that recovery efforts were underway and that there was a new onion address as part of the recovery.
The clearnet version of the site was still seized, but as we saw with BreachForums when ShinyHunters was able to regain control of their domain, it appeared that the government’s efforts to seize the onion version of XSS.is may have been short-lived vain and that the forum’s onion site could be revived. Throughout the day, the onion site could be reached for varying amount of times. But of concern, although users could connect to the old onion address, they would be redirected to the new onion address after successfully completing hcaptcha.
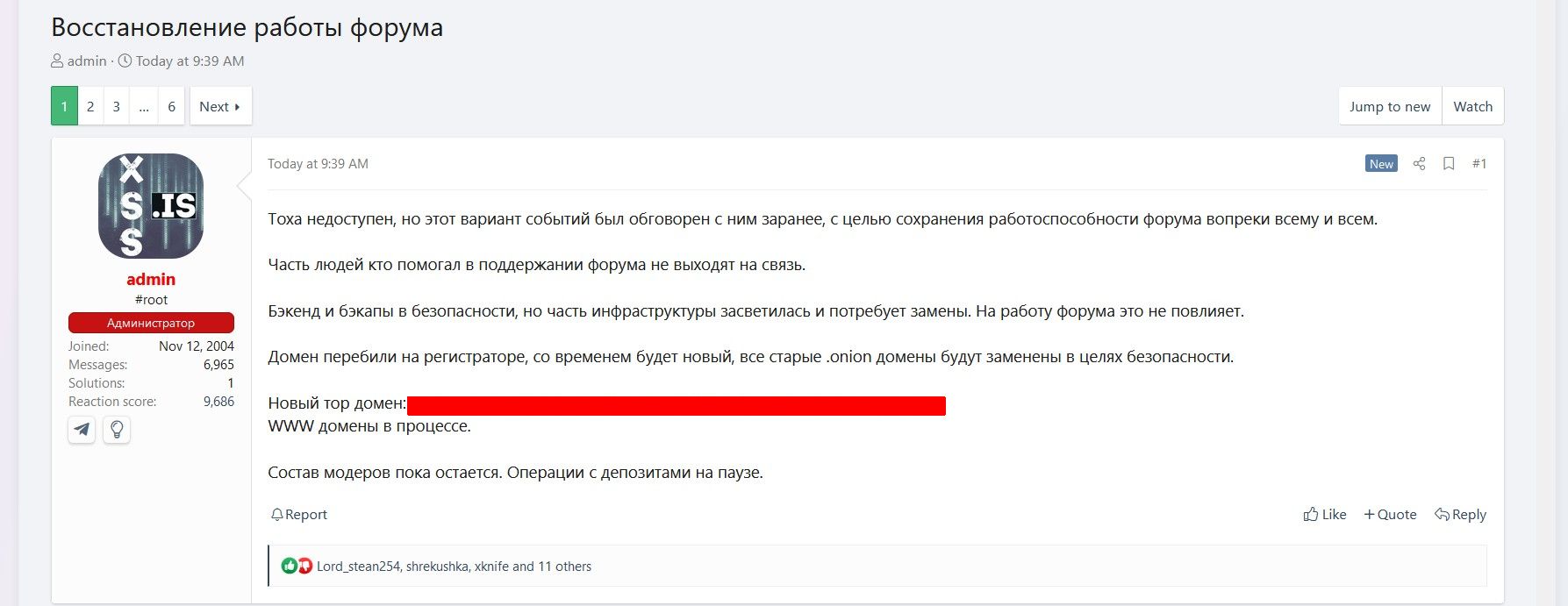
Machine translation:
![Tokha is unavailable, but this scenario was discussed with him in advance, with the goal of maintaining the forum's functionality in spite of everything and everyone. Some of the people who helped maintain the forum are not getting in touch. The backend and backups are safe, but some of the infrastructure has been exposed and will require replacement. This will not affect the forum's operation. The domain was changed at the registrar, a new one will appear over time, all old .onion domains will be replaced for security purposes. New tor domain: [redacted onion address] WWW domains in progress. The moderators remain in place. Deposit operations are on hold.](https://databreaches.net/wp-content/uploads/xss_onion_en2-e1753398332547.jpg)
But Are Appearances Deceiving?
But was this really the Admin #root who posted that? If Toha was unavailable (because he was the one presumably arrested), and “some of the people who helped maintain the site were not getting in touch,” how could forum members determine whether this “root” was really someone from XSS.is or whether the post and new domain were being operated by law enforcement officials?
By the end of the day, that concern still had not been really resolved and probably will not be resolved until someone who is really known to forum members appears and can be authenticated not only by what they know but also by members’ ability to recognize them as the same person they had dealt with in the past.