In their newest escalation of activities since saying “goodbye” and then determinedly trying to create more chaos on Telegram. the Scattered LAPSUS$ Hunters collective (for lack of a better word right now), has opened up a leak site in both clear net and onion versions.
In its debut, the group has targeted Salesforce, and is attempting to pressure them by threatening to leak their clients’ data if payment is not received by October 10.
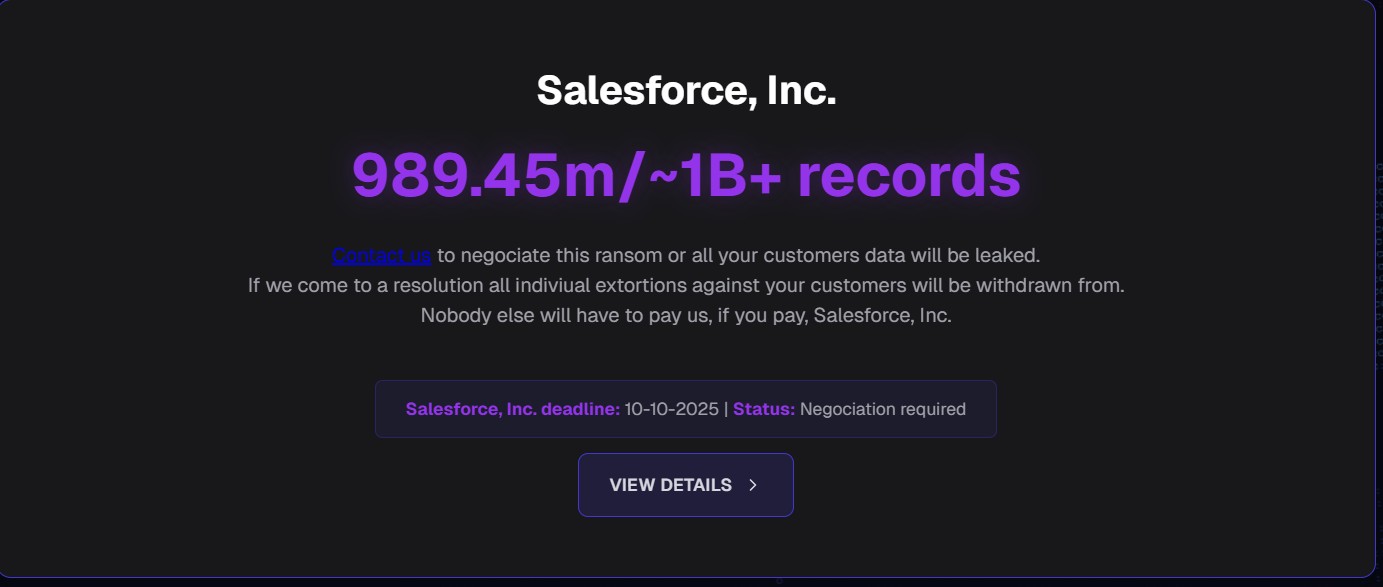
Salesforce, Inc.
989.45m/~1B+ records
Contact us to negociate this ransom or all your customers data will be leaked.
If we come to a resolution all indiviual extortions against your customers will be withdrawn from.
Nobody else will have to pay us, if you pay, Salesforce, Inc.
Salesforce, Inc. deadline: 10-10-2025 | Status: Negociation required
Dozens of listing of individual Salesf0rce-related targets follow. For each entity, the listing indicates the date that they were compromised and the size of the data tranche (in GB). Each listing also provides a summary of what types of information or files are involved and there is a sample of data from each target.
A listing of the individual companies with their compromise dates and size of files is provided at the bottom of this post. The site currently lists 39 targets, but as ShinyHunters emphasizes, those are often the parent companies. As an example, he tells DataBreaches that Disney and Hulu were both affected as individual companies, but because Disney owns Hulu, they are listed together on the leak site. He also notes that “there have been numerous other companies that haven’t been listed for reasons I can’t comment on.” One reason he would not be able to comment on them would be if they had paid the ransom demand. If there are other companies that haven’t paid and yet haven’t been listed, the reasons for that are not known to DataBreaches.
Preliminary inspection of the site contents indicates that some of the entities were attacked in early 2024 while some were attacked more recently. Many of these entities have never publicly disclosed their breach.
Because Salesforce is used for customer relationship management (CRM), DataBreaches reminds everyone that some customer data can be problematic by revealing the contact information for people who can then be targeted with phishing attacks or other social engineering attacks. As one example, DataBreaches noted some very expensive purchases by customers in the Kering breach data shared with this site. Records such as those, or those of Chanel’s New York customers, can provide fraudsters with the names and contact information of high-wealth individuals.
Businesses like FedEx and USPS or even retail merchants that record customers’ names, postal addresses, and phone numbers can also put people at risk of becoming targets of phishing or social engineering attacks.
Even worse, perhaps: some seemingly benign data can also put named individuals at risk of political violence or targeting. In this type of situation, DataBreaches includes the Home Depot incident, because Home Depot has a file devoted to government employees that includes their name, email and postal addresses, and phone numbers. Inspection of the sample data reveals that the customers are a mix of federal, state, and county employees. While not all customers provided all the data types, many in the sample did, and some appeared to have provided their home addresses and not their work addresses. DataBreaches has emailed Home Depot to ask if they will be notifying all customers about this breach. No reply was immediately available, but DataBreaches will update this post if a reply is received.
DataBreaches also checked the Walgreens listing to determine if it contained any patient data. It appears to be all employee data, with the sample containing information on more than 1,000 employees. The listing claims that the data includes name, email address, phone number, residential address, date of birth, Walgreens internal account IDs, and other employee information. Although there are fields for “phone” and “Mobilephone,” the sample data had “null” in each of those fields. Whether are data or tables in the full data set have actual phone numbers is unknown to DataBreaches, but with the job titles, names, and email addresses, the employees could be targeted for social engineering to gain access to more sensitive data.
DataBreaches contacted ShinyHunters to ask whether other Walgreens data contained patient data. He replied that he had verified that there was no patient data before anything was posted, which is consistent with his past policies of not attacking or leaking medical/patient data.
There is clearly a lot of data to go through, and this is just a preliminary report. DataBreaches also asked ShinyHunters whether all of these victims had been contacted previously with ransom demands or if some might first be finding out today. He replied that all had been notified:
All of them have been contacted long ago, they saw the email because I saw them download the samples multiple times. Most of them chose to not disclose and ignore.
It will now literally be leaked on the deadline if they do not engage before then.
Based on the “Comprised On” dates, not all could have been notified “long ago,” as some of these targets appear to have been just hit in September, and some of the dates may not be quite accurate.
The following is the list as listings currently appear on the leak site. Previous coverage of some of these incidents can be found by using the Search function on this site and the entity’s name.
Of course, the main target is Salesforce, Inc. itself. When asked whether ShinyHunters would reveal how much they are demanding from Salesforce, he declined to comment.
DataBreaches has emailed Salesforce to ask if it has any comment on the leak site and if it will be responding at all. DataBreaches also asked whether Salesforce will be notifying all customers of this new development and giving them any advice. No reply was immediately available, but DataBreaches will update this post if a reply is received.
The following entities appear on a leak site by Scattered LAPSUS
Update 1: While no reply has been received as yet, a message from Salesforce to customers was posted by the threat actors on their Telegram channel.
Its funny, these children still seem to think they are untouchable. just watch what happens now kiddies. be seeing you soon.