On November 7, a relatively new user on a hacking forum offered data allegedly from Doctor Alliance for sale. According to the seller, there is 353 GB of data comprising 1,240,640 files. “Contact us on signal to negociate this ransom or all your data will be sold,” the seller warned. The ransom demand was listed as USD $200,000.00, with a deadline of November 21, 2025.
Doctor Alliance is a Texas-headquartered vendor providing services for healthcare providers that include preparing, delivering, and signing documents, verifying that patients are billable, and tracking documents in real-time, integrating with any EHR so that all documents get sent out automatically. As such, it is a business associate and has liability and responsibilities under HIPAA. Covered entities must have a business associate agreement (BAA) in place that specifies the responsibilities of the service provider with respect to privacy and data security.
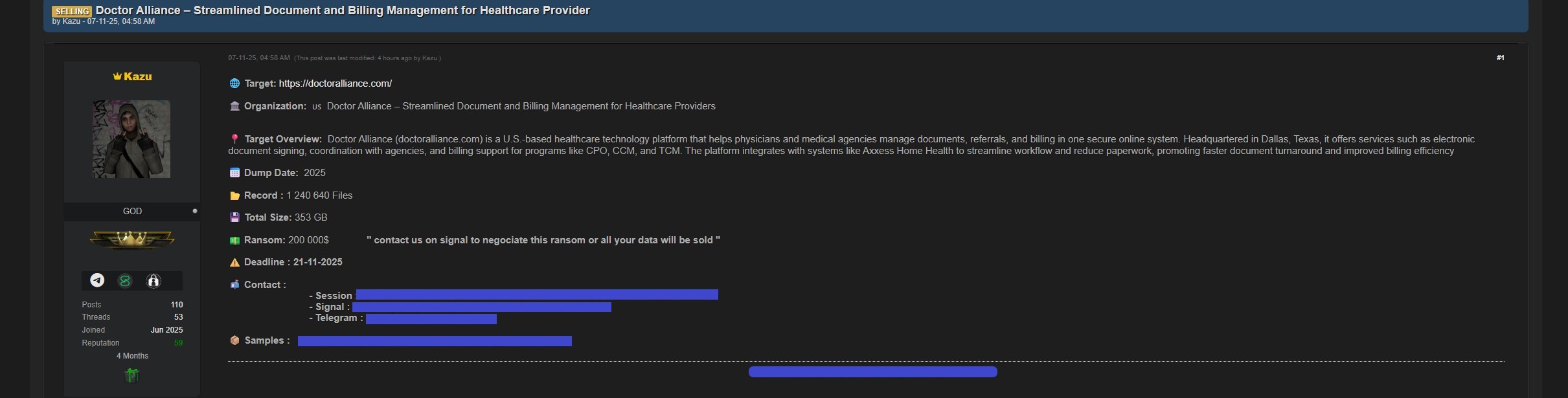 Screengrab of a sales listing for 353 GB of files from DoctorAlliance.com, posted on a hacking-related forum. Image and seller’s contact information redacted by DataBreaches.net.
Screengrab of a sales listing for 353 GB of files from DoctorAlliance.com, posted on a hacking-related forum. Image and seller’s contact information redacted by DataBreaches.net.
The forum listing linked to a sample consisting of a compressed archive of 533 images of patient files. Many of the images appear to be individual pages of scanned files from plans of care. Inspection of the files indicate that they contain significant amounts of sensitive personal and protected health information on patients that include the patient’s name, date of birth, address, phone number, email address, Medicare number, Medical Record number, the patient’s primary and secondary diagnoses, their treatment plans (in detail and with treatment codes), safety measures, medications and dosages, and provider information, with other elements as well.
On November 11, DataBreaches emailed Doctor Alliance to ask if they had confirmed the breach and if this was an incident that involved encryption or was it one involving only exfiltration with a ransom demand.
Doctor Alliance responded that they were not able to confirm from the information they have that this is a legitimate breach, but “If you have samples indicating so, we can comment on those if you share them.” It was not clear from their response whether they were saying that the sample with 533 images was not sufficient to determine if they had been breached or if they had not investigated the sample.
DataBreaches sent them some of the images from the sample, but also reached out to the seller for additional details. As part of an online chat, the seller (“Kazu”) provided DataBreaches with a screenshot purportedly showing access to Doctor Alliance’s network (see screengrab below). A People Search found a person with the same name, address, and month and year of birth in the redacted image.
[Note: Although “Kazu” is a relatively new username on the forum, the individual is not new to hacking and ransom incidents. In the online chat, Kazu informed DataBreaches that he had worked with a number of other individuals and groups over time, but had more recently gone out on his own. He provided DataBreaches with the moniker of one of his former associates.]
DataBreaches sent the access screengrab to Doctor Alliance and also informed Doctor Alliance that this site had been attempting to verify that there were real people at the addresses indicated in the sample of data and had matched a number of the patients’ names, addresses, and ages to people found via people searching using Google, National Public Data, and other online resources. Doctor Alliance did not reply to that email by publication.
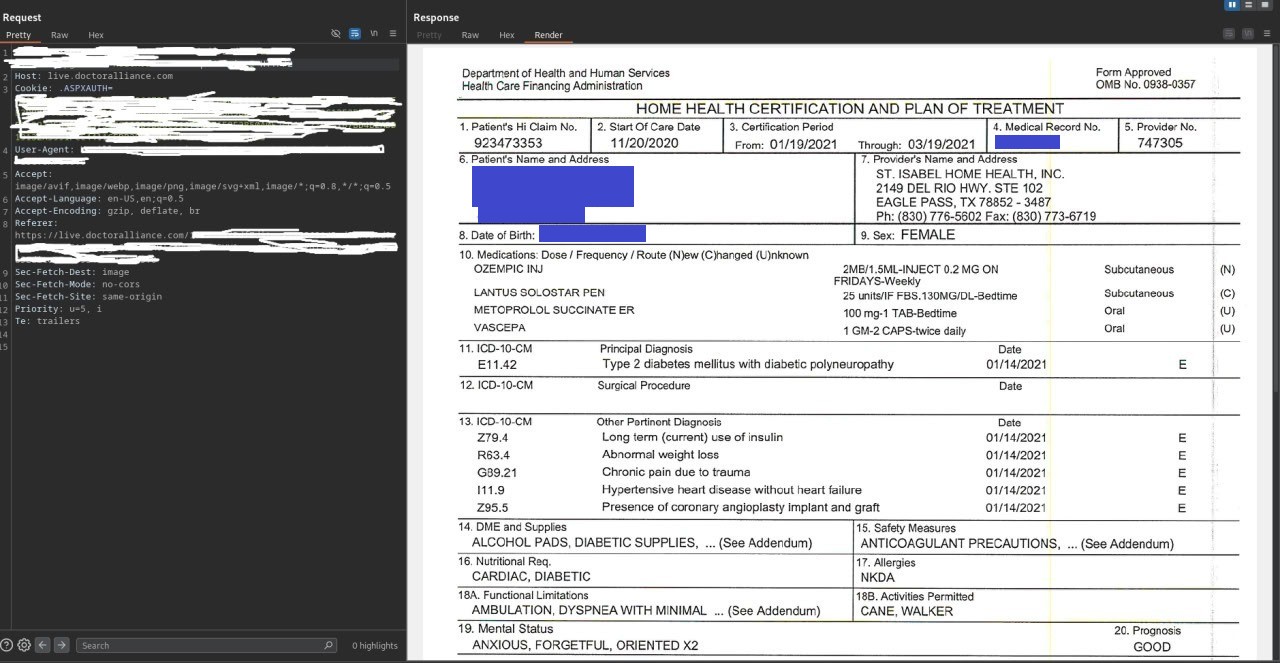
In the second email to Doctor Alliance, DataBreaches also informed them that Kazu claims he first accessed Doctor Alliance in October, but didn’t dump the data until November 4-6, 2025. He informed DataBreaches that he first emailed Doctor Alliance on November 7, but they have not responded to any of the emails sent to them.
Although Kazu declined to be specific about what vulnerability he had exploited, he did tell DataBreaches that he had exploited an older vulnerability that Doctor Alliance had not patched. If Kazu was accurate in the dates he provided to this site, Doctor Alliance had a window of time during which they might have been able to detect the intrusion and avoid the data exfiltration. In response to another question from this site, Kazu stated that Doctor Alliance subsequently patched the vulnerability.
Even without the additional details Kazu provided today to DataBreaches about the firm’s alleged failure to patch a known vulnerability, at least one law firm had already issued a release yesterday seeking potential plaintiffs for a class action lawsuit, and at least one lawsuit against Doctor Alliance and Prima Care (one of their clients) has already been filed in federal court in Texas (Cateon v. Doctor Alliance LLC et al, 3:25-cv-03079-E, Northern District of Texas). Although the case caption is Cateon v. Doctor Alliance, the complaint itself lists Lisa Cucchiello as the named plaintiff. The complaint also erroneously names the defendant as Doctors Alliance LLC. It is Doctor Alliance, LLC. DataBreaches does not know if the named plaintiff even had their data involved in the breach, but is attempting to determine that.
This post may be updated if more information becomes available.