AirAsia Group* pledges to be responsible when gathering personal information and to protect privacy “in every possible way.” That’s not a contract, mind you, but just an expression of their commitment.
On November 11 and 12, AirAsia Group fell victim to a ransomware attack by Daixin Team. The threat actors, who were the topic of a recent CISA alert, informed DataBreaches that they obtained the personal data of 5 million unique passengers and all employees.
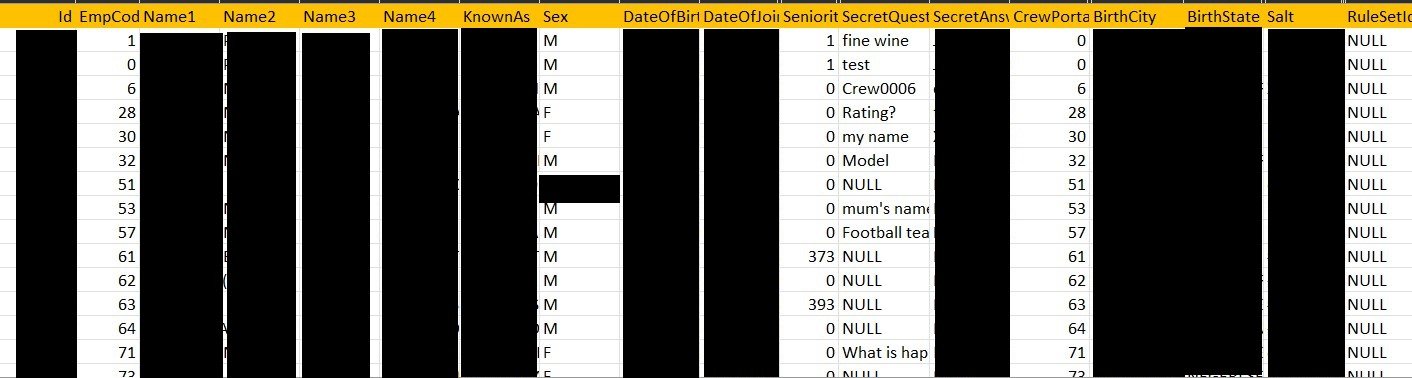
DataBreaches was provided with two .csv files that Daixin Team also provided to AirAsia Group. One file contained information on named passengers. The second file contained employee information with numerous fields that included name, date of birth, country of birth, location, date employment started, their “secret question,” “answer,” and salt.
According to Daixin’s spokesperson, AirAsia responded to the attack. They reportedly entered the chat quickly, asked Daixin’s negotiator for an example of the data, and after receiving the sample, “asked in great detail how we would delete their data in case of payment.” AirAsia reportedly did not try to negotiate the amount, which may indicate that they never had any intention of paying anything. ‘Usually everyone wants to negotiate a smaller amount,” the spokesperson told DataBreaches. DataBreaches does not know how much Daixin Team demanded to provide a decryption key, delete all data they had exfiltrated, and inform AirAsia Group of the vulnerabilities that had been found and exploited.
One point that Daixin’s spokesperson emphasized was that while locking files, the team had avoided locking “XEN, RHEL – hosts of flying equipment (radars, air traffic control and such).” That statement is consistent with statements Daixin Team has made to DataBreaches in other incidents where they have stated their avoidance of encrypting or destroying anything if the result could be life-threatening.
Somewhat surprisingly, Daixin’s spokesperson stated that poor organization on AirAsia Group’s network spared the company further attacks. Although Daixin Team allegedly encrypted a lot of resources and deleted backups, they say that they did not really do as much as they normally might do:
The chaotic organization of the network, the absence of any standards, caused the irritation of the group and a complete unwillingness to repeat the attack.
… The group refused to pick through the garbage for a long time. As our pentester said, “Let the newcomers sort this trash, they have a lot of time.”
DataBreaches cannot think of any other incident this blogger has reported on where threat actors told this site that they actually balked at pursuing an attack because they were irritated by the organization of a network. DataBreaches asked Daixin’s spokesperson if they would confirm that AirAsia’s poor organization really spared the airline from more attacks. The spokesperson responded,
Yes, it helped them. The internal network was configured without any rules and as a result worked very poorly. It seemed that every new system administrator “built his shed next to the old building.” At the same time, the network protection was very, very weak.
Security by incompetence? Could it catch on?
In any event, Daixin informed DataBreaches that in addition to leaking the passenger and employee data on their dedicated leak site, the group plans to make information about the network — “including backdoors” — available privately and freely on hacker forums. “The DAIXIN Team disclaims responsibility for future negative consequences,” they told DataBreaches.
DataBreaches sent email inquiries to AsiaGroup’s data protection officer on yesterday and again this morning, but no reply was received by publication.
Over the past few years, Malaysian entities have often been targets of cyberattacks, as the number of databases and leaks on hacking-related forums or a search of this site attests. AirAsia Group is not the only Malaysian air carrier to suffer a breach. Malaysia Airlines disclosed data security incidents in both 2020 and 2021.
As of January 2022, AirAsia Group became Capital A Berhad, operating as AirAsia. AirAsia is a Malaysian multinational low-cost airline, and the largest airline in Malaysia by fleet size and destinations.
This is a scathing indictment of AirAsia’s sysec protocols and they really need to assess their entire dev SOP.
I hope this press spreads far and wide, if extortion won’t fix their SySec maybe public shaming would.
Doing things half-assed in Malaysia is an institutional way of life here…