Some state and federal laws provide specific timeframes by which breached entities must provide notice to regulators and to those affected by a data breach. Unfortunately, loopholes abound, as we seen in statutory language such as Minnesota’s breach notification law, where for timing of notification, it says: “The disclosure must be made in the most expedient time possible and without unreasonable delay, consistent with any measures necessary to determine the scope of the breach, identify the individuals affected, and restore the reasonable integrity of the data system.”
So if it takes more than a year to figure out whom to notify, you can wind up with a really delayed notification.
In August 2023, Sightpath Medical LLC, a Minnesota entity, notified the Maine Attorney General’s Office of a breach. Their notification, submitted by external counsel, made it appear that a beach affecting 813 people occurred on February 2, 2023, and was discovered on June 14, 2023. Notifications were being sent on August 14, 2023.
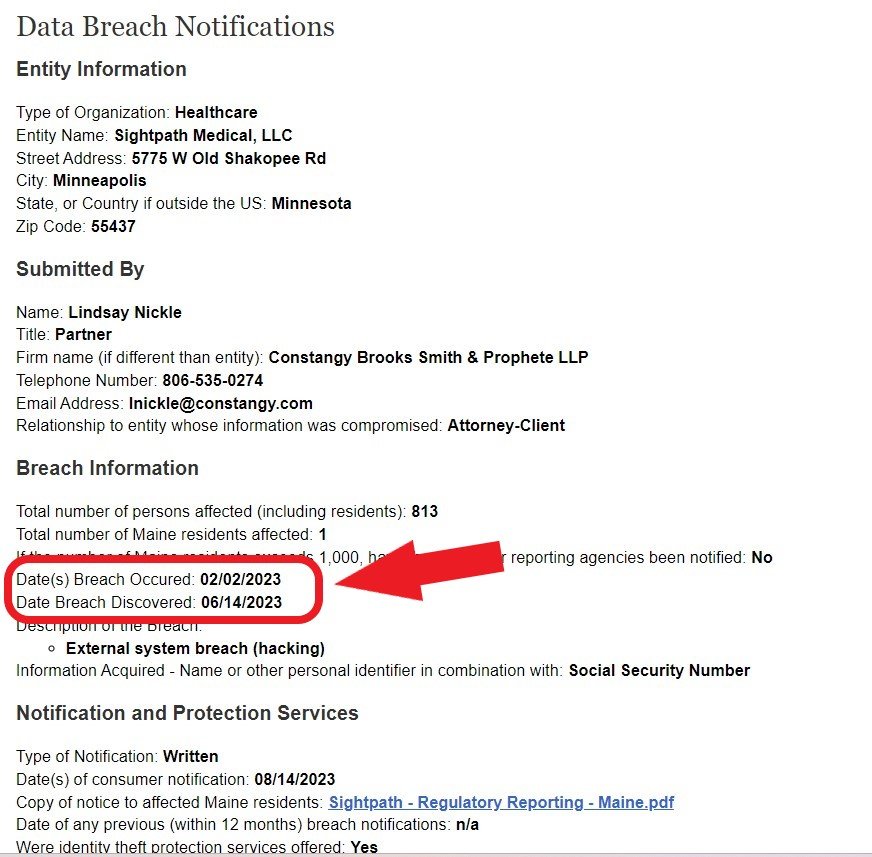
If you believed that information was accurate, then two months after discovery of the breach, notifications were being sent, even though it took four months to first discover the breach. But that information does not appear to be accurate.
If you read the documents submitted to the state for that report, you get a totally different timeframe. According to the notification letter submitted to the state by external counsel, Sightpath first discovered unusual activity in their system on February 9, 2022. The attached letter to those affected also states that the unusual activity was first discovered on February 9, 2022. Those letters are embedded at the bottom of this post.
Was the “February 2, 2023” in the summary entry for the date of the breach a typographical error that really should have been February 9, 2022? If so, that’s a big difference in gap between breach and discovery. But even the date of discovery appeared inaccurate.
In the reporting form, counsel indicated that the breach was discovered on June 14, 2023. According to the attached documents, however, Sightpath completed its investigation on June 14, 2023. It had already known before then that personal information was involved. HIPAA/HITECH is clear that the date of “discovery” is not when an investigation is completed, but when the entity first knew or should reasonably have known that a breach occurred. In other words, the date of discovery is the first day on which a breach of unsecured Protected Health Information is known or, by exercising reasonable diligence would have been known to Covered Entity or Business Associate as defined by 45 CFR §164.404(a)(2) and 45 CFR §164.410(a)(2) of The HIPAA Rules.
Under HIPAA, the 60 day notification deadline should have started ticking when Sightpath first knew it had a breach of unsecured PHI. Under Minnesota law, however, they may have been in compliance because they were trying to determine scope of breach and whom to notify and how.
On September 8, Sutter North Surgery announced an investigation revealed that 861 patients had been affected by an incident. Their statement stated that their vendor, Sightpath, detected abnormal activity on February 9, 2022 and notified them on June 14.
Did Sutter North terminate any contract with Sightpath because it took them more than a year to notify them of a breach detected in early 2022? And if they didn’t terminate their contract, why didn’t they? Does Sutter think that gap between breach and notification is acceptable?
DataBreaches sent Sightpath an inquiry via their contact form. It asked them:
1. Was abnormal activity in your network first discovered on February 9, 2022, as stated in your August letter to the Maine Attorney General’s Office, or was it first discovered in February 2023, as your external counsel reported to that agency via a reporting form? Which year was accurate?
2, When did you *first* discover that any PHI was involved at all?
3. You reported to Maine that 813 were affected, total. Was that for the Sutter North Surgery Center patients or for some other covered entity?
4. If the 2022 initial discovery date was correct, why did it take more than one year to complete any investigation?
5. Are you filing any report with HHS OCR, or are the covered entities all filing their own reports?
No reply has been received.
If the February 2022 date is correct. and if this is a breach covered by HIPAA, maybe HHS OCR should investigate what appears to be a failure to comply with the Breach Notification Rule.
Sightpath - Regulatory Reporting - Maine