Earlier today, AlphV added MeridianLink to their leak site. MeridianLink (MLNK) is the provider of a loan origination system and digital lending platform for financial institutions. AlphV’s listing has been temporarily removed to be updated, but DataBreaches has learned some additional details from someone involved in the attack.
The attack was last Tuesday, November 7. According to AlphV, they did not encrypt any files, but did exfiltrate files. MeridianLink was aware of it the day it happened. According to AlphV, no security upgrades were made following the discovery, but “once we added them to the blog, they have patched the way used to get in,” DataBreaches was told.
DataBreaches asked AlphV whether MeridianLink had contacted them at all or responded to them at all, and was told that someone from MeridianLink had reached out to AlphV at some point, but there has been no interaction between the attackers and the firm. When asked why not, the threat actor explained, “it says they are offline.”
In what may be a first, however, AlphV has seemingly reported its victim to the SEC. A copy of the submission was shared with DataBreaches:
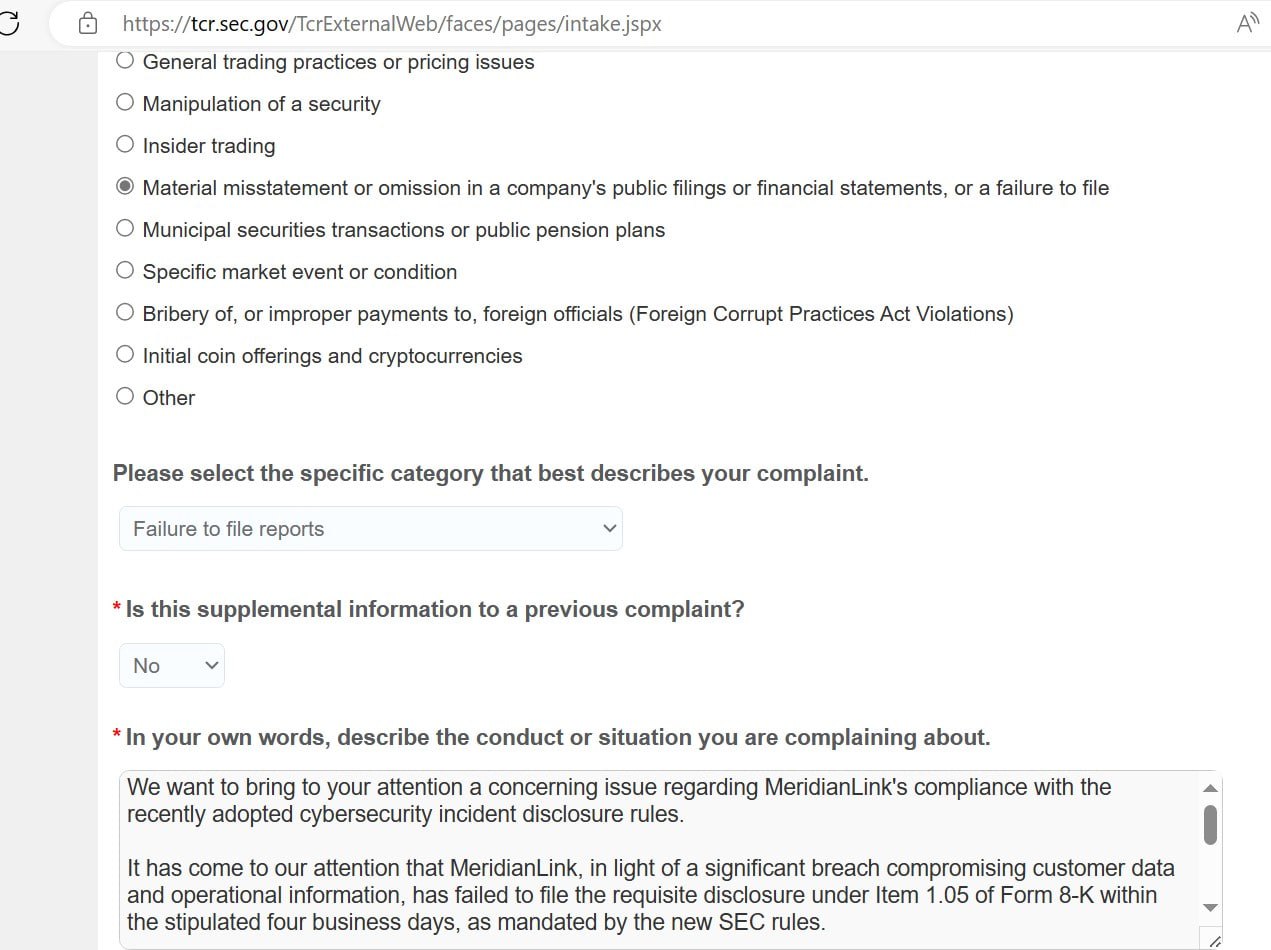
AlphV wrote: “We want to bring to your attention a concerning issue regarding MeridianLink’s compliance with the recently adopted cybersecurity incident disclosure rules.
It has come to our attention that MeridianLink, in light of a significant breach compromising customer data and operational information, has failed to file the requisite disclosure under Item 1.05 of Form 8-K within the stipulated four business days, as mandated by the new SEC rules.
MeridianLink’s data security information can be found on its website. DataBreaches sent an inquiry to MeridianLink asking them about the alleged incident and their incident response. They replied promptly with the following statement:
Safeguarding our customers’ and partners’ information is something we take seriously. MeridianLink recently identified a cybersecurity incident that took place on Nov 10. Upon discovery on the same day, we acted immediately to contain the threat and engaged a team of third-party experts to investigate the incident. Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption.
We have no further details to offer currently, as our investigation is ongoing.
Update 1: This post was updated post-publication to include MeridianLink’s statement.
Update 2: In response to a question DataBreaches received: We are not lawyers, but we believe that new SEC reporting rule doesn’t go into effect until December 15. If any legal authority thinks it is already in effect, please let us know.
Image by wayhomestudio on Freepik.
It is not effective until December 18 2023 for MeridianLink. Even then – the rule is not 4 days from the incident, but 4 days to disclose from the point the company determines they need to disclose it. Companies can’t ‘unreasonably delay’ the determination of if they need to disclose it.
My photos and videos .yzaq ransomware encrypted files so pls help me
How to decrypt all file?
Virus attack date 4.11.2023
This is not my forte, so I asked Brett Callow of Emsisoft, and he suggested you take a look at this thread on BleepingComputer:
https://www.bleepingcomputer.com/forums/t/671473/stop-ransomware-stop-djvu-puma-promo-support-topic/
(and yes, links are not allowed in comments, but I am the owner so I can give myself permission)
Check out this website:
https://www.nomoreransom.org/crypto-sheriff.php
That is also a good site, but in this case, you know from the extension that it’s the newer version of the malware and there’s no decryptor yet.