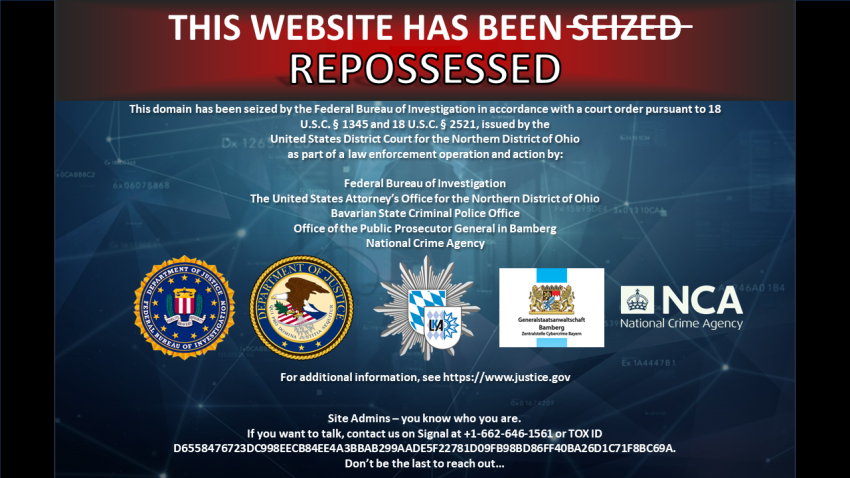
The following takedown and operation relate, in small part, to a leak DataBreaches reported to the FBI and a hosting company. DataBreaches did not name the victim entities or RADAR-DISPOSSESSOR in that blog post to prevent others from finding or misusing the victims’ data. The dispossessor.com website now displays a seizure notice, where the word “seized” is crossed through and replaced with “Repossessed.” A note at the bottom of the notice reads, “Site admins – you know who you are. If you want to talk, contact us on Signal…. or Tox…. Don’t be the last to reach out.”
From the FBI today:
On August 12, FBI Cleveland announced the disruption of “Radar/Dispossessor”—the criminal ransomware group led by the online moniker “Brain”—and the dismantling of three U.S. servers, three United Kingdom servers, 18 German servers, eight U.S.-based criminal domains, and one German-based criminal domain.
Since its inception in August 2023, Radar/Dispossessor has quickly developed into an internationally impactful ransomware group, targeting and attacking small-to-mid-sized businesses and organizations from the production, development, education, healthcare, financial services, and transportation sectors. Originally focused on entities in the United States, the investigation discovered 43 companies as victims of the attacks, from countries including Argentina, Australia, Belgium, Brazil, Honduras, India, Canada, Croatia, Peru, Poland, the United Kingdom, the United Arab Emirates, and Germany. During its investigation, the FBI identified a multitude of websites associated with Brain and his team.
Ransomware is a type of malicious software, or malware, that encrypts data on a computer making it unusable. A malicious cybercriminal holds the data hostage until the ransom is paid. If the ransom is not paid, the victim’s data remains unavailable. Cybercriminals may also pressure victims to pay the ransom by threatening to destroy the victim’s data or to release it to the public.
Radar Ransomware follows the same dual-extortion model as other ransomware variants by exfiltrating victim data to hold for ransom in addition to encrypting victim’s systems. Simply, the ransomware identifies and attacks new victims and, re-victimizes current victims.
Radar/Dispossessor identified vulnerable computer systems, weak passwords, and a lack of two-factor authentication to isolate and attack victim-companies. Once the criminals gained access to the systems, they obtained administrator rights and easily gained access to the files. The actual ransomware was then used for encryption. As a result, the companies could no longer access their own data. Once the company was attacked, if they did not contact the criminal actor, the group would then proactively contact others in the victim company, either through email or phone call. The emails also included links to video platforms on which the previously stolen files had been presented. This was always with the aim of increasing the blackmail pressure and increasing the willingness to pay.
Finally, the compromise was announced by the attackers on a separate leak page and a countdown set until public release of the victim data if no ransom was paid.
As ransomware can have many variants, such as this case, the total number of businesses and organizations affected is yet to be determined. The FBI encourages those with information about Brain or Radar Ransomware—or if their business or organization has been a target or victim of ransomware or currently paying a criminal actor—to contact its Internet Crime Complaint Center at As ransomware can have many variants, such as this case, the total number of businesses and organizations affected is yet to be determined. The FBI encourages those with information about Brain or Radar Ransomware—or if their business or organization has been a target or victim of ransomware or currently paying a criminal actor—to contact its Internet Crime Complaint Center at ic3.gov or 1-800-CALL-FBI. Your identity can remain anonymous. or 1-800-CALL-FBI. Your identity can remain anonymous.
The investigation and joint takedown were conducted in conjunction with the the U.K.’s National Crime Agency, Bamberg Public Prosecutor’s Office, Bavarian State Criminal Police Office (BLKA), and U.S. Attorney’s Office for the Northern District of Ohio.
And from the U.S. Attorney’s Office for the Northern District of Ohio:
The U.S. Attorney’s Office for the Northern District of Ohio filed a complaint against a defendant known as “Brain,” believed to be based in Europe, and who is responsible for building a multi-national ransomware organization known as Radar. The complaint sought injunctive relief to prevent additional attacks on victims from occurring and authorized disruption of the ransomware by disabling domain names, servers and IP addresses associated with the criminal enterprise. Related ransomware domain names and servers in the United Kingdom and Germany were also disabled in a transnational coordinated effort.
Victims include businesses and organizations located in more than three dozen countries throughout the world. Among the victims in the northern district of Ohio were a trade union and a manufacturing company.
The complaint alleges that the defendant developed a highly sophisticated and destructive form of software, known as ransomware, and used it to engage in wire fraud and unlawful interception of electronic communications. This was accomplished by infecting victims’ computers which locked them out from accessing their own files. Ransomware administrators then demanded the victims to pay a ransom in order to unlock the files. Failure to pay the ransom could result in selling the victims’ data to nefarious third parties.
According to the FBI, monetary losses incurred by individuals and organizations are estimated to be in the millions. This is an ongoing investigation and the extent of the reach and damage inflicted is yet to be determined.
This case was investigated by the FBI Cleveland Division; the Bavarian State Criminal Police Office in Germany; the National Crime Agency of the United Kingdom; and the Prosecutor’s Office of Bamberg, Germany.
The case is being handled by Assistant U.S. Attorney Brendan Barker for the Northern District of Ohio.
To report ransomware attacks, visit ic3.gov or call 1-800-CALL-FBI (1-800-2255-324).
This post was updated to add the seizure notice.