On July 9, RansomedVC reappeared, temporarily referring to itself as “RebornVC,” but quickly reverting to its better-known identity.
Its first two victims were listed as SnapAV/Resideo (Snap One) in the U.S. and Unyleya in Brazil. No proof of claims was offered for either listing, and no deadlines were posted, but Snap One had a price of $1 million listed, while Unyleya had a price of $50,000.
Claimed Attack on Snap One
In response to a request from DataBreaches, RansomedVC (RvC) claimed that they had exfiltrated about 50 GB of data from Snap One that included confidential drawings and documents. They provided DataBreaches with five screenshots. One schematic was a diagram for a reference design related to power supplies that has appeared on the internet. Another schematic, however, was stamped “Control4 Corporation” and designated “Proprietary and Confidential.” Control4 merged with SnapAV in 2019 and became Snap One.
Two other files marked confidential and proprietary have been redacted by DataBreaches.net:
 |
 |
SnapOne has not responded to multiple requests for a response to RvC’s claims, but yesterday, after this site gave them a 5 pm deadline to respond for publication, there was suddenly a maintenance note on the site about “scheduled maintenance.”
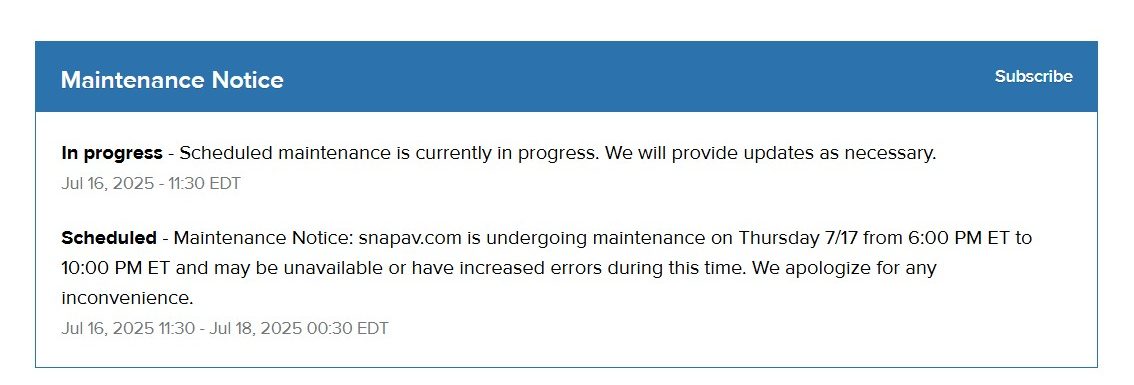
Although Snap One has neither confirmed nor denied any breach, the screenshots and previously unannounced “scheduled maintenance” may be the only confirmation we have at this point. If Snap One ever replies, this post will be updated.
And Then There was a Post About Medusa
Perhaps RvC’s most intriguing post was their third post — now removed — about the Medusa ransomware gang. RvC wrote:
Medusa is a group that first came to prominence in 2023, contrary to what you might believe their business model is quite different from the standard Ransomware as a Service and they operate on a monitored division of subgroups. Lately we have noticed some strange behavior from the admin as confirmed by other affiliates, he seems completely absent and unresponsive to the needs of his members. He recently deleted all groups on the RocketChat server without warning leaving the affiliates with only two plausible reasons: exit scam, admin arrested by authorities. Would you trust Medusa if it were to become active again? Below we have left you an interesting list of current affiliates who participate in the Medusa program, now you know where to repopulate and make lots of money with your skills 😀
What followed was a list of alleged affiliates:
|
|
But it was not just affiliate names. There were screenshots of portions of what appeared to be internal chats with dates in 2022 and 2023. RvC claimed that, “Thanks to our insiders we were able to gather a minimal but interesting amount of historical internal communications between affiliates and their so-called “boss.”
DataBreaches can neither confirm nor refute any of the claimed names or materials, as this site did not attempt to validate the claims. An intel firm or analyst with knowledge of Medusa’s history and affiliates may be able to comment on that. DataBreaches simply notes that going after competitors to try to discredit them is nothing new for RansomedVC. We have seen this type of behavior before.
DataBreaches reached out to Medusa to ask them if they had any comment on RvC’s claims and post, and why they had recently deleted all their data leaks and why RvC claimed their admin had disappeared. They responded on Tox:
I am not disappeared.
We are working
Its a very old data
and also its not us.
no worries
It’s very old data but not them? That requires a follow-up, but they have not been back on Tox to see a follow-up inquiry.
Significantly, however, the entire Medusa listing has been removed from RvC’s site.
Often, when a listing is suddenly removed from a ransomware gang’s leak site, it means that the victim has paid an extortion demand. When RvC was asked why the listing for Medusa was removed, their spokesperson replied, “I am suffering from motivated partial Amnesia, and i cannot recall this to have ever happened.”
More about RansomedVC
DataBreaches has covered RansomedVC under the leader’s various monikers over the past few years (“Impotent,” “Kmeta,” and “RansomedVC.” [A search of this site for those monikers will return additional results.] Looking at the new site, it does not seem like there are any big differences from how RansomedVC used to operate. The group lists its program features and rules on its leak site, but DataBreaches [DD] asked some questions to check:
DD: Reborn appears to be a R-a-a-S model group. What is your policy about attacking the medical sector — hospitals, medical centers, clinics, and physician offices, rehab or addiction facilities, plastic surgery centers, etc.?
RvC: Attacking medical sectors is undoubtedly one of the simplest ways to expand the market, for the same reason on certain critical infrastructures we will adopt only and exclusively the classic exfiltration preventing any critical damage to people or things.
DD: Other groups have made the same claims and then not stuck to their stated rules or done anything when affiliates violated the rules. What will RansomedVC actually do if an affiliate locks a hospital or critical medical entity?
RvC: If an affiliate does not stick to the rules, he will be removed from our affiliate program. We will not allow locking critical infrastructure related to the medical sectors, but we have allowed the attacks to other critical infrastructure, like in the past, for example, pipelines, power supplies and others.
[Note: in further follow-up questions and answers, it became clearer that RansomedVC is prohibiting attacks on hospitals or any medical facility providing emergency medical care where life might be in danger, but they are not prohibiting attacks on medical offices or non-emergency clinics, etc. ]
DD: So if an affiliate locks a critical medical entity, they will be removed as an affiliate, but what, if anything, will you do to help the victim at that point? Can you give them a decryptor or only the affiliate could do that?
RvC: We can decrypt, yes.
DD: The site says you are under new leadership. Who is the new leadership of RvC2 or Reborn?
RvC: The new leadership is Admin, we don’t use monikers.
DD: Why did you target Medusa?
RvC: We specifically targeted Medusa for two reasons, the first one is to warn its own affiliates and second to promote the originality and versatility that our program provides and will provide to newcomers. Our Medusa leak wasn’t particularly done to “steal” affiliates, but rather distinguish our group from others.
DD. There was talk a few months ago about how DragonForce might be trying to head up some kind of “cartel.” Is RvC collaborating with any other groups or interested in becoming part of a “cartel?”
RvC: We’re always open to new collaborations to expand our business and that of others. Our new alliances will be solid and beneficial for all parties involved. To be clear, we don’t want to be part of any cartel for any reason; others will join ours in a few years, or who knows, a few months. We know what we’re doing, and we also know how to influence our competitors.
DD: Can you say something about your ransomware? Are you using something you adapted from existing ransomware, and if so, which?
RvC: No comment.
DD: Can you explain a bit more about your program’s features? Are you actually doing the negotiation for the affiliates?
RvC: We operate primarily as a data broker, but at the same time we can provide everything needed to close operations in the best possible way, this includes the locker, on-call support and much more. We do not carry out the negotiation exclusively, but rather we support the affiliates of the operation to maximize profits, furthermore we are equipped with personnel suitable for the study and meticulous choice the amount to ask. Thanks to our connections we are able to provide media coverage through articles and blog posts to enhance the pressure and with originality is pretty clear, how many groups leak their competitors data?
DD: Seeing “RansomedVC” again may lead some people to think, “Same liar, new lies.” To put it somewhat bluntly: in the past, RansomedVC did not have a great reputation. Jon DiMaggio of Analyst1 wrote a lengthy piece that pointed out the unreliability of RansomedVC’s word. DataBreaches also had that issue when reporting on an alleged Colonial Pipeline incident, where Ransomware kept changing its answers to this site’s questions. Has anything changed since then? If not, why should any affiliate or victim believe RansomedVC now?
RvC: We understand that the past RansomedVC’s reputation wasn’t the greatest, nevertheless we are taking the risk to revive our operations. Why would they believe now? Simply because this new era is under a new leadership and all the victim data we publish will be leaked within a specific period if unable to reach an agreement and this is undoubtedly the best way for researchers to verify that RansomedVC is no longer built on castles of paper, but proven facts. We are also available to answer any request that may make all the interested journalists and cybersecurity researchers change their minds, by proving for example legitimacy of our claims.