Millicom describes itself as a leading provider of fixed and mobile telecommunications services dedicated to markets in Latin America. With headquarters in Luxembourg and Florida, the company is listed on the NASDAQ stock exchange (TIGO). Through Tigo, Tigo Business, and its products and services such as Tigo Music, Tigo Sports, Tigo Money, and ONEtv, Millcom has more than 46 million subscribers.
The multinational firm’s statements about cybersecurity and risk management can be found on its website, as can its reports to the SEC and investors.
What site visitors will not find on the website, however, is any mention of a data breach that allegedly resulted in the exfiltration of 380 million customer-related records.
The Millicom Breach Listing
On November 13, threat actor(s) known as ShinyHunters posted data for sale on a clear net hacking-related forum. DataBreaches had first been made aware of the incident on November 3, but refrained from publishing anything as it seemed that the company was trying to negotiate something, and DataBreaches did not want to interfere with their efforts to protect customer data.
From the listing and from additional details provided to this site by ShinyHunters, the negotiations failed to produce an agreement, and the data were listed for sale with a note to Millicom, “Should’ve paid the ransom ;)”.
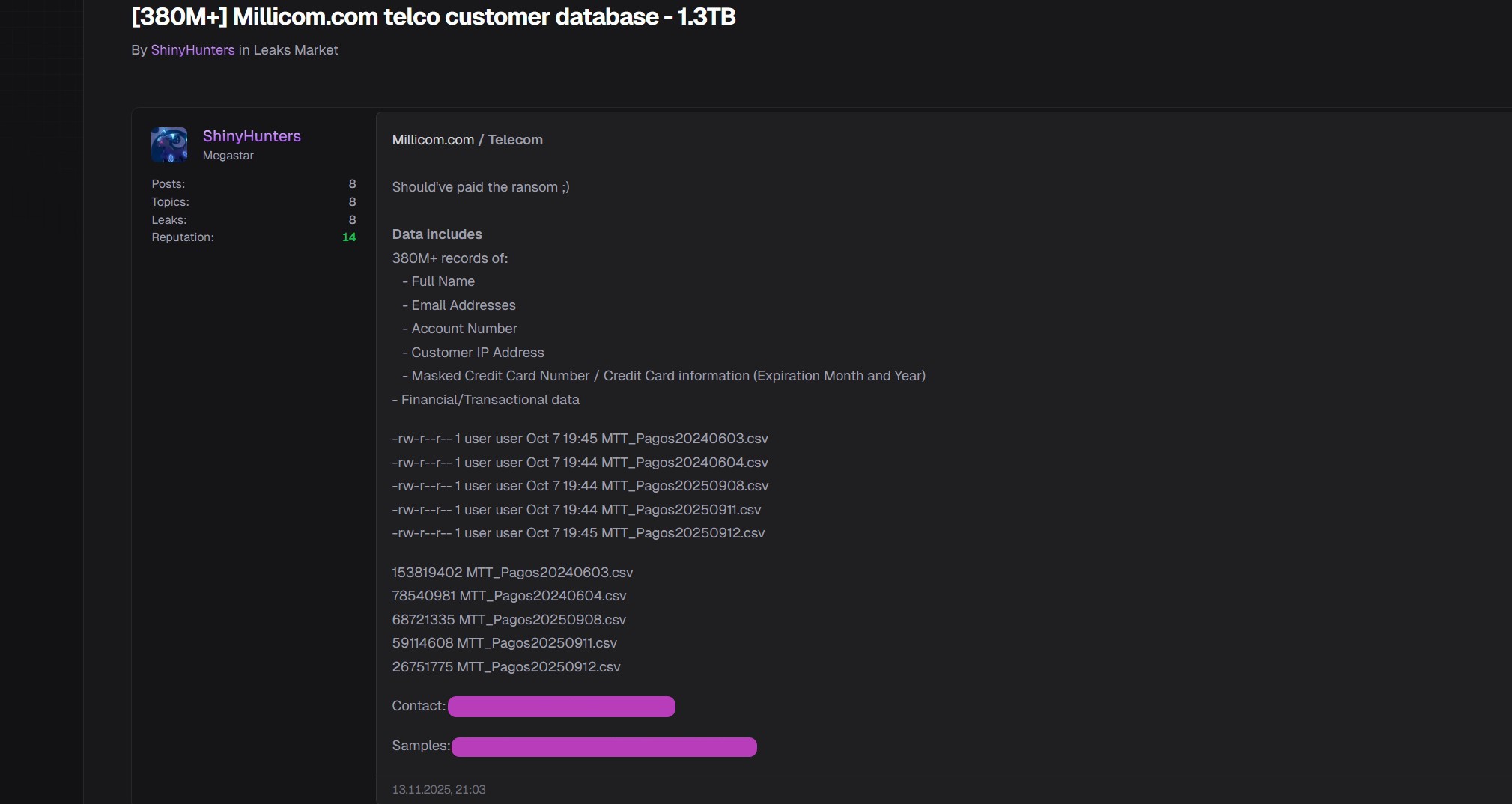
According to the listing, as well as samples provided with the listing, the 380 million records include information that includes customers’
- Full Name
- Email Addresses
- Account Number
- Customer IP Address
- Masked Credit Card Number / Credit Card information (Expiration Month and Year)
- Financial/Transactional data
In online communications between DataBreaches and ShinyHunters, ShinyHunters claimed that Millcom was attacked in mid-September. The attack exploited CVE-2024-2577, which gave the attackers access to AWS credentials and ultimately to database backups stored in AWS S3 buckets.
DataBreaches does not know whether Millicom ever discovered the breach on its own or first learned of it when ShinyHunters contacted them.
Negotiations Fail
Negotiations with Millicom began on November 4. Although DataBreaches did not see the text of any email sent to Millicom, from the contents of the chat log provided to DataBreaches by ShinyHunters, the initial ransom demand was 15 BTC.
There was nothing particularly unusual about the early negotiations. DataBreaches was surprised that Millicom did not request a file tree or directory when they clearly wanted to know about the scope of the breach. But their negotiator did a good job of bringing up a post by DataBreaches that had reported that some PowerSchool clients were getting ransom demands, even after PowerSchool had paid ShinyHunters the ransom. Millicom’s negotiator used that situation to raise doubts about whether ShinyHunter’s word could be trusted.
But the real surprise came after ShinyHunters firmly and repeatedly told Millicom’s negotiator that they absolutely would not accept a payment plan that the negotiator proposed. Millicom simply went ahead and sent them a payment to demonstrate good faith and asked ShinyHunters to accept $10k a month for at least five years, as long as ShinyHunters did not leak the data or take action against Millicom.
ShinyHunters’ response to “emceefr33,” Millicom’s negotiator, was predictable:
[18:05:27] emceefr33: Hello, we have an update for you. We know this may not be what you’d like to hear but we hope that you’d continue work with us as we took the first step to show that we’re acting in good faith here. We just sent you the first payment of approximately 10,000 USD to the BTC wallet you provided us yesterday. We commit to send you every month 10,000 USD for at least 5 years as long as you do not publish our data to anyone or act in bad faith in any way against our company.
Please confirm that you received the funds when you get a chance. We really hope that you change your mind and agree to work with us here. We wanted to show that we will hold on to our promise and send you the funds monthly as long as you agree to work with us.
[19:06:21] shinycorp: We will not accept multiple installments, we made that very very very very clear to you. Yet you ask us for our Bitcoin wallet, suggesting and implying that you will finally resolve this case in a one-time immediate manner, but no, you are acting absolutely foolishly.
If you had no intention of paying us immediately your best decision was to disengage with us and suffer the consequences but instead you, again, without confirming with us or asking us to agree to your terms, send us less than 1% of the money that we do not want in such a manner.
We expect the full amount by the end of this week. Make the right decision.
[19:37:17] shinycorp: We have repeatedly told you we do not accept your offer of multiple installments and you sent us funds that we did not agree to and without our consent. Please provide your BTC address so we can return it and make up your damn mind.
If you truly want to resolve this case and prevent us from leaking your data you WILL pay us the entire agreed upon amount in a one-time immediate transaction.
If you ghost us we will return the approximate 10,000 USD you sent us to the wallet you paid us from and we will proceed with the outlined consequences. You really messed up, this is your last chance. We are not messing around, this is not a game, this is serious, stop acting childish. You have till the end of this week to pay us entirely.
Millicom did not reply, but wrote on November 12:
[20:55:51] emceefr33: The next payment of 10,000 USD is scheduled for December 10th as long as our data and communications are not leaked in any way.
[21:42:43] shinycorp: We have just told you we do not accept this offer. We want an immediate one-time payment. If you can’t do this we will be leaking all your data tomorrow.
On November 13, ShinyHunters listed the data for sale.
DataBreaches has never seen a ransom negotiation where the target just went ahead and sent a payment for a payment plan that the threat actor had firmly and repeatedly refused, so we provided Valery Rieß-Marchive of LeMagIT with the complete chat logs and asked for his comments.
Like DataBreaches, Valery was also surprised at the lack of a request for a full files list, commenting, “It’s surprising that a larger sample is requested, but no full files list. By now, I’d expect anyone negotiating to request such a list.” He was also impressed with how the negotiator used a post of DataBreaches to raise concerns about whether ShinyHunters’ word could be trusted, writing, “Googling the threat actor as suggested, and using against them what’s been found on them seems like a fairly clever move. In a negotiation, you need to find leverage anywhere you can.”
But it was the installment plan proposal that blew his mind, as it blew DataBreaches’ mind. “This installments proposal blows my mind – if really serious. Who, in their right mind, would like to seal a deal so committing for both parties? It seems fairly dangerous to me, on both sides.”
Perhaps Millicom hoped that if they strung out the payments, ShinyHunters would be arrested, and they wouldn’t have to pay as much would recover their data? Was this a way to stall? Or was the payment plan a way to avoid disclosing a breach to investors who might also be considering news this week of a resolution of an unrelated DOJ investigation? DataBreaches would love to know what Millicom thought was likely to happen or why they negotiated as they did.
But the bottom line was that ShinyHunters was demanding $1.3 million USD in one transaction, and all Millicom was offering was $600k spread out over five years.
ShinyHunters’ response was predictable.
Questions for Millicom
Finding no 8-K report to the SEC or any other disclosure, DataBreaches emailed Millicom with questions as to whether the SEC had been notified and whether investors and customers were being notified.
DataBreaches also asked Millicom if they would confirm that there had been negotiations with ShinyHunters as described in the purported chat logs provided to this site, and whether they had sent an unsolicited payment in BTC of $10k to ShinyHunters. DataBreaches was able to find a transaction that matched the information in the chat logs for a November 11 payment, but that is not proof as to who paid it.
There has been no reply from Millicom’s press contact or their investors’ contact. This post will be updated if a reply is received. For now, however, the claims are unconfirmed.
i work for Tigo and I must say my bossess’ bosses are FRUSTRATED, they’ve fired a lot of people very recently because of this.
what exactly are they frustrated about?