This is Part 2 of today’s posts reporting on apps leaking health information. The leaks were shared with DataBreaches.net by researcher Chris Vickery, and this one involves very sensitive health and medical information. Part 1 reported on iFit’s data leak.

Screenshots provided to DataBreaches.net on December 8 by Vickery revealed that 4,926 user accounts from Hzone Dating App for HIV-positive Singles were leaking. The personal information included date of birth, religion, relationship status, country, email address, ethnicity, height, last login IP address, username, orientation, number of children, and password hash. Users can also enter their nicknames, share their political views and sexual life experiences, and post their photo in their profile, as this redacted screencap illustrates:
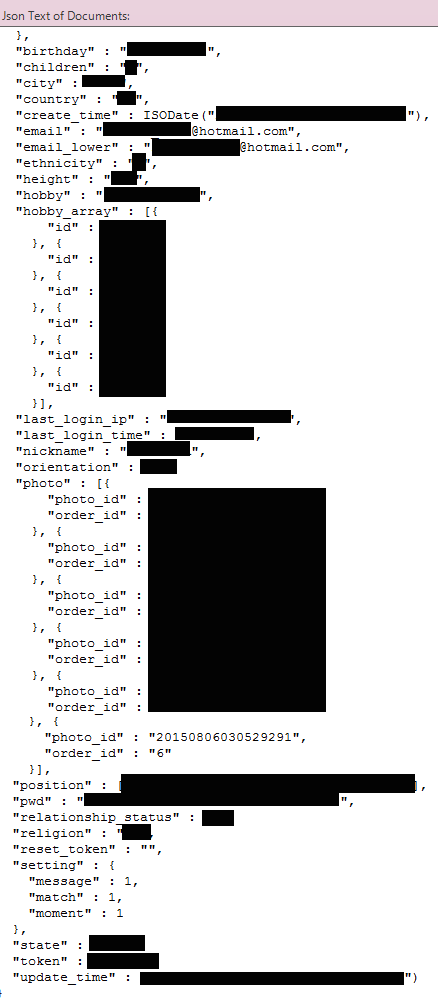
The database also stores messages posted by members. The messages often contain very personal or sensitive information, e.g.,
“Hi. I was diagnosed 3 years ago now. CD4 and Viral Load is relatively good. I’m therefore not on Meds yet. My 6-monthly blood tests are due in June. Planning to go in meds. I’m worried about the side effects. What kinds of side effect have you experienced? Xx”,
While Hzone is a free app, if people subscribe to the premium service, they also provide their name, postal address, phone numbers, and credit card information.
In other words, it’s a leak that could lead to identity theft, extortion demands, or embarrassment.
Five days after multiple initial notifications by this site and Chris Vickery, Hzone’s user information was still leaking.
Indeed, their correspondence, when they finally responded five days after I notified them, was somewhat bizarre, to say the least, and replete with all kinds of accusations.
Because sensitive information was leaking and Hzone was not responding, DataBreaches.net filed an FTC complaint on December 9 and urged them to use their resources to contact the developer to get them to secure their database. FTC did not respond to that request. Apple’s iTune App Store did respond, however, when this site contacted them on December 12 with my concerns when the database continued to leak. Their response did not include immediately pulling the app from the store, however, and days later, they were still reportedly investigating.
As of December 13, 5,027 users’ information was leaking – 100 more people were now at risk than when I first notified Hzone of its leaking database.
The database was (finally) secured last night.
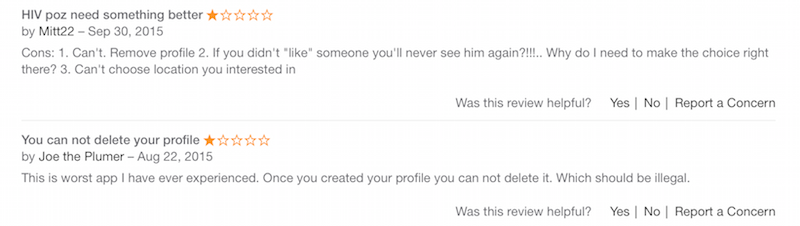
Unfortunately for its users, Hzone does not have a strong tech team, as their spokesperson admitted to DataBreaches.net in e-mail. And users who decide that they do not wish to risk exposure from an app that may not have a great grasp of security appear to be SOL because it seems that Hzone won’t delete profiles. From reviews of Hzone in the iTunes app store:
Hzone’s privacy policy makes no mention of deleting accounts or profiles.
As it routinely does, DataBreaches.net asked Hzone when the leak first began, whether they had audited to determine how many others might have accessed the database, whether they would be notifying their users of the leak, etc. They replied that the leak occurred for no more than one week. “We just re-setup a new system with the server and database and the leaking may caused by that,” a spokesperson informed this site.
Their statement appears to be belied by the fact that a search engine accessed their database anonymously on November 29. So the database was already leaking by then and may have been leaking much earlier.
Hzone’s answer to another question also raises question about their honesty or security auditing. When asked how many people or IP addresses may have accessed the leaking database, they replied, “As far as we can see, you are the only one who have accessed our server and database. No other IP or people login.”
Chris Vickery says that’s a lie, as he used more than one computer and IP address to access the database. So if they claim only one IP address accessed the database, did they really even check or did they check and are covering up? How many other accesses may there have been?
Asked whether Hzone would be notifying its users that their data was exposed, they replied:
No,we didn’t notify them. If you will not publish them out, nobody else would do that, right? And I believe you will not publish them out, right?
So we’ll all just pretend that they didn’t put all their users’ info at risk, right? If they did not properly investigate the leak and/or report their findings honestly, then those sensitive data may have been leaking for quite a while and may have been accessed by others who might misuse the information.
As a side note, the developer had a second app that was leaking in the same way, SugarD. That database was also secured last night after DataBreaches.notified them that it, too, was leaking.
User Beware
If you know someone who might be using Hzone, you might want to point them to this post. While anyone can have a leak or breach, Hzone’s failure to timely respond to notification, the lack of encryption for stored sensitive data, and their refusal to delete profiles when they have inadequate incident response are truly concerning.
Side Note: Over on Salted Hash, Steve Ragan fills readers in on my correspondence with Hzone and how I was initially threatened with HIV infection if I disclosed the leak. Put your coffee or favorite beverage down before reading it.
Not only were you threatened, but your family as well?
Not sure how it is in the States, but here that is a threat of assault, as a minimum.
It’s probably illegal here, too. And if I took it seriously, I might have done something about it. But as I explain in the Privacy Policy on my other site, PogoWasRight.org:
🙂
I send out proactive notifications of breaches all the time. I’d be happy to notify these users that their information may have been compromised if the app admins won’t.
@atechdad
Thanks for the offer, but because health/sensitive info was involved, neither Chris Vickery nor I downloaded the user data. If Hzone doesn’t notify their users, though, I hope tweets and other media sites reporting on the leak will help get the word out. I actually thought of downloading Hzone so I could enter a customer review on App Store to alert people.