Vendor’s error appears to have exposed personal and confidential medical data of patients seen at Bronx-Lebanon Hospital Center since 2014;
Records also include addiction histories, psych histories, and histories of physical or sexual abuse;
Hospital investigating to determine what happened and who may have accessed data.
By now, you may be tired of reading reports on misconfigured MongoDB installations or rsync backups. If it’s any consolation, I’m tired of reporting on all these leaky and/or misconfigured installations, but … they’re still happening. It’s almost as if no one is listening to any of the researchers begging entities to secure their data. How many MongoDB servers have to be totally wiped out or ransomed before more people start checking whether they left port 27017 open? How many more nude photos of patients or ultrasound images will be exposed because of misconfigured Rsync backups? And of course, if the government hadn’t thrown researcher Justin Shafer in jail on cyberstalking charges, he’d probably still be uncovering firms and covered entities that expose what should be protected health information on public FTP servers.
But as concerning as the PII leaks of patient data are, the ones with sensitive protected health information are even more concerning to this blogger.

On May 3, Bob Diachenko of the Kromtech (MacKeeper) Security Research Center contacted me after finding what appeared to them to be tens of thousands or even millions of patients’ records exposed due to yet another misconfigured rsync backup. At Bob’s request, after reviewing some of the data he sent me, I agreed to assist him with trying to make notifications. Inspection of the data had suggested that the backup was managed by iHealth Innovations, but that the patient records were from Bronx-Lebanon Hospital Center in New York City.

Unable to reach anyone at iHealth Innovations other than their switchboard, with whom I left a message, I attempted to notify the hospital, while Kromtech also attempted to make notifications. I cannot say that notification to the hospital was quick or easy, but within an hour or so, the data were secured, and by the next day, I had received three call-backs from the hospital and the vendor. Both thanked me for alerting them to the problem and promised to get back to me with some explanation or answers to my questions.
Neither followed up as promised, however. A hospital spokesperson did return my call yesterday, and asked me what my questions were. Then he didn’t answer any of them, telling me only that they were investigating and would have no further comment at this time. The hospital wouldn’t even answer a basic question such as “Why does iHealth Innovations have all this patient data? What does iHealth do for the hospital?” Neither did iHealth Innovations follow up despite their assurances.
So no, we didn’t get to the question of whether any business associate agreement was in place and how the hospital evaluated their vendor’s data security or whether the vendor even needed all that personal and confidential medical information to do its job for the hospital. The data that Kromtech sent me appeared to be from 2014 and 2015 but a listing of the directories and folders indicates that the exposed backup also contained records from 2016 and 2017.
As noted previously, the records contained a lot of sensitive medical information in addition to personally identifiable information such as name, address, telephone number, date of birth, Social Security number, etc. Here are two redacted snippets, below. The lines giving the patients’ names and other details have been cropped and other details are redacted. Some may be shocked by the amount of detail in the records, which is precisely why I am posting redacted snippets: imagine if these records were yours or a family member’s. Do you really want all these hospital records exposed on the internet because of a vendor’s error? Do you even want a vendor to have all this sensitive information?
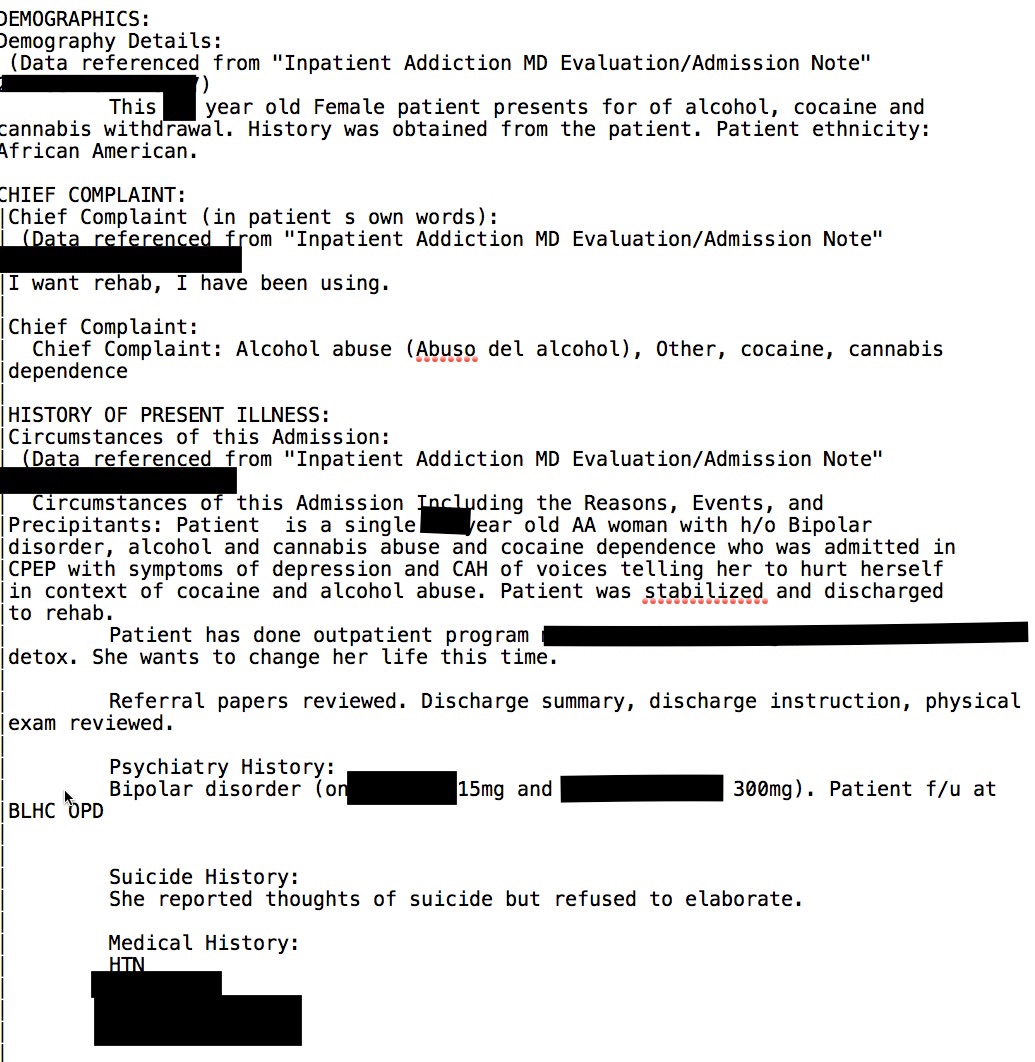
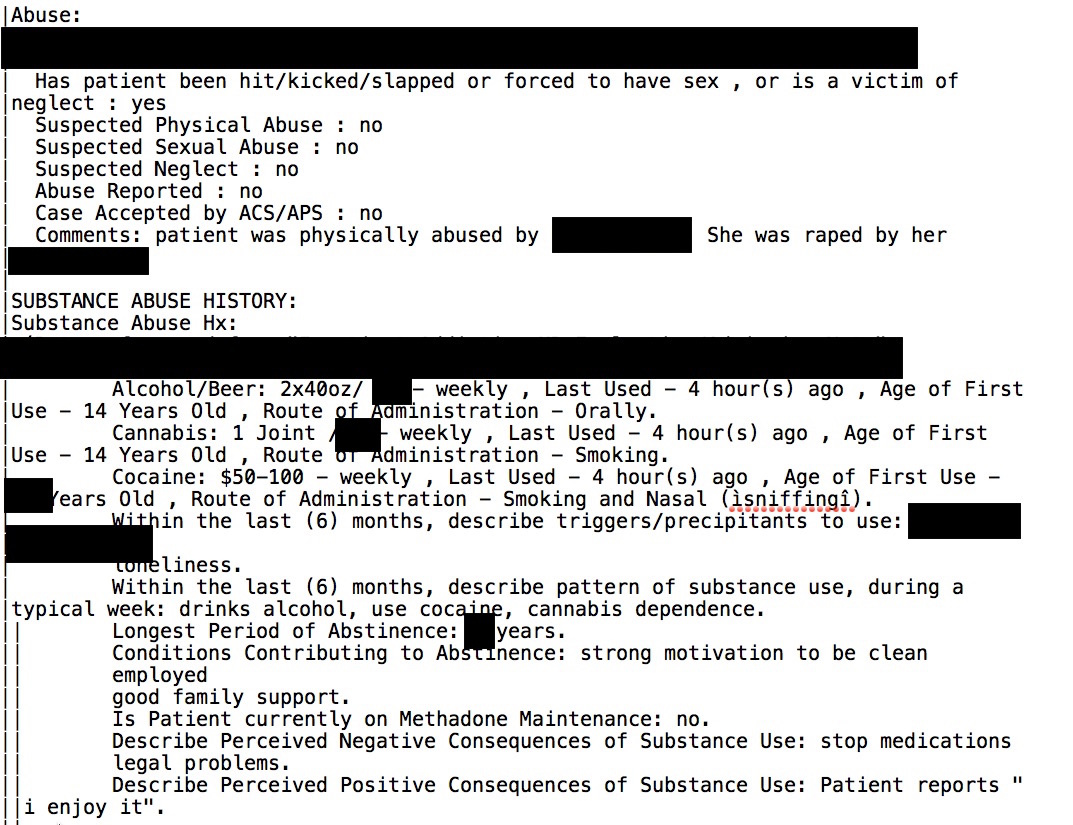
The preceding redacted snippets are from files in the Addiction unit. According to what Diachenko found via a Shodan search, and you can read his report here, records and files from a number of departments were publicly accessible and viewable, including cardiology, surgery, pulmonology, psychiatry, and neurosurgery.
At the present time, DataBreaches.net does not know if anyone other than Kromtech’s research team accessed these medical records and other personal data. Nor does DataBreaches.net have a clear sense as to many unique patients’ records were involved, although Diachenko indicates it could be tens of thousands to millions. Whether the hospital or vendor will notify HHS or any regulators or patients remains to be seen.
This post will be updated if or when the hospital or vendor provide additional information.
You’re right, the amount of detail is horrifying. I’m guessing they won’t talk to you because they are busy hiring lawyers and PR experts who will issue the standard announcement: “Information technology policies were not adhered to… remedial action will be taken… updating security policies… offering subscription to a credit monitoring service.”
As of 5/13/2017, Bronx Lebanon hospital (Bronx NY) was hit with another cyber attack and our whole system was affected and still is affected.
Are you referring to the Wanna Cry ransomware attack?
Bronx Lebanon was hit and so was lots of other hospitals