On December 6, Catalin Cimpanu of ZDNet reported that both BMW and Hyundai had reportedly been hacked. His report was based on reporting by Von Hakan Tanriverdi and Josef Streule that had been published on both BR.de and taggeschau.de. Their report was light on details, though, and neither BMW nor Hyundai would comment. to them or to ZDNet. Indeed, when it came to Hyundai, all the German publications’ reporters noted was that the attack involved some fake website.
For reasons that are not clear to me but may have been lost in translation, the reporters attributed the attacks to the threat actors known as Ocean Lotus or APT32, a group suspected of attacking entities on behalf of the Vietnamese government. The group has previously been linked to other attacks on automotive companies.
Whether the reported hack on Hyundai was the work of APT32 or not, on December 7, DataBreaches.net was contacted by an individual who claimed to have hacked Hyundai. It made for an initially confusing interview, because this blogger incorrectly assumed he was referring to the incident reported by ZDNet. But one of the first things this hacker claimed was that he was NOT APT 32 and he was not a group — he was an individual — a greyhat hacker working as an individual.
Well, if he was a state actor, we would expect him to lie, right? But over the next few hours, it became clearer that what he was describing probably was either a second and unrelated hack of Hyundai or the initial reporting may have been wrong. Then again, maybe this site was just being gamed.
“DarkSly,” as he prefers to be called, first tweeted about hacking Hyundai in mid-November:
more details for leaked data from @hyundaisaudi
about 460K customer details from saudi arabia and iraq@Hyundai @Hyundai_Global @Hyundai_KSA https://t.co/IVSUEQFcOo pic.twitter.com/uwf5vE5wZZ— DarkSly (@notify91557898) November 14, 2019
According to statements made to this site, DarkSly wanted a bug bounty of 1 BTC to inform Hyundai Saudi Arabia of its vulnerability, fix it for them, and wipe out all the data he had downloaded, but after an initial response by one of the Twitter accounts, they blocked him and then just didn’t respond to him any further.
lol
their reaction @Hyundai @Hyundai_Global @hyundaisaudi https://t.co/VoFRezNKfO pic.twitter.com/arZL3ouDMm— DarkSly (@notify91557898) November 13, 2019
So what kind of data does Darksly possess? He claims to have approximately 550,000 user records with many records including full name, email address, city, bank, monthly salary, cellphone number and some other details. The data also reportedly include details of approximately 14,000 Iraqi customers. Neither passwords nor credit card numbers were reportedly stored in the databases.

DarkSly also claims that the last time he tried to access their server — a few days ago — he still had access. But even if he loses access, he’s not particularly concerned about regaining access: “I actually have their source code and can find other ways since development looks so weak.”
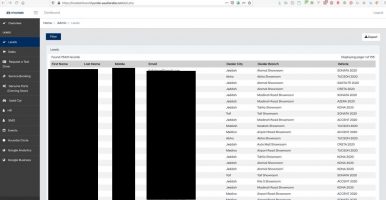
DataBreaches.net contacted Hyundai’s corporate headquarters to ask for clarification or confirmation as to whether they have experienced one hack or two, and whether they had any comments. No response has been received. DataBreaches.net also sent emails to the first 9 customers listed in one of the unredacted screenshots DarkSly provided to ask them whether they had purchased the model listed next to their name. One of the emails bounced back that there was no such user. The other 8 emails did not bounce back, but none of the recipients replied.
So what will he do next? DarkSly informed DataBreaches.net that he may post a video of the attack, which he recorded, and/or he may sell their data.
And now, a Developing Story:
Yesterday, DarkSly posted some other data involving Jaguar and LandRover:
any idea??
saudi arabia, Kuwait, uae, oman, egypt, mexico, Morocco, Lebanon, Iraq, qatar and Tunisia branches involved, all databases backed up. pic.twitter.com/M6avp4Aozj
— DarkSly (@notify91557898) December 8, 2019
The tweet with screenshots apparently showing access to their server was subsequently removed.
According to DarkSly, he hacked Jaguar and LandRover yesterday in about three hours. At the time of his initial announcement, he had not contacted either manufacturer or any dealers. When asked whether he was targeting Saudi Arabia, he responded that he just woke up and decided to target a big company. He was still working on the mynaghi group (Hyundai) attack, and landed up at Jaguar and LandRover, he claims.
“having fun with big shots,” he wrote to DataBreaches.net.