On January 3, the U.S. announced the successful assassination of Qasem Soleimani, Iran’s top general. Dire warnings about retaliation immediately appeared in the news, and it wasn’t long before we began to see headlines claiming that Iran had launched cyberattacks on the U.S. But were these really state actors or sophisticated actors, or or were these just a bunch of kids, skids, or hacktivists?
In the past two weeks, we have seen the re-emergence of old hacking accounts, the emergence of new accounts using old templates for defacement or updated templates, and attacks on a variety of entities, not all of which have anything to do with the U.S. government.
The following is a chronology of attacks based on published sources as well as archived defacements. We have annotated entries with a bit of information on the threat actors when any information was available, but we note the obvious that statements made by threat actors are not highly likely to be truthful or accurate.
January 3rd, 2020:
– Qasem Soleimani killed in a targeted drone attack in Baghdad, Iraq.
January 4th, 2020:
Threat actor “Iran_Cyber” breaches and defaces fdlp.gov, a U.S. government website. Social media immediately over-reacts claiming it was a state-sponsored attack.
Our research showed that Iran_Cyber appeared to be a reused/recycled name. Whoever was recycling the name, however, had altered it slightly from Iran-Cyber to Iran_Cyber. The original Iran-Cyber had stopped defacing sites in 2019, and had used a somewhat different template for defacing sites.



January 4 – 5, 2020:
A threat actor using the name “Shield Iran” begins defacing small businesses’ and organizations’ websites with a picture of Soleimani.

Shield Iran targets that day included the South Alabama Veterans Council and the Sierra Leone National Bank, a bank that is hosted on a U.S. server. The bank, attacked on January 5, was offline for approximately two days. The SAVC was still offline on January 16.
January 5, 2020:
A YouTube account hashtagged #Anonymous #Iran published a video, “Anonymous warning to American citizens about Iran. The video has had more than 37,000 views to date.
January 6, 2020:
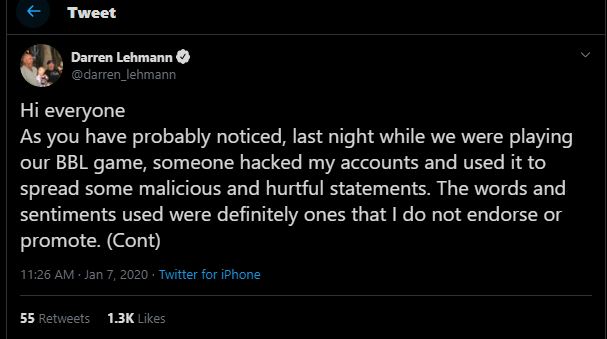
The Twitter account o ex-Australian cricket coach, Darren Lehmann’s, is hijacked and used to spread hate messages and abuse. Lehmann’s profile was also changed to a discord. Monitoring the discord revealed that those involved were based in Australia and were doing it for laughs (“the lulz”) in a targeted attack against Lehmann.

Lehmann was reportedly so distraught over the incident that on January 7, he announced he was taking a break from social media.
Hi everyone
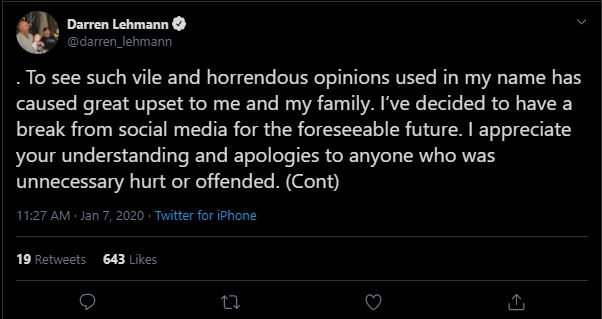
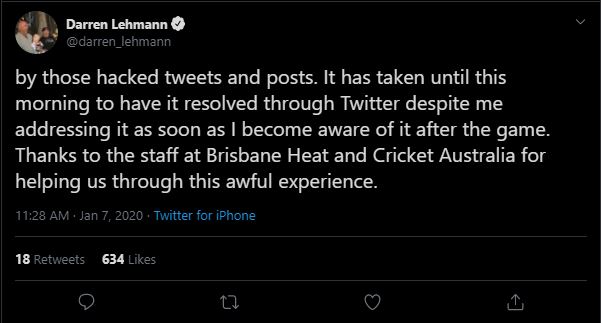
As you have probably noticed, last night while we were playing our BBL game, someone hacked my accounts and used it to spread some malicious and hurtful statements. The words and sentiments used were definitely ones that I do not endorse or promote.To see such vile and horrendous opinions used in my name caused great upset to me and my family. I’ve decided to have a break from social media for the foreseeable future. I appreciate your understanding and apologies to anyone who was unnecessary hurt or offended by those hacked tweets and posts. It has taken until this morning to have it resolved through Twitter despite me addressing it as soon as I became aware of it after the game.
Thanks to the staff at Brisbane Head and Cricket Australia for helping us through this awful experience.
January 6, 2020:
The Anonymous Iran account on Facebook suddenly becomes a lot more active again. The account, which opened in 2015, has less than 3,000 followers.
January 7, 2020:
A threat actor using the handle MrB3hz4d (MrBehzad?) changed the defacement template they had been using on January 3, 2020 to include a slogan in support of Soleimani: “Suleimani was not a person/he was a belief/Beliefs never die”.

The original defacement still stated “Down with America” and was tagged with “Iranian Hackers.” The defacements are still occurring, but they vary, with some defacements involving sites in Vietnam, and some of the defacements appearing to be very low-level defacements (such as one on a GoDaddy website builder website), which begs the questions as to whether these defacers are skids or just kids with as-yet underdeveloped skills.
January 7, 2020:
Threat actor “lulzkid,” using the tag #theloserteam, managed to pull off what appeared to be a breach and defacement of the Texas Department of Agriculture website. This was later confirmed by the state, but no data were reportedly exposed or exfiltrated, leaving us to wonder whether this may have been a DNS-related attack. #TheLoserTeam team has been doing very minor text-based defacements for a short time since the end of last year. They have also recently been targeting Indonesian-based websites with absolutely no real link to anything dedicated to America, leaving us yet again with one more low-level actor making a lot of noise.

January 8, 2020:
Some users on social media start to urge Iran to hack Trump and the United States.
Could they hack the IRS and obtain Trump’s tax returns… asking for a friend.

Iran “If you’re listening… you know that plan to hack IRS for Trump’s tax returns………”
Now hack the IRS website for Trump’s tax returns!
January 8, 2020:
A false news article appears on Twitter claiming that Iran has successfully hacked the IRS and obtained Trump’s tax returns. It is met with great glee in some quarters.
January 8, 2020:
Kuwait news agency claims to have been breached and a false article posted.

January 9 , 2020:
The Governor of Texas, Greg Abbott, announces on Twitter that attempted cyber attacks from Iran against Texas agency websites are occurring at a rate of about 10,000 per minute. Most people fail to read the rest of the story which explains that that’s a typical day. Subsequent media reports clarify that also that has become fairly typical, Iran may — or may not — have escalated recently. It turns out no one really had hard numbers that they could use to compare.
January 9, 2020:
A dentist who provides help to patients in Africa learned that his site was defaced. “Mr Behzad” of Iran Shield claims credit for the defacement, telling a news site that he is a 19-year-old operating out of a sense of patriotism.
January 10, 2020:
Threat actors claiming to be Anonymous Iran breached the City of Ozark’s website and leave a message: “we love your country but we hate your president.”
January 15, 2020:
Israeli news live publishes a YouTube video that begins to circulate titled “Did the US or Israel Hack Iran Air Defenses Taking Down Flight 752?”
The video was shared and viewed by 18,000 people in its first day.
January 16, 2020:
The South Alabama Veterans Council remains offline after being defaced by by Shield Iran on January 5.
![]()
January 17, 2020:
Actor OP999, who began defacing Iranian government and non-goverment websites on January 13, uploads 70 defacement records to zone-h. Many are the result of mass-defacements and are not top-level defacements.

The defacement message used on January 13, seen below, appear somewhat different than defacements after the January 17, with the more recent defacements omitting any references to Iran or Soleimani.
Defacement message of January 13 (translated)
This is a serious warning to all government, political and military officials of the Islamic Republic.
You have been involved in systematic lies, widespread corruption and crimes against Iranian citizens and other people around the world for the past five years.
Know and be aware that Yoom-in is far closer than you can imagine to respond to your evil deeds.
It will not take long for you to sit in the courts of justice in the courts of punishment and punishment, and then you will have to pay for all these years of oppression and oppression.
Know that your resistance to this issue will bring you no fate other than the one of Qassim Suleimani.
# OP999, T-117, Want3d, Cr0x, NI9
What to take away from this?
If there is anything to take from this, it is that first, we shouldn’t hype low-level defacements as being state-sponsored attacks. While Iran may be capable of such attacks, there was no indication any of the cyberattacks we have learned about since January 3 are likely a state-sponsored attack.
Second, as low-level as defacements and hijacking Twitter accounts may seem, we need to remain cognizant that even defacements can result in small businesses suffering a major loss if they do not have the resources to quickly restore their site’s appearance and functionality.
Research by Lee J. Reporting by Lee J. and Dissent.