GETTR, a social media platform similar to Twitter but frequented by people who don’t feel welcome on Twitter, officially launched on July 4th, 2021. It may be hard to remember what came first — the official launch of the platform run by former President Trump’s ex-spokesman Jason Miller or its first data breach, which was also announced on July 4.
Jason Miller’s new right-wing social media site “Gettr” was hacked this morning. pic.twitter.com/cncddw9RZ9
— Zachary Petrizzo (@ZTPetrizzo) July 4, 2021
A hacker calling themself @JubaBaghdad subsequently dumped a database claiming that it contained a scrape of thousands of GETTR’s users. Hackread.com confirmed that the dump included users’ status, location, usernames, date of birth, and email addresses. “After removing duplicates; the database contains the email addresses of 76,382 GETTR users. However, no passwords were scraped or dumped in this data leak,” Hackread reported.
As Insider reported at the time, @JubaBaghdad did not disclose his method but said it was easy to hack them and that there were other bugs. And although Miller claimed that the problem was detected and fixed within minutes, Insider noted that the platform was off to a “bumpy start:”
GETTR was flooded with pornographic images and GIFs on Saturday, Insider reported. Users spammed the platform’s first post with graphic hentai videos and images of Hillary Clinton’s face photoshopped onto a woman’s naked body, Mother Jones reported.
GETTR’s privacy policy states, in part:
Data Security
We have implemented measures designed to secure your PI from accidental loss and from unauthorized access, use, alteration, and disclosure. All information you provide to us is stored on our secure servers behind firewalls. Any payment transactions and PI will be encrypted using SSL technology.
They then attempt to cover their corporate tuchus with a disclaimer:
Unfortunately, the transmission of information via the internet is not completely secure. Although we do our best to protect your PI, we cannot guarantee the security of your PI transmitted through the Website or Apps. Any transmission of PI is at your own risk. We are not responsible for circumvention of any privacy settings or security measures contained on the Website or Apps.
But have they really done their best? And aren’t they responsible for insecurely configured databases and logs?
GETTR is leaking user data, and hasn’t responded to three attempts at responsible disclosure. Read on…
GETTR is Leaking
On August 25, DataBreaches.net was alerted to the leak by Twitter user @pompompur_in, who had discovered two GETTR-related leaks by searching Shodan.
“I was randomly looking up stuff on Shodan and came across an instance where GETTR has left a database UI page open and I can see some API logs,” he explained. “IP Addresses, usernames, what people are searching // viewing,” he added.
Minutes later, he reported finding another instance, but it was a dev instance, he noted.
The dev instance contained more personal information on users, including messages, users’ email addresses, and administrator actions such as who was being banned, etc. To make things even more of a face-palm, the developer’s instance had been attacked and ransomed by a MongoDB bot that left a “READ_ME_TO_RECOVER_YOUR_DATA” message.
DataBreaches.net reached out to GETTR on August 25 and provided the urls of the exposed data and screencaps.
Getting no response, this site reached out to their Twitter team, with similar unsuccessful results.
On August 28, DataBreaches.net emailed GETTR’s privacy@ email one more time (there was nothing on their site that indicated where/how to report a bug or security issue — even after their first embarrassing incident).
At this point, then, GETTR users might want to assume that at least some of their personal information is exposed and may remain exposed — or scraped by others.
Here are just two of the screencaps demonstrating the leak that were provided to this site by @Pompompur_in. They have been redacted by DataBreaches.net for what might be real names and email addresses. This site has left exposed comments and blocks, however, with one exception that struck me as so offensive/racist/antisemitic that it was redacted it, too.
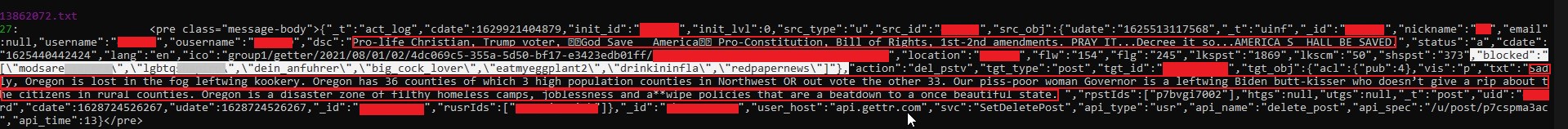
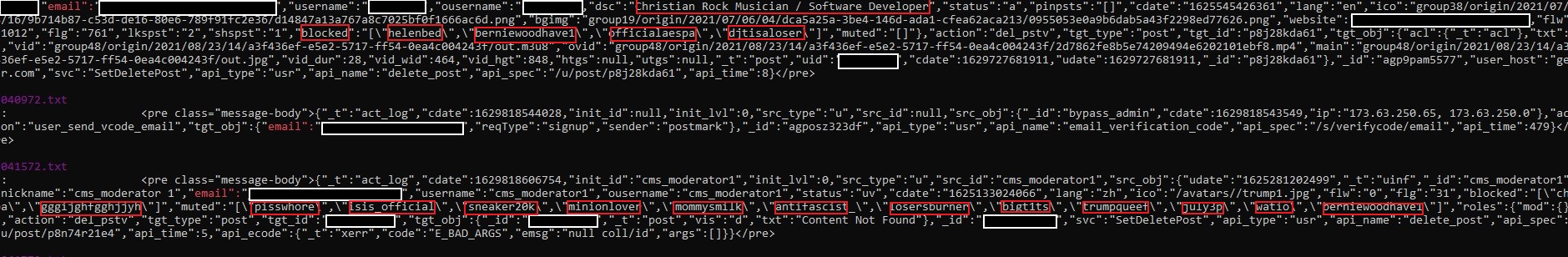
Comment:
DataBreaches.net realizes there will be some who may criticize this site for not waiting longer to report this — and for not giving GETTR more time. Given that GETTR is of significant political interest to many, this site doesn’t doubt that these leaks may have already been discovered by others who may be collecting the personal information for future use or misuse. This site has therefore made the decision to report quickly so that GETTR users can protect themselves when GETTR isn’t protecting them.